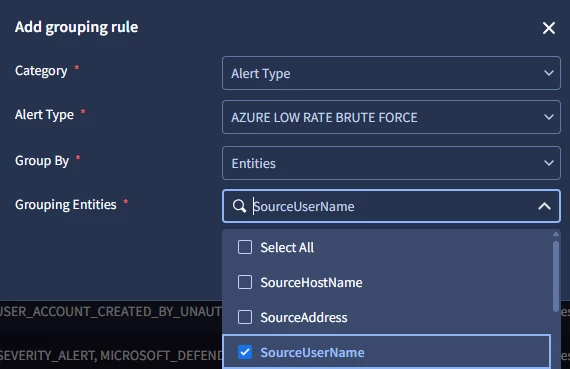
I'm trying to better understand how grouping by identifiers works for entities and origins.
https://cloud.google.com/chronicle/docs/soar/investigate/working-with-alerts/alert-grouping-mechanism-admin
From the documentation, I understand that by enabling this feature, alerts in SIEM will be grouped from a sourceGroupIdentifier. The question here is, how is this identifier defined from SIEM alerts?
Is this identifier created based on the SOAR ontology rules? If I want to create a grouping based on some field present in the result of my detections, is that possible?