Hello,
I am looking at the following preview documentation:
https://cloud.google.com/chronicle/docs/preview/search/raw-log-search-in-investigate
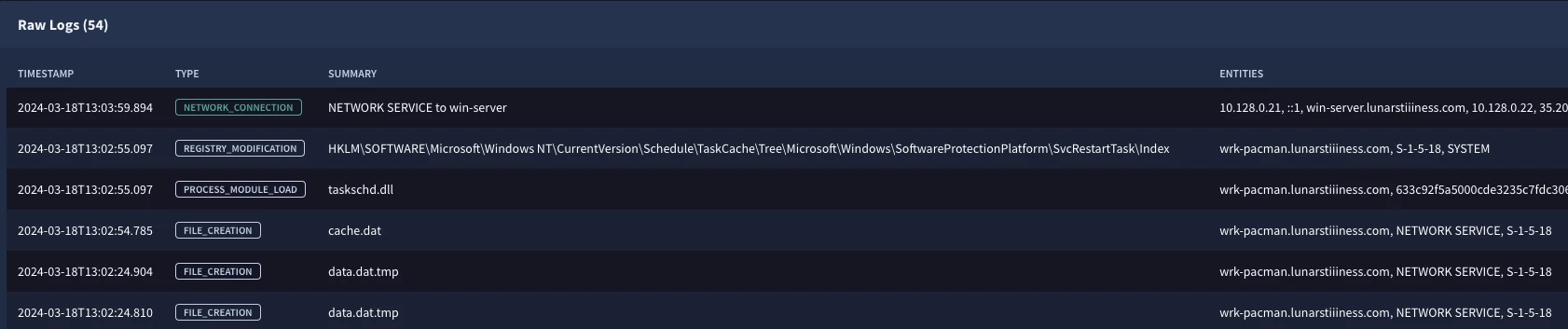
Using UDM Search, one can only search for UDM events and not UDM entities. The documentation says:
>After you complete a raw log search, each matching raw log line is replaced with the events and entities contained in the log line.
What does that mean? And is raw log search and UDM entity search the same?
Thank you!