Hey folks,
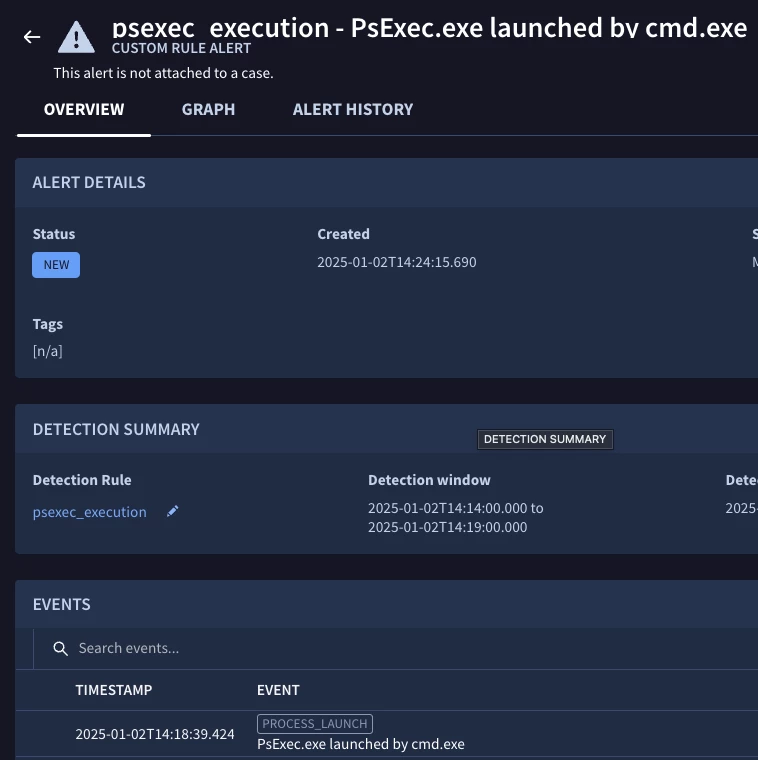
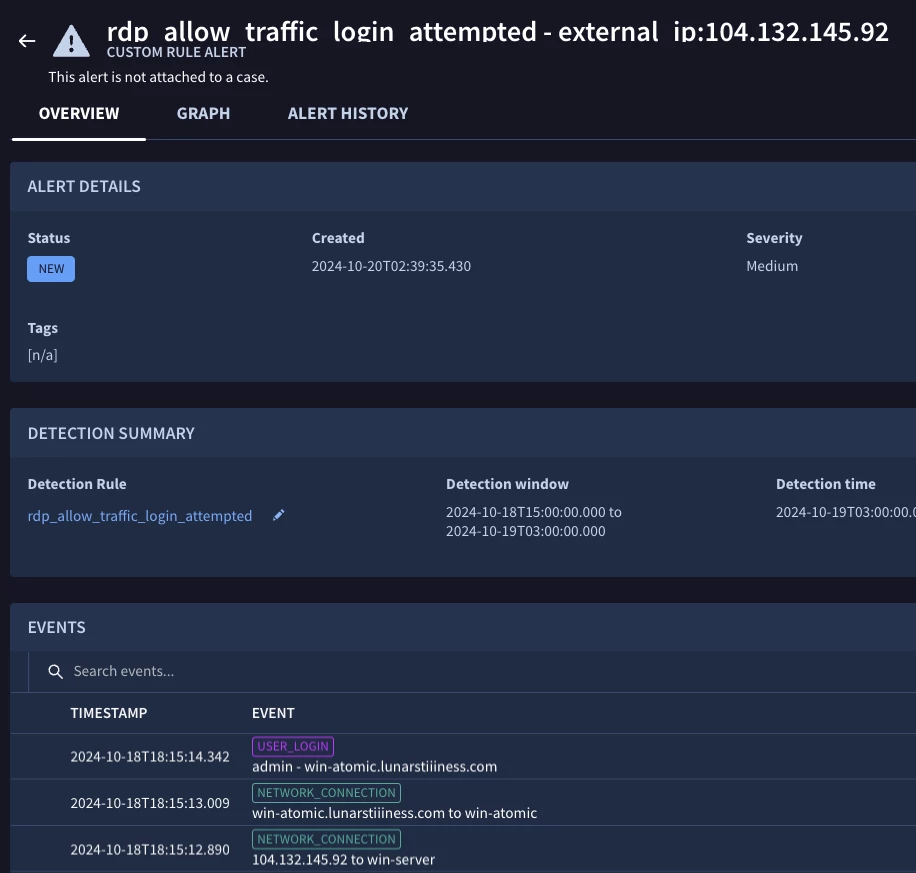
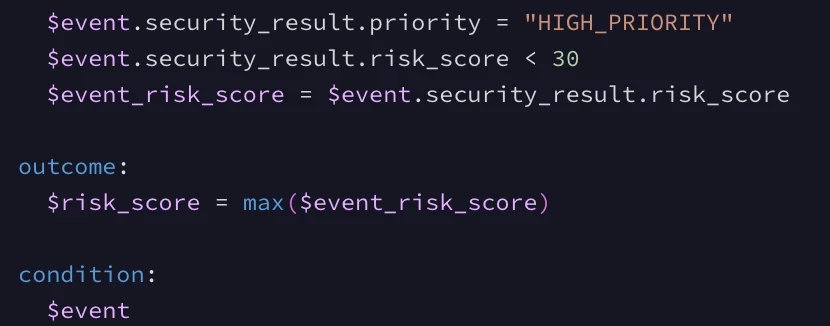
I have a rule that generates alerts if some log matches the conditions mentioned in the rule. However, when the alert is generated, it shows the name "[n/a]", as mentioned in the screenshot.
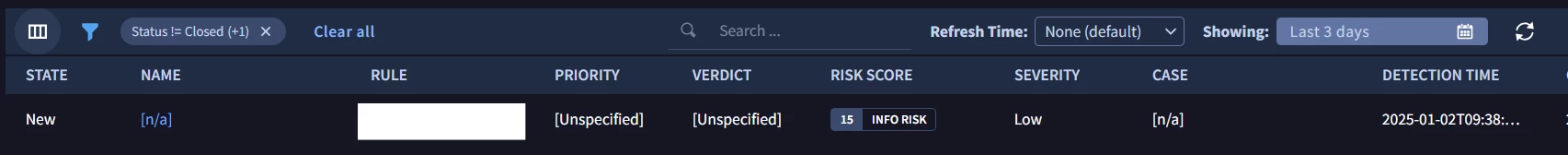
Can someone explain why does this happen, and what steps should be taken for adding a name to the generated alert.