Hello!
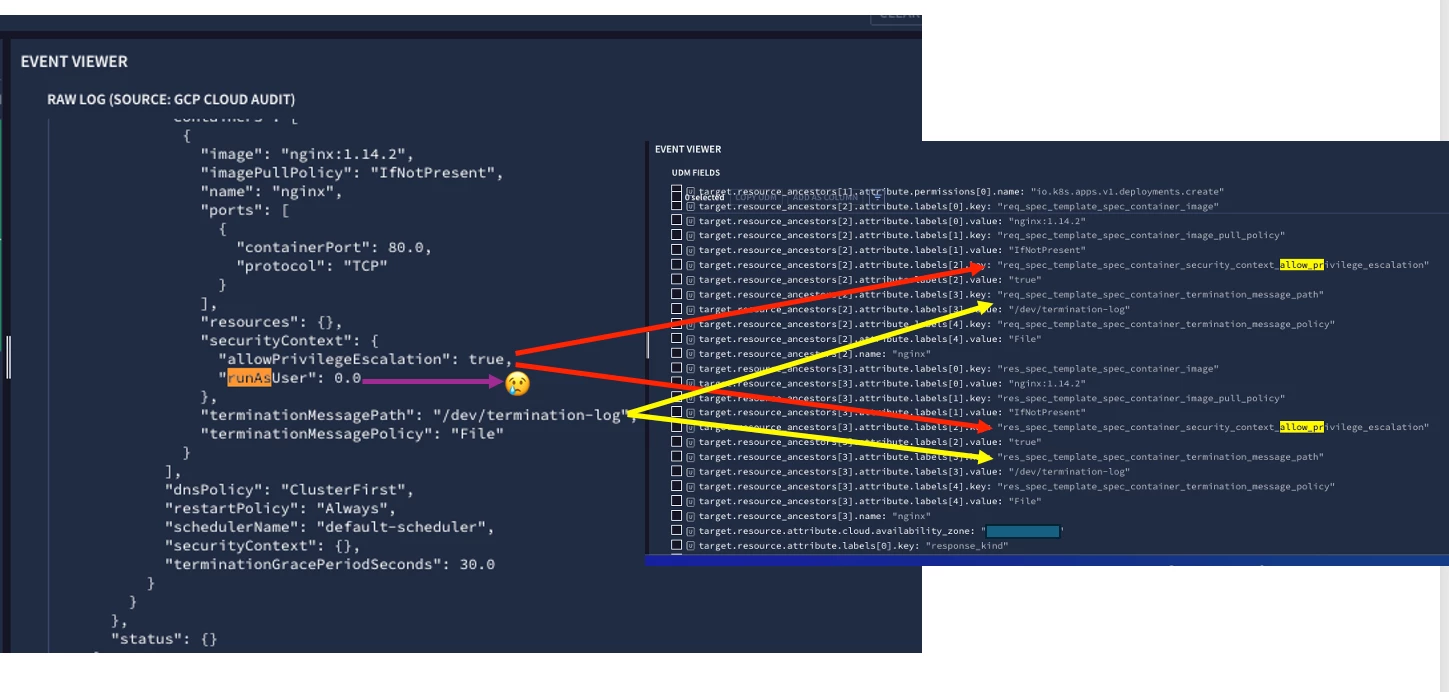
When a deployment is created in Kubernetes, it is possible to add a field as part of the securityContext named runAsUser. If the value in this field is 0, that means the deployment is run as root, which is not good at all from a security perspective. So, we would like to detect when this happens using Chronicle.
In the documentation [1], it is possible to see an entry that ends with runAsUser, so that means the parser is able to do so. Also in the code it is shown:
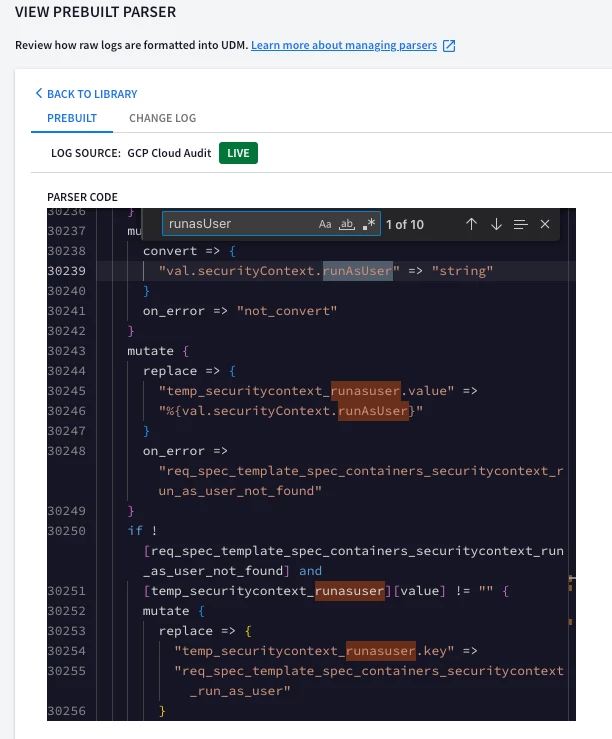
But when doing tests i.e., when deploying a deployment with the value and then chronicle consuming it and processing it, the runasUser mapped field is not displayed 😞
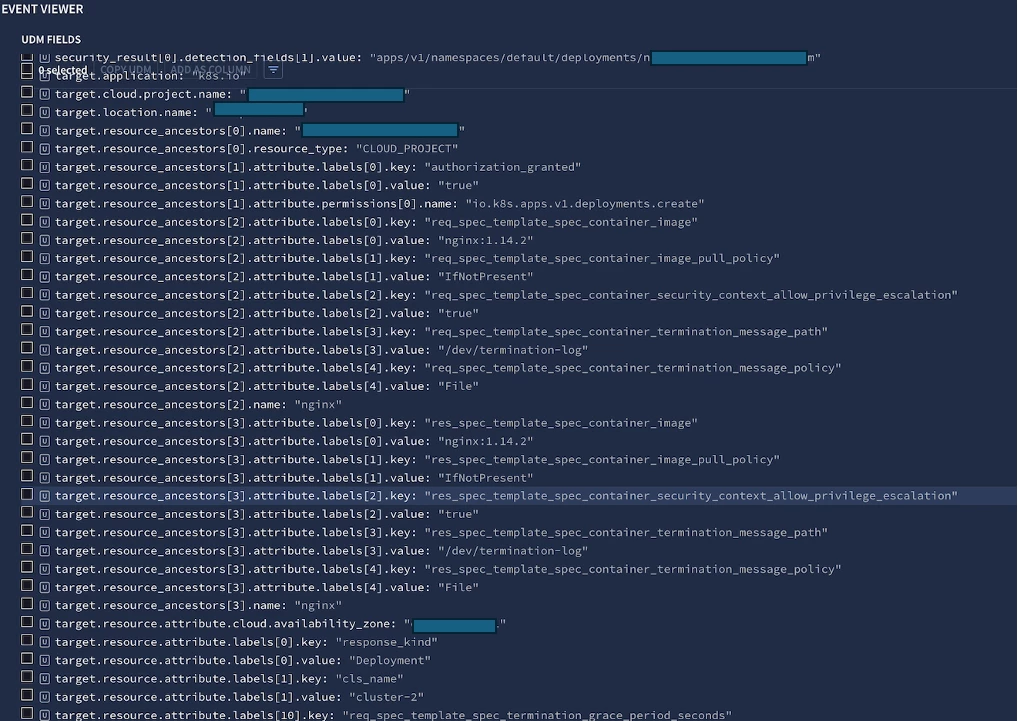
I open support case #55363713. After two months the issue is still present. The "solution" of the support case is "Engineering team already fixed the request as a best effort. Please, open a new case."
Two main questions please:
1. What to do when the documentation says one thing, and the code is in the product, but the product does not behave as expected? My guess was to open a support case, but it seems that is not the way, at least in this case.
2. Have you had this type of answer in support cases? What can be done? Is it normal to wait two months and receive that kind of answer? I I don't want to end in an endless "done-best-effort -> open-a-new-case" loop
Thank you!!!
[1] https://cloud.google.com/chronicle/docs/ingestion/default-parsers/collect-audit-logs