I'm working with data tables in a SecOps SIEM, where the goal is to evaluate incoming log data against records in the data table. The relevant fields are:
Data Table:
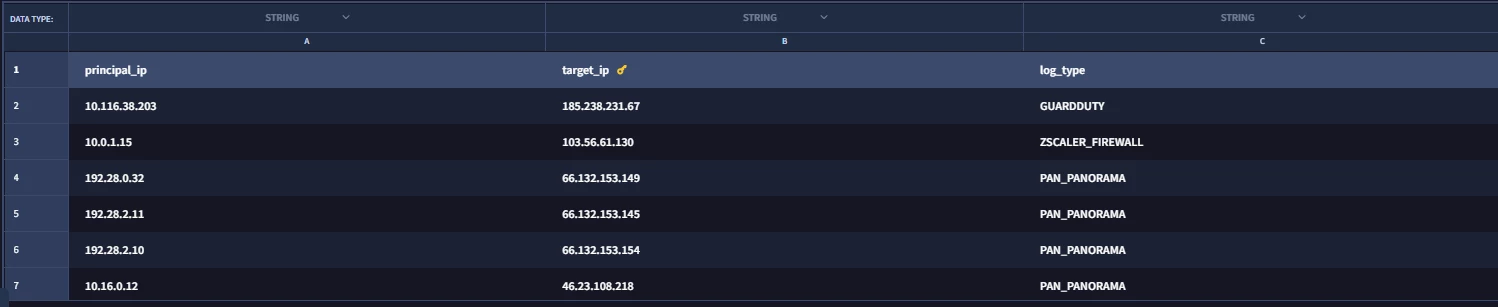
Logic:
%DL_Anomali_High_Critical_Severity_IP_v1.target_ip = $ip
$e.principal.ip = %DL_Anomali_High_Critical_Severity_IP_v1.principal_ip
$e.metadata.log_type = %DL_Anomali_High_Critical_Severity_IP_v1.log_type
Sample Log Data:
principal.ip= [removed by moderator]
target.ip = [removed by moderator]
log_type = PAN_PANORAMA
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
Existing Behavior:
Currently, if the log data exactly matches a row (for example, row 5 in the table above), the rule is triggered.
Desired Requirement:
I need the opposite behavior:
- If all log values for
target.ip,principal.ip, andlog_typematch a single row in the data table, the rule should NOT trigger. - If even one value does not match (i.e., only partial match, or no row contains all three values together), the rule SHOULD trigger.
- If
target.ipis not in the table, the rule SHOULD trigger as well.
Example Use Case:
- If
target.ipexists in the data table, but the correspondingprincipal.ipandlog_typein that row do not match (or are in different rows), the rule should be activated.
What is the best way to implement this logic so that the rule is only suppressed when there is a complete row match, but triggers on any partial or mismatched data? Are there any best practices or patterns within common rule engines or data table handling for achieving this "negative match" behavior?
Any examples, pseudocode, or references to common patterns are appreciated!




