Hello community,
I´m new to the SOAR part of Google SecOps and I´m starting with the creation of a playbook for an IOC based detection. I came across the Gemini summary page and noticed the malicious verdict. I was expecting to utilize an VirusTotal enrichment block to get this verdict but now I am wondering how does Gemini/GSOAR come to it and if this can be used inside a playbook/block.
Maybe someone already came across this?
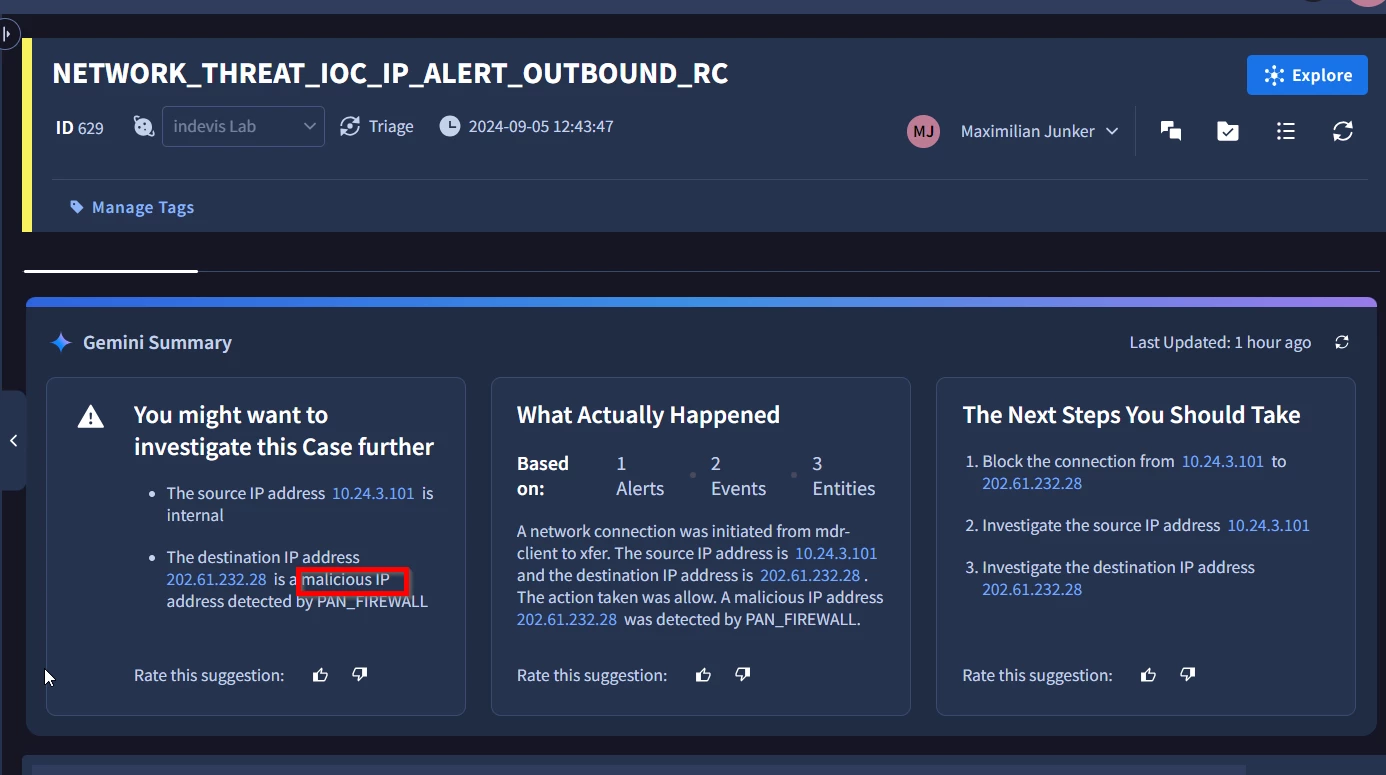
Thank you!
/Max




