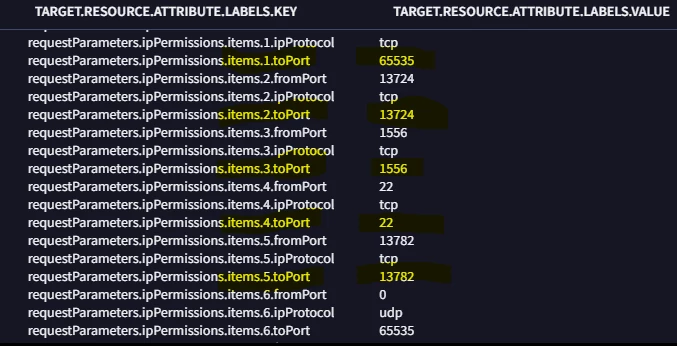
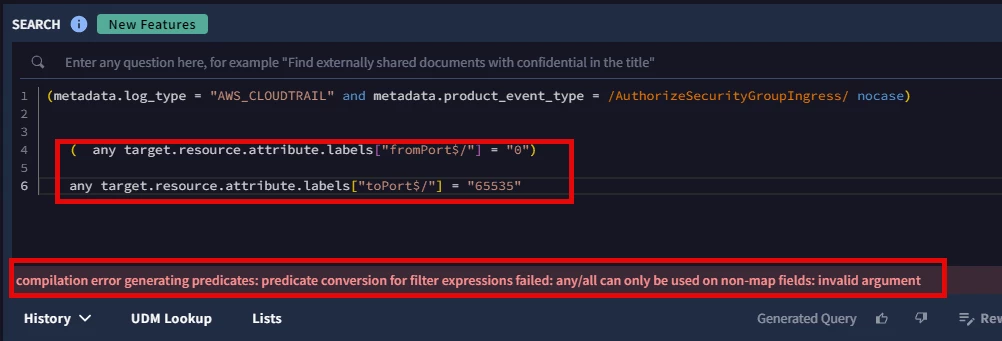
Hi All,
Any type of key-value UDM fields when used multiple time with "AND" condition in YaraL it doesn't work. but when i try the same in UDM search it works.
// Sample Example
UDM Search , Events are getting detected
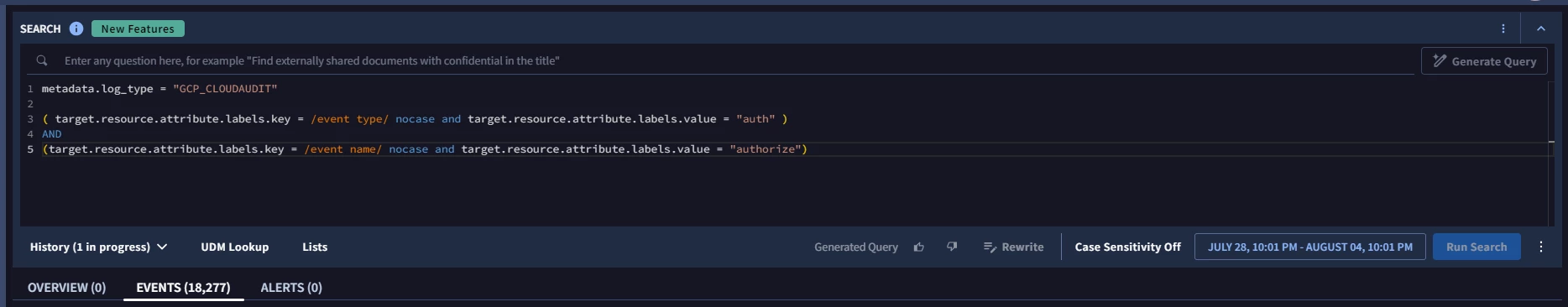
But when i try the same thing in Rules Editor in YARA L doesn't seem to work
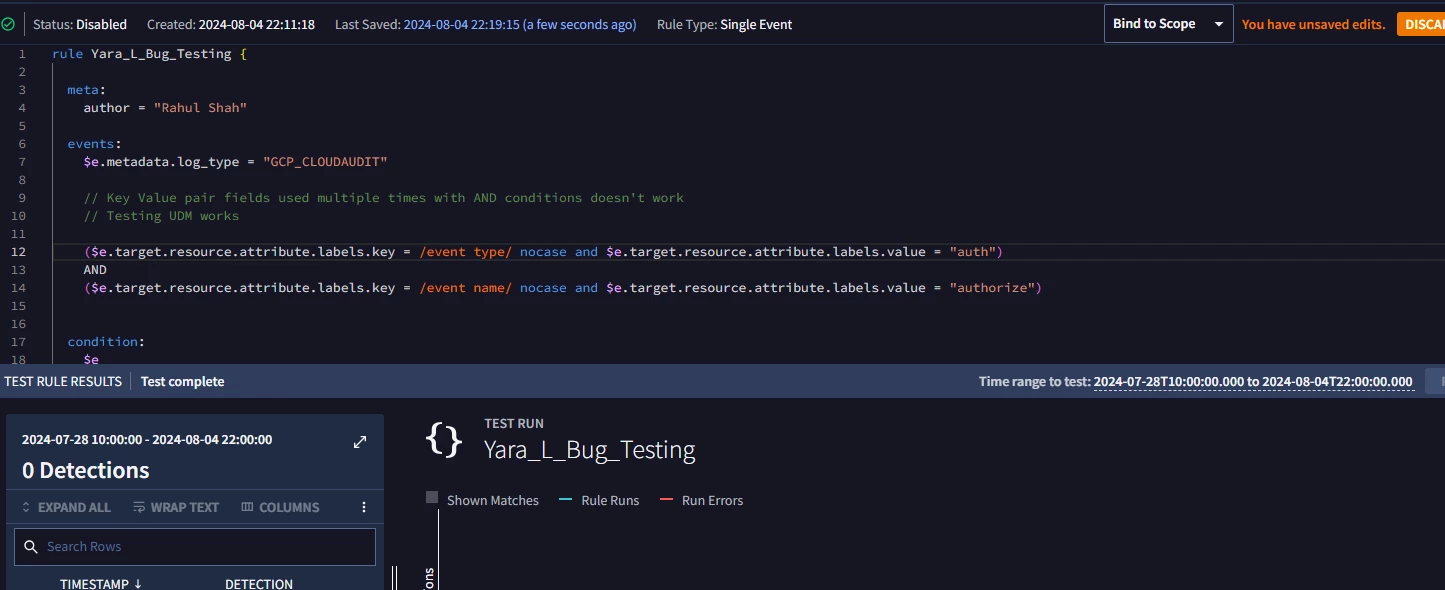
Sample Rule to Test
rule Yara_L_Bug_Testing {
meta:
author = "Rahul Shah"
events:
$e.metadata.log_type = "GCP_CLOUDAUDIT"
// Key Value pair fields used multiple times with AND conditions doesn't work
// Testing UDM works
($e.target.resource.attribute.labels.key = /event type/ nocase and $e.target.resource.attribute.labels.value = "auth")
AND
($e.target.resource.attribute.labels.key = /event name/ nocase and $e.target.resource.attribute.labels.value = "authorize")
condition:
$e
}