Hello,
thanks to @cmmartin_google I came across the idea to import Misp data into Chronicle. For several reasons I was not able to do it the exact way he describes but I´ve got it working with an csv export and then the import via nxlog and a forwarder. That is all working fine. Now I was trying to adjust his rules. But this is the part I´m not able to get working. So here is the rule as I thought it should work:
rule misp_ioc_network_domain_dns_question {
meta:
events:
$event.metadata.event_type = "NETWORK_DNS"
$event.network.dns.questions.name = $domain
$event.principal.asset.hostname = $hostname
$misp.graph.metadata.vendor_name = "MISP"
$misp.graph.metadata.entity_type = "DOMAIN_NAME"
$misp.graph.entity.hostname = $domain
match:
$hostname over 1m
condition:
$event and $misp
}
And this is the MISP Log:
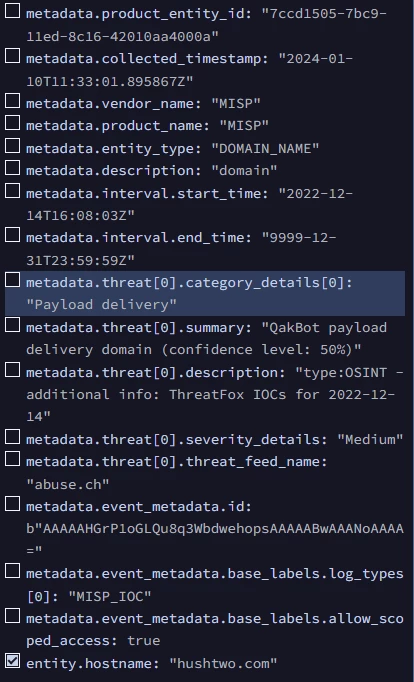
And this is the log that should get detected
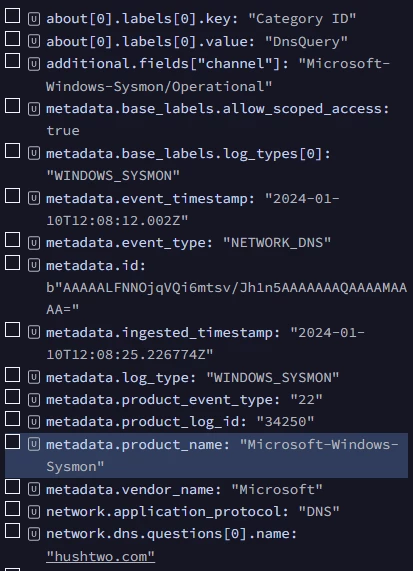
Any Idea what I´m doing wrong here?



