Hi,
I have configured my BindPlane agents to collect logs from the Windows Security Events, Microsoft-Windows-PowerShell/Operational, and Sysmon channels. For each log source, I have specified the log type in the processor configuration as per the documentation.
I have set up three different ports on the destination, with each port designated to receive a specific log type. Logs are being sent and received on all three ports as expected.
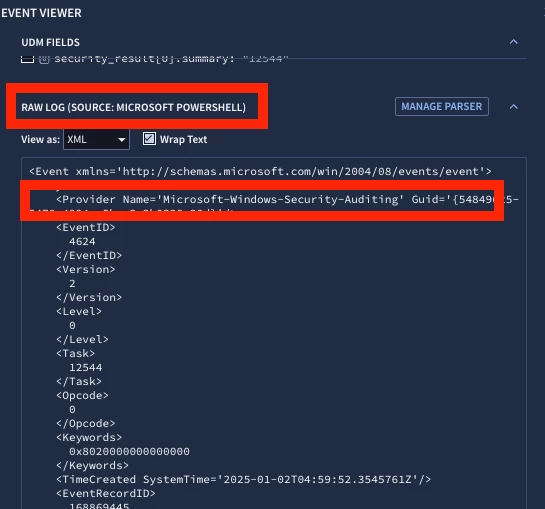
However, in Google SecOps, when I search for logs from the Microsoft-Windows-PowerShell/Operational channel, I observe that some logs are incorrectly categorized as Windows Events log type instead of PowerShell log type. This issue does not occur for all logs; some logs from the PowerShell channel are correctly written as the PowerShell log type, while others are misclassified as Sysmon or Windows Events or misclassified as Powershell when its Windows Events etc.
My forwarder is configured to listen 20 different log types, and this issue only occurs with BindPlane agents forwarding logs from the Windows Security Events, Powershell and Sysmon channels.
Is there anyone who can help identify the cause of this issue?
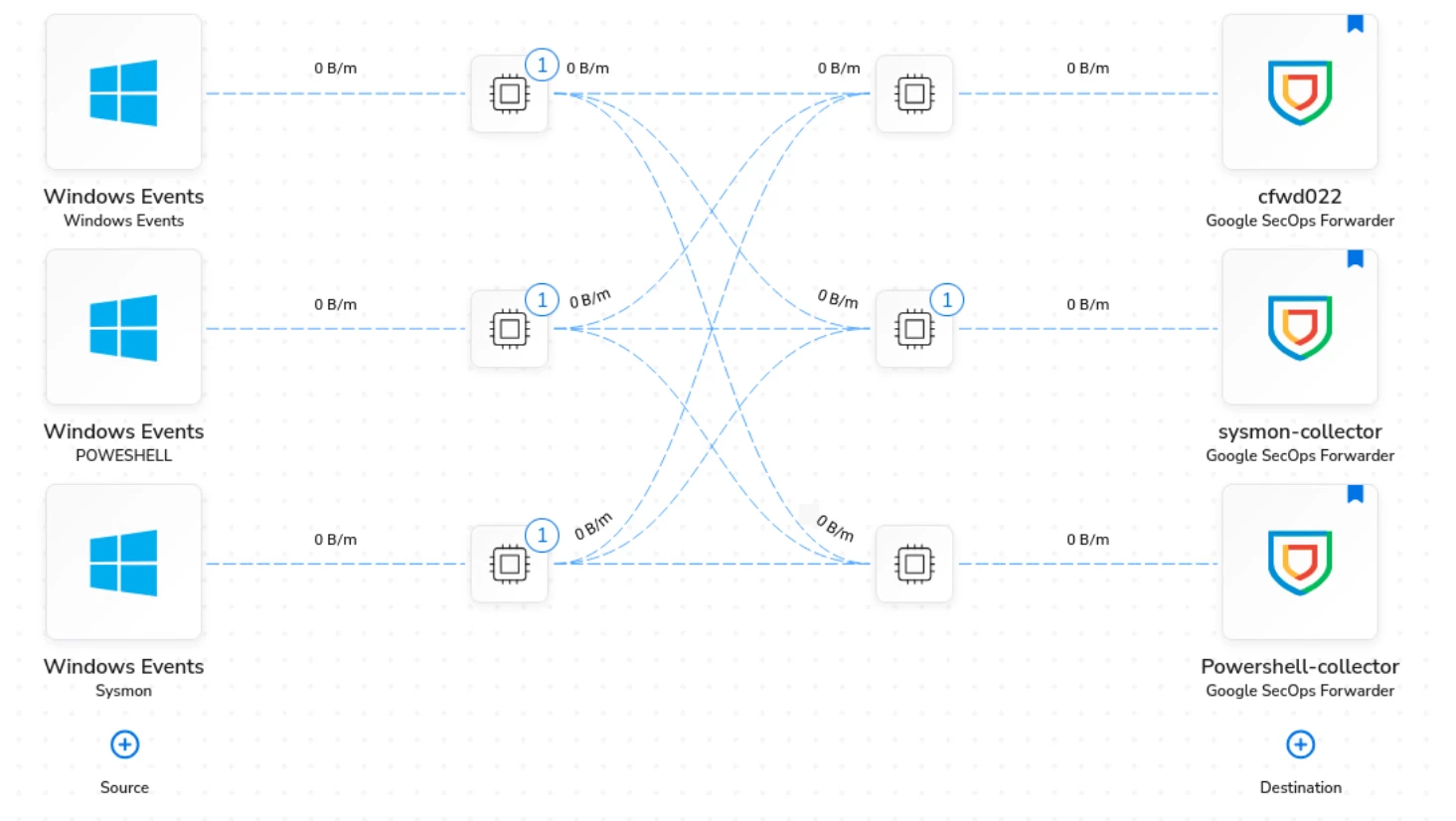
That Security-Auditing channel isn't in the Source configuration on Bindplane.