Hello,
I currently have several alarms in the SOAR that are based on the same KQL rule in Sentinel. Sometimes, as described in the connector, the KQL is executed and the event data is taken over. In other cases, the SecurityAlert table is read.
Connector Description: "Both scheduled and NRT alerts are by default ingested using the log analytics KQL queries to get alert and event data"
We're using the Microsoft Azure Sentinel Incident Connector v2 in Version 52, today I've updated to 53
As an example, I have two screenshots: both SOAR incidents were generated on different days using the same connector in the same SOAR environment. Both are originating from the same Sentinel Scheduled Alert.
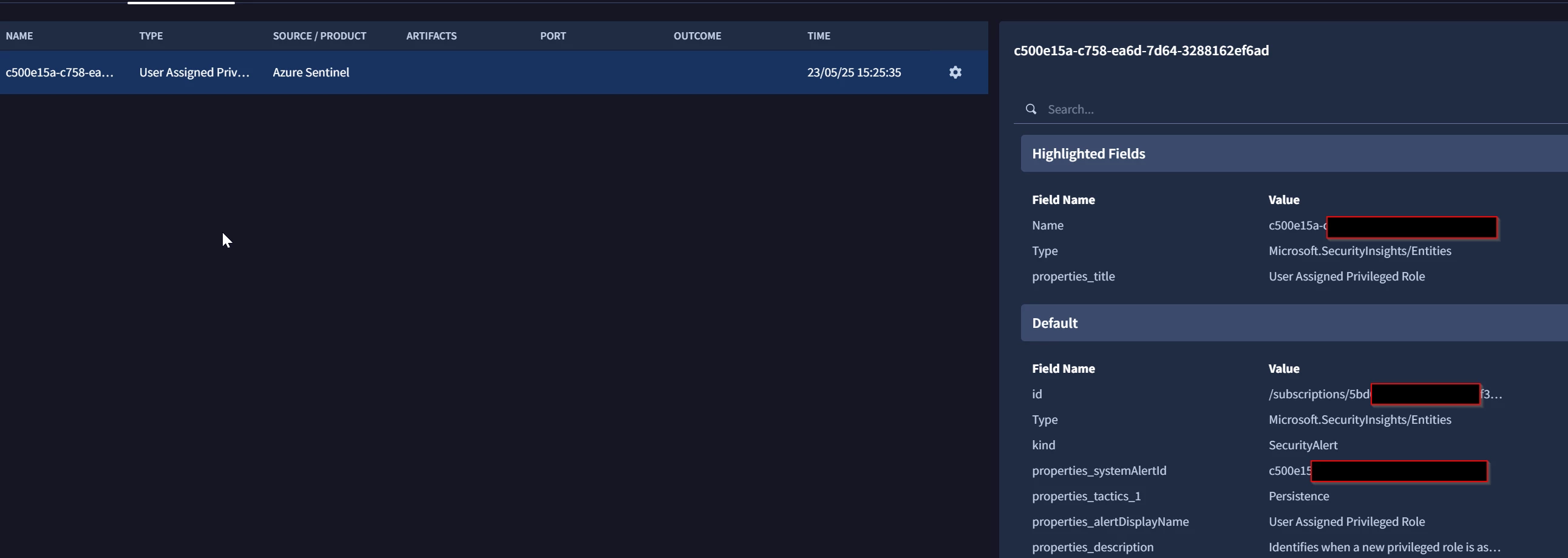
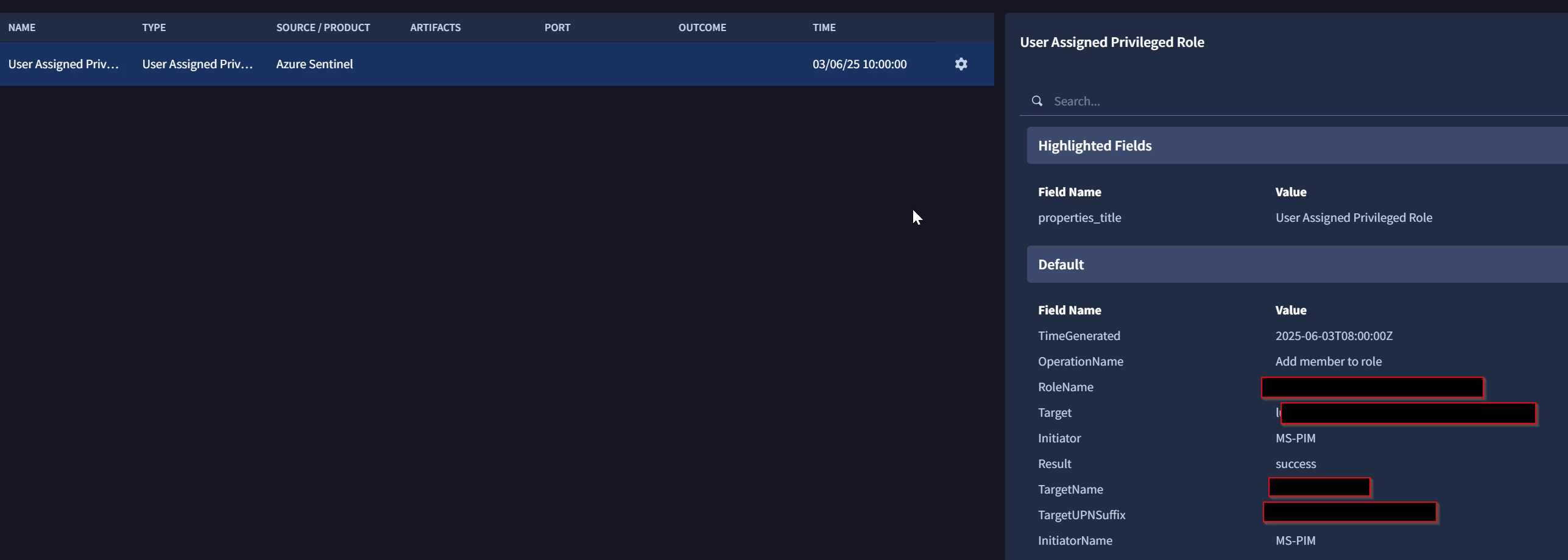
In the "bad" example the Name of the Event equals the Sentinel AlertID from the SecurityAlert Table.
But no infomation why the Incident was created in Sentinel - this originates from the KQL query of the Alert.
Am I'm doing something wrong the outcome of the ingestion seems unpredictable ?
Best regards
Dominik




