hello Team
Could anyone please help me with metrics alert event name count functionality? I have a use case that requires calculating the average number of alerts received per host from Defender . Can this metric be used for that purpose? Also, does it include Defender alerts by default? i only need defender alerts
This Splunk query I need to translate to yara is designed to monitor and analyze security alerts generated by Microsoft Defender Advanced Threat Protection (ATP) over a 7-day period. The goal is to identify hosts that are generating an unusually high number of alerts compared to their average hourly alert count.
Thanks in advance





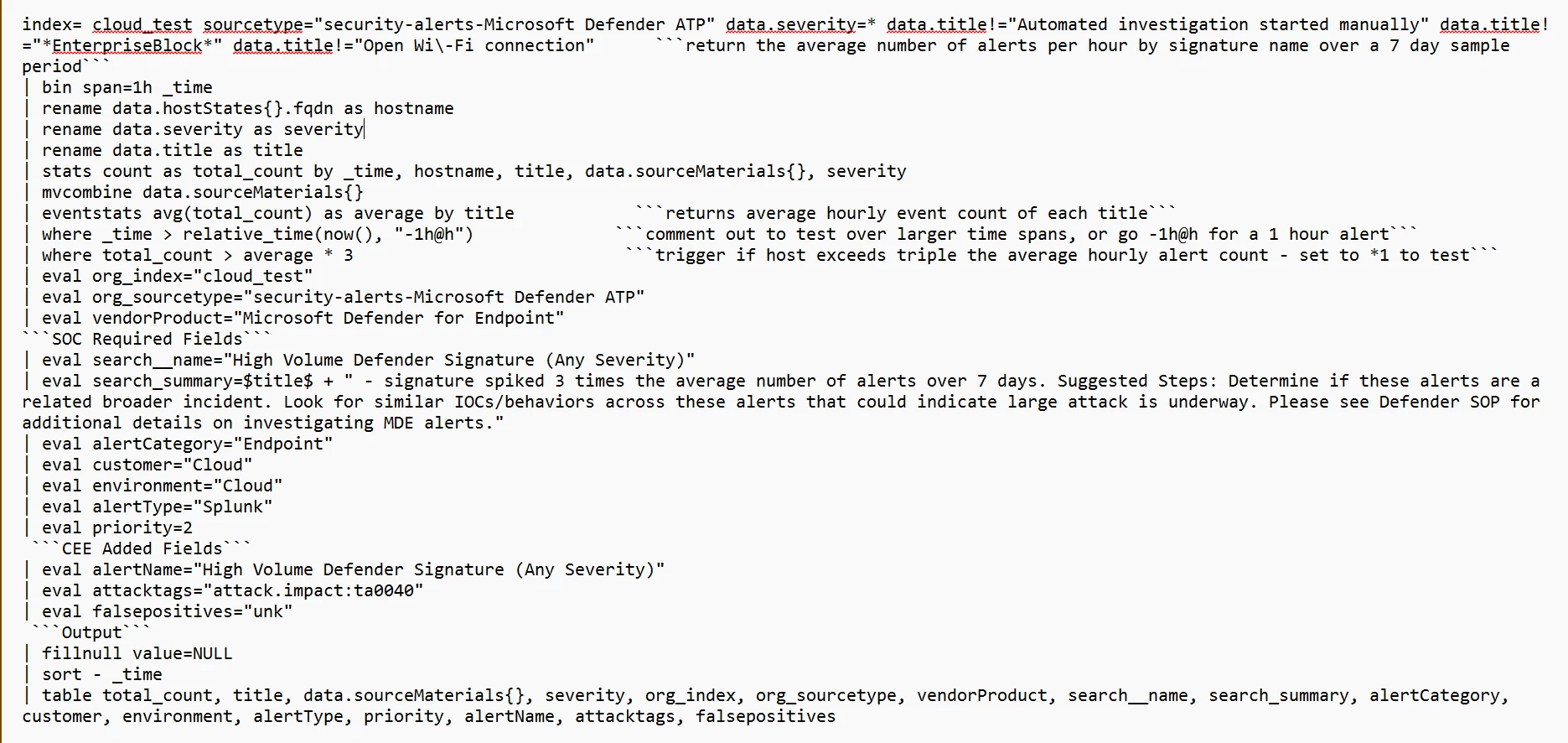 please find this snip
please find this snip
