Hi everyone,
I'm trying to figure out how to restrict access to specific playbooks or blocks in our environment so that only selected SOC team members can view and run them.
Currently, by default, all users in our SOC have access to view and run all playbooks. I want to change this behavior so that certain sensitive or specialized playbooks are only visible and executable by specific users in SOC.
I tried using the access control options within the playbook settings and specified certain usernames, but it didn’t work as expected. It seems like the default global access is overriding these specific restrictions.
Has anyone successfully configured access controls for playbooks or blocks at a more granular level? Is there a way to override or customize the default permissions?

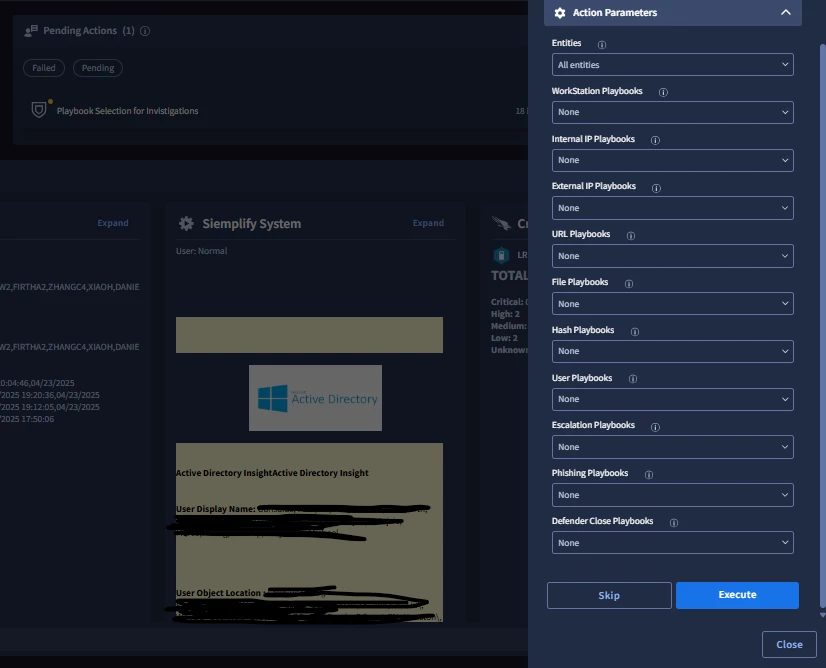
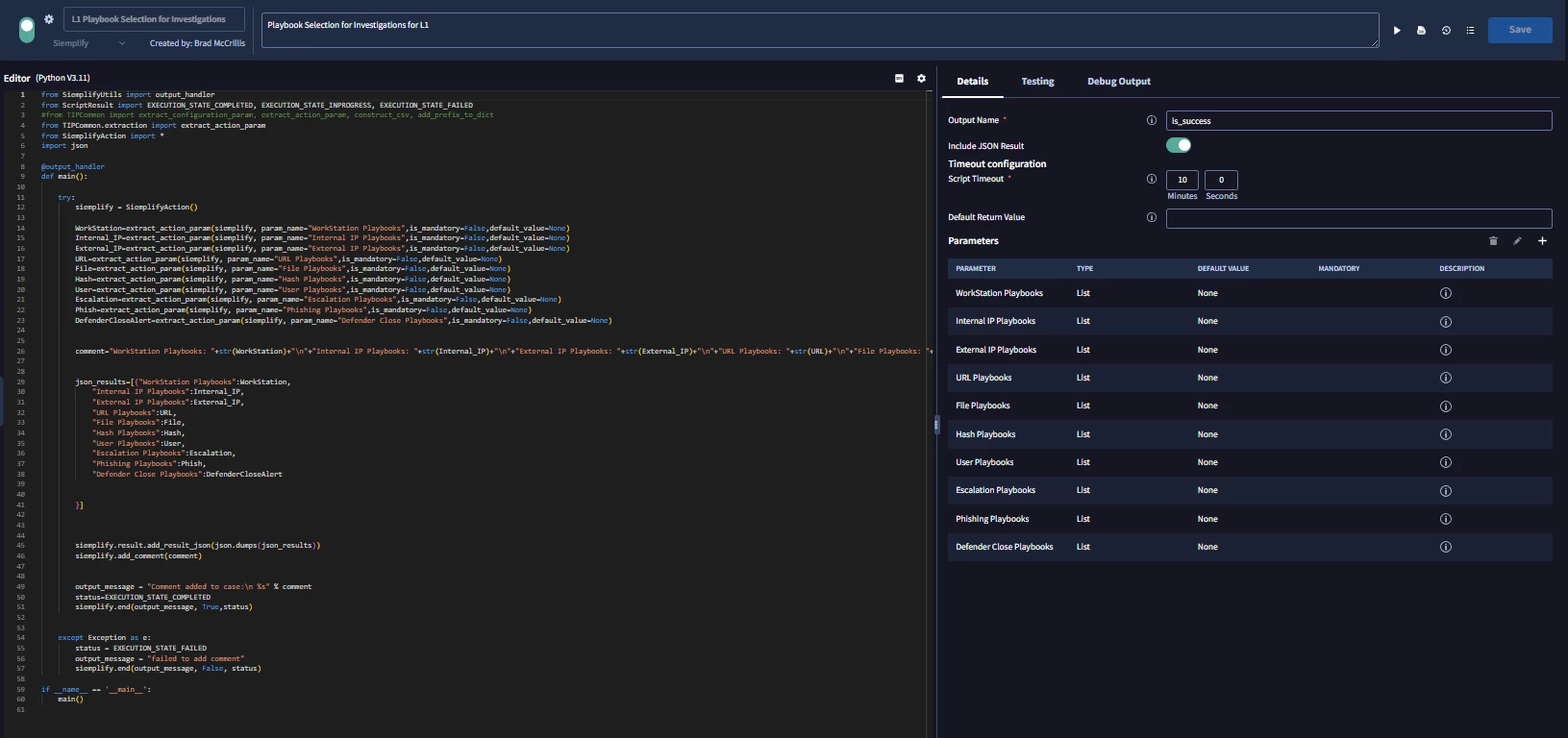
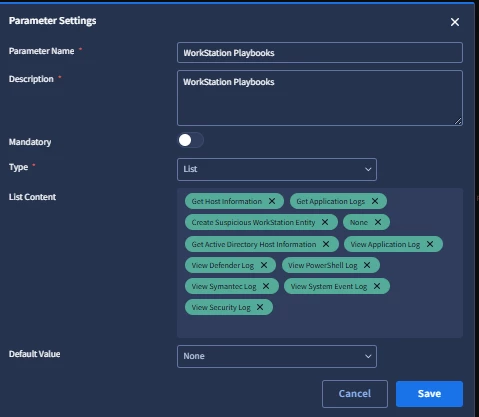 as an example would be our L1 workstation playbook options.
as an example would be our L1 workstation playbook options.