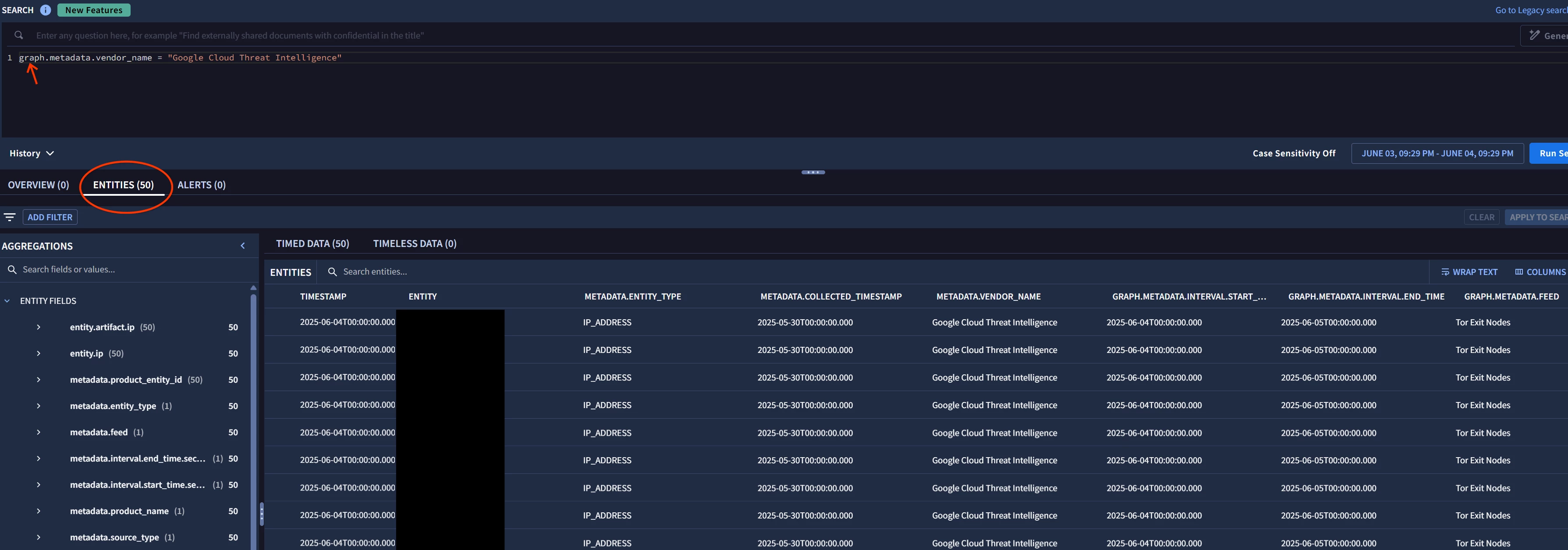
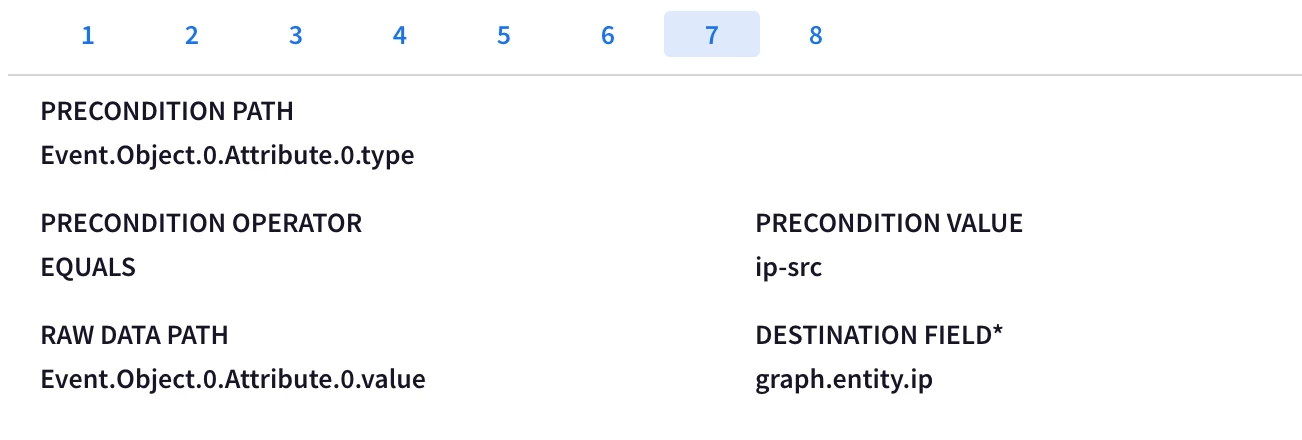
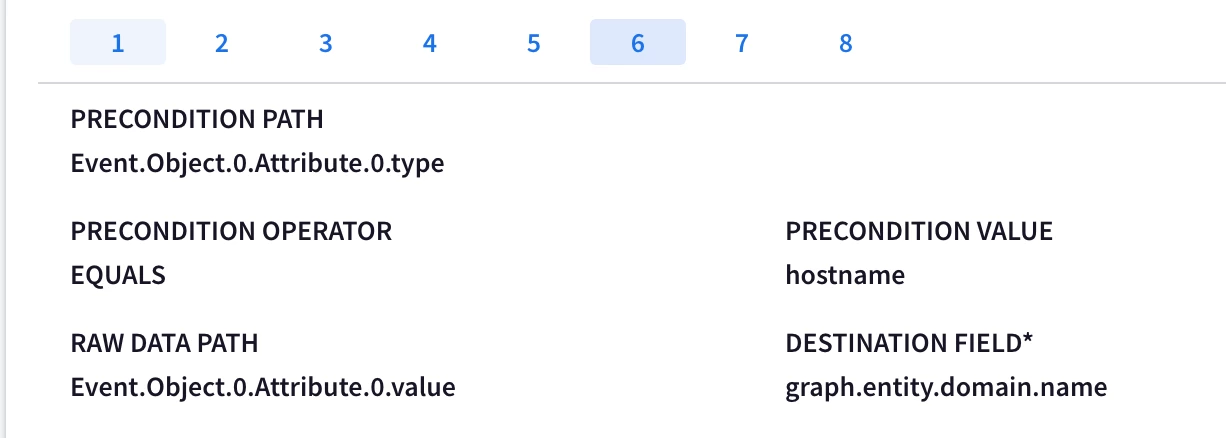
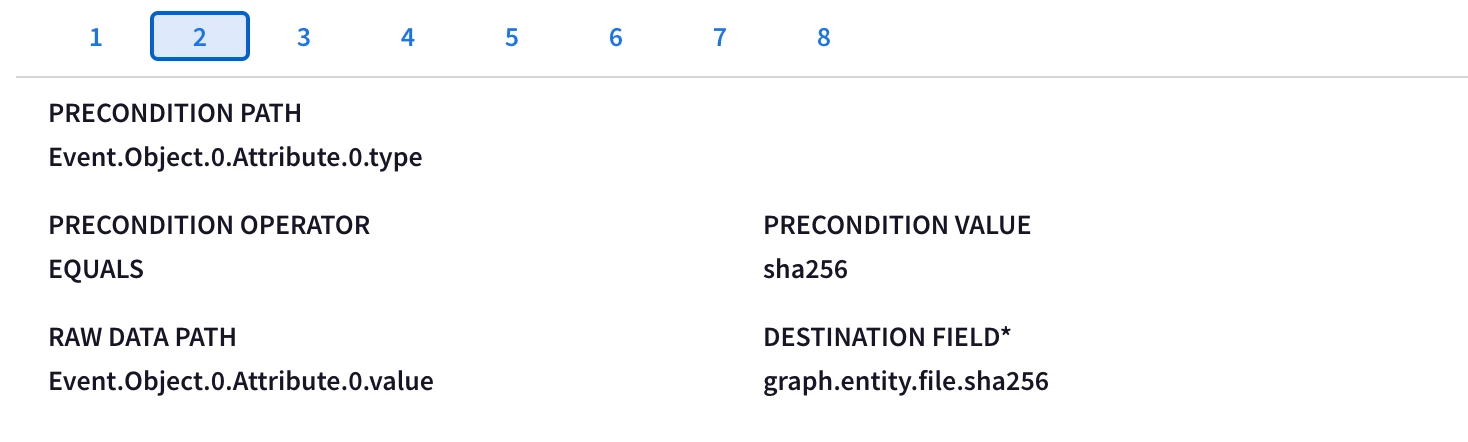
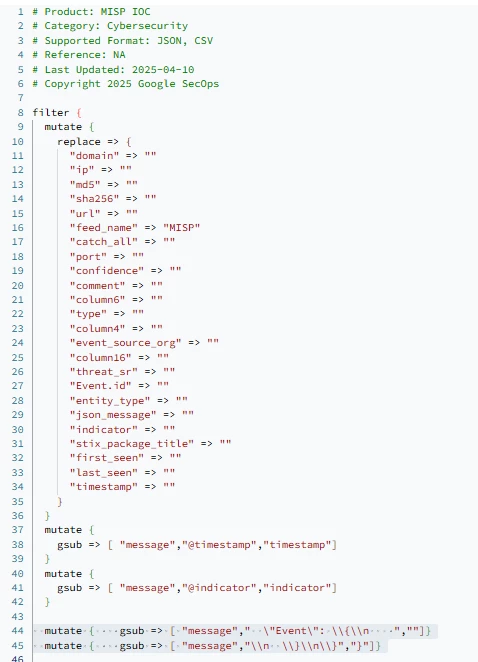
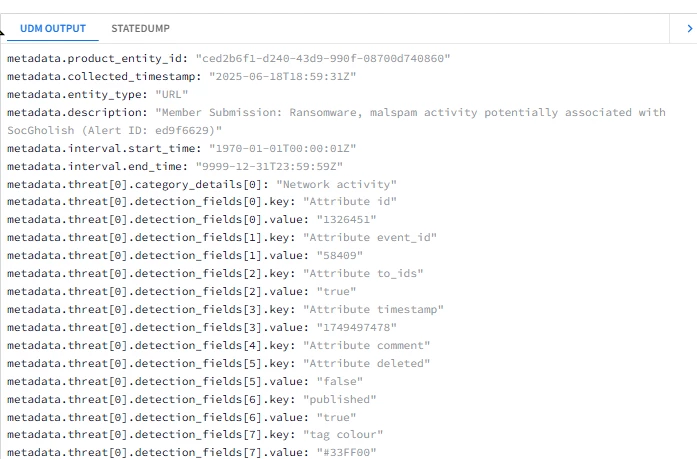
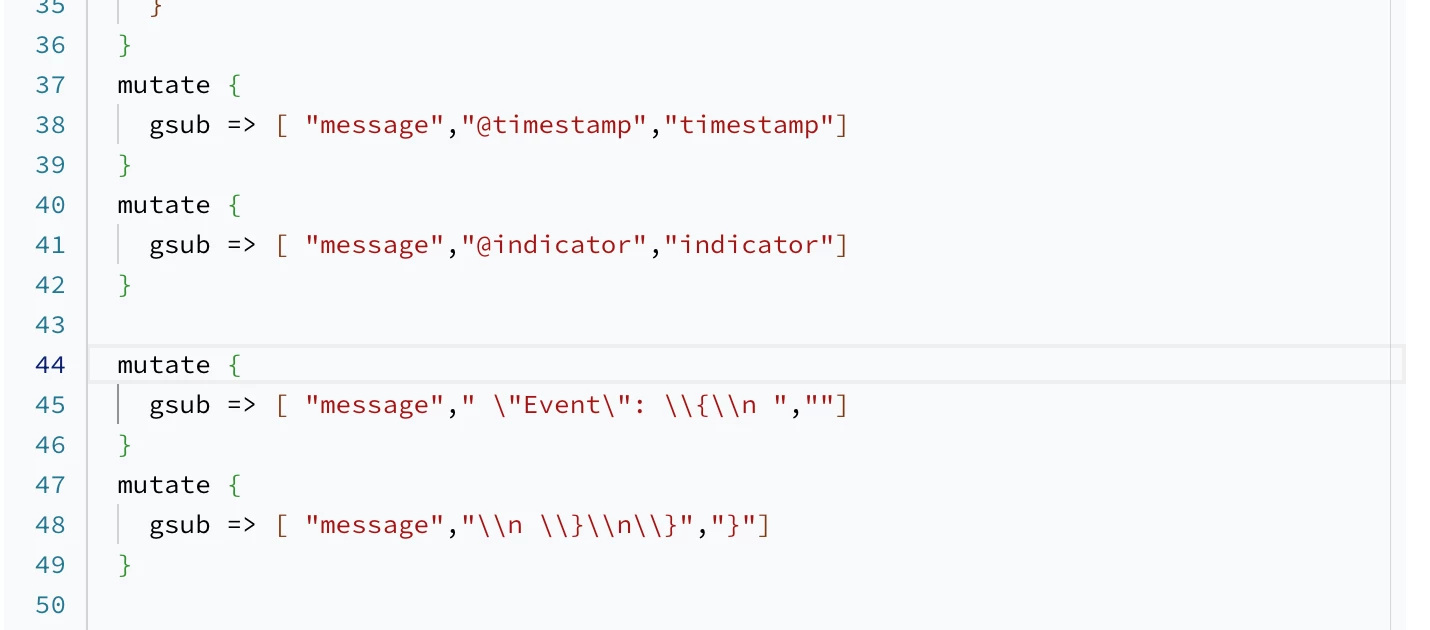
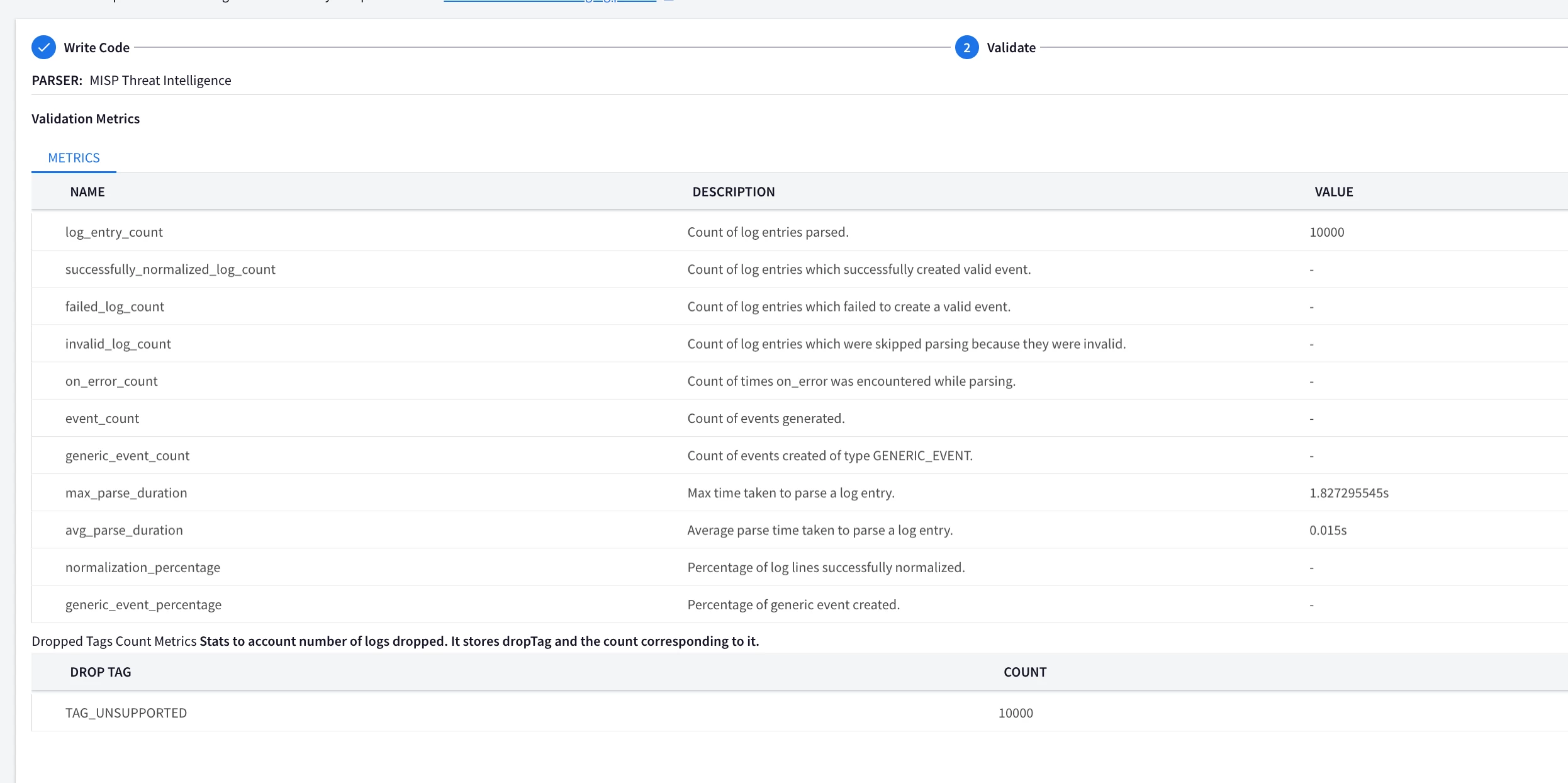
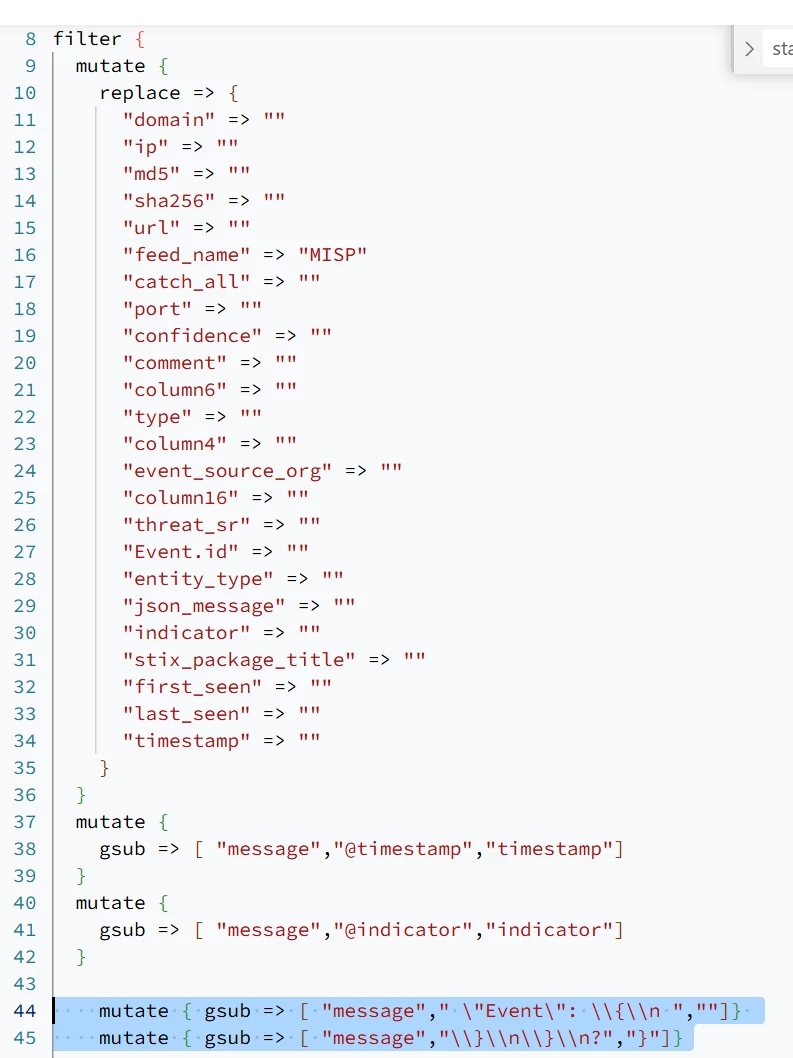
Hi @AbdElHafez , these are not the initial instructions you had on this page, have you gotten rid of the webhook method because of this ticket? It should remain a valid method for ingesting MISP data, no?
Google caching even shows the webhook method before updates to the page were made:
I have followed the instructions that were on this web page before you updated them:
Configure a feed in Google SecOps to ingest the MISP Threat Intelligence logs
Go to SIEM Settings > Feeds.
Click Add new.
In the Feed name field, enter a name for the feed (for example, MISP Logs).
Select Webhook as the Source type.
Select MISP Threat Intelligence as the Log type.
Click Next.
Optional: Specify values for the following input parameters:
Split delimiter: the delimiter that is used to separate log lines, such as \\n.
Asset namespace: the asset namespace.
Ingestion labels: the label applied to the events from this feed.
Click Next.
Review the feed configuration in the Finalize screen, and then click Submit.
Click Generate Secret Key to generate a secret key to authenticate this feed.
Copy and store the secret key. You cannot view this secret key again. If needed, you can regenerate a new secret key, but this action makes the previous secret key obsolete.
From the Details tab, copy the feed endpoint URL from the Endpoint Information field. You need to specify this endpoint URL in your client application.
Click Done.
Heres a couple more:
{
"Event": {
"id": "58557",
"org_id": "1",
"date": "2025-06-18",
"info": "Member Submission: Phishing, Credential pharming activity (Alert ID: 96584937)",
"uuid": "65113e36-2c71-4043-b4ac-5b8fd6318a08",
"published": true,
"analysis": "0",
"attribute_count": "3",
"orgc_id": "31",
"timestamp": "1750264239",
"distribution": "0",
"sharing_group_id": "0",
"proposal_email_lock": false,
"locked": true,
"threat_level_id": "4",
"publish_timestamp": "1750291245",
"sighting_timestamp": "0",
"disable_correlation": false,
"extends_uuid": "",
"protected": null,
"Attribute": [
{
"id": "1327878",
"event_id": "58557",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": false,
"uuid": "85aaafef-5120-4380-83a5-c025aabc8817",
"timestamp": "1750264235",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "143.55.232.13",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2094",
"name": "audience-industry:Securities & Investments",
"colour": "#111cf7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2079",
"name": "audience-region:Europe",
"colour": "#6197ca",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
],
"Tag": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2094",
"name": "audience-industry:Securities & Investments",
"colour": "#111cf7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2079",
"name": "audience-region:Europe",
"colour": "#6197ca",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
}
],
"_AttributeFlattened": [
{
"id": "1327878",
"event_id": "58557",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": false,
"uuid": "85aaafef-5120-4380-83a5-c025aabc8817",
"timestamp": "1750264235",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "143.55.232.13",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2094",
"name": "audience-industry:Securities & Investments",
"colour": "#111cf7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2079",
"name": "audience-region:Europe",
"colour": "#6197ca",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
]
}
}
Heres a couple more:
{
"Event": {
"id": "58557",
"org_id": "1",
"date": "2025-06-18",
"info": "Member Submission: Phishing, Credential pharming activity (Alert ID: 96584937)",
"uuid": "65113e36-2c71-4043-b4ac-5b8fd6318a08",
"published": true,
"analysis": "0",
"attribute_count": "3",
"orgc_id": "31",
"timestamp": "1750264239",
"distribution": "0",
"sharing_group_id": "0",
"proposal_email_lock": false,
"locked": true,
"threat_level_id": "4",
"publish_timestamp": "1750291245",
"sighting_timestamp": "0",
"disable_correlation": false,
"extends_uuid": "",
"protected": null,
"Attribute": [
{
"id": "1327878",
"event_id": "58557",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": false,
"uuid": "85aaafef-5120-4380-83a5-c025aabc8817",
"timestamp": "1750264235",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "143.55.232.13",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2094",
"name": "audience-industry:Securities & Investments",
"colour": "#111cf7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2079",
"name": "audience-region:Europe",
"colour": "#6197ca",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
],
"Tag": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2094",
"name": "audience-industry:Securities & Investments",
"colour": "#111cf7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2079",
"name": "audience-region:Europe",
"colour": "#6197ca",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
}
],
"_AttributeFlattened": [
{
"id": "1327878",
"event_id": "58557",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": false,
"uuid": "85aaafef-5120-4380-83a5-c025aabc8817",
"timestamp": "1750264235",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "143.55.232.13",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2094",
"name": "audience-industry:Securities & Investments",
"colour": "#111cf7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2079",
"name": "audience-region:Europe",
"colour": "#6197ca",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
]
}
}{
"Event": {
"id": "58535",
"org_id": "1",
"date": "2025-06-17",
"info": "Member Submission: Payroll Diversion activity (Alert ID: f7e893ae)",
"uuid": "4b4cbfe8-3211-4d19-906f-a85153db70d5",
"published": true,
"analysis": "0",
"attribute_count": "1",
"orgc_id": "31",
"timestamp": "1750183271",
"distribution": "0",
"sharing_group_id": "0",
"proposal_email_lock": false,
"locked": true,
"threat_level_id": "4",
"publish_timestamp": "1750204819",
"sighting_timestamp": "0",
"disable_correlation": false,
"extends_uuid": "",
"protected": null,
"Attribute": [
{
"id": "1327657",
"event_id": "58535",
"object_id": "0",
"object_relation": null,
"category": "Payload delivery",
"type": "email-src",
"to_ids": true,
"uuid": "90e8ff00-f057-4c13-b7d2-a528e2bf96b4",
"timestamp": "1750183272",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "mystubresource@gmail.com",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2124",
"name": "attack-pattern:Payroll Diversion",
"colour": "#887eff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2097",
"name": "audience-industry:Payments",
"colour": "#3eb067",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
],
"Tag": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2124",
"name": "attack-pattern:Payroll Diversion",
"colour": "#887eff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2097",
"name": "audience-industry:Payments",
"colour": "#3eb067",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
}
],
"_AttributeFlattened": [
{
"id": "1327657",
"event_id": "58535",
"object_id": "0",
"object_relation": null,
"category": "Payload delivery",
"type": "email-src",
"to_ids": true,
"uuid": "90e8ff00-f057-4c13-b7d2-a528e2bf96b4",
"timestamp": "1750183272",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "mystubresource@gmail.com",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2124",
"name": "attack-pattern:Payroll Diversion",
"colour": "#887eff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2097",
"name": "audience-industry:Payments",
"colour": "#3eb067",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
]
}
}
{
"Event": {
"id": "58535",
"org_id": "1",
"date": "2025-06-17",
"info": "Member Submission: Payroll Diversion activity (Alert ID: f7e893ae)",
"uuid": "4b4cbfe8-3211-4d19-906f-a85153db70d5",
"published": true,
"analysis": "0",
"attribute_count": "1",
"orgc_id": "31",
"timestamp": "1750183271",
"distribution": "0",
"sharing_group_id": "0",
"proposal_email_lock": false,
"locked": true,
"threat_level_id": "4",
"publish_timestamp": "1750204819",
"sighting_timestamp": "0",
"disable_correlation": false,
"extends_uuid": "",
"protected": null,
"Attribute": [
{
"id": "1327657",
"event_id": "58535",
"object_id": "0",
"object_relation": null,
"category": "Payload delivery",
"type": "email-src",
"to_ids": true,
"uuid": "90e8ff00-f057-4c13-b7d2-a528e2bf96b4",
"timestamp": "1750183272",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "mystubresource@gmail.com",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2124",
"name": "attack-pattern:Payroll Diversion",
"colour": "#887eff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2097",
"name": "audience-industry:Payments",
"colour": "#3eb067",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
],
"Tag": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2124",
"name": "attack-pattern:Payroll Diversion",
"colour": "#887eff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2097",
"name": "audience-industry:Payments",
"colour": "#3eb067",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
}
],
"_AttributeFlattened": [
{
"id": "1327657",
"event_id": "58535",
"object_id": "0",
"object_relation": null,
"category": "Payload delivery",
"type": "email-src",
"to_ids": true,
"uuid": "90e8ff00-f057-4c13-b7d2-a528e2bf96b4",
"timestamp": "1750183272",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "mystubresource@gmail.com",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2124",
"name": "attack-pattern:Payroll Diversion",
"colour": "#887eff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2097",
"name": "audience-industry:Payments",
"colour": "#3eb067",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
]
}
}{
"Event": {
"id": "58243",
"org_id": "1",
"date": "2021-01-05",
"info": "Partner Submission: Ransomware, malspam activity potentially associated with MUMMY SPIDER, Dridex, Emotet, TrickBot, Qakbot. Reported on 05 January 2021. (Alert ID: 4fe45ac9)",
"uuid": "861e0297-893f-4c4b-83a8-c1c63216b071",
"published": true,
"analysis": "0",
"attribute_count": "130",
"orgc_id": "31",
"timestamp": "1627412846",
"distribution": "0",
"sharing_group_id": "0",
"proposal_email_lock": false,
"locked": true,
"threat_level_id": "4",
"publish_timestamp": "1747893242",
"sighting_timestamp": "0",
"disable_correlation": false,
"extends_uuid": "",
"protected": null,
"Attribute": [
{
"id": "1323097",
"event_id": "58243",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": true,
"uuid": "d1f93f40-460e-47dc-9fac-3c7431239274",
"timestamp": "1627412847",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "177.85.167.10",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "1574",
"name": "malware:emotet",
"colour": "#ad00ff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2505",
"name": "malware:Dridex",
"colour": "#691672",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2268",
"name": "malware:Qakbot",
"colour": "#0d53a3",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2388",
"name": "threat-actor:MUMMY SPIDER",
"colour": "#1cb6e7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2343",
"name": "malware:TrickBot",
"colour": "#96e38c",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2179",
"name": "attack-pattern:Ransomware",
"colour": "#5d7d17",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
],
"Tag": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "1574",
"name": "malware:emotet",
"colour": "#ad00ff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2505",
"name": "malware:Dridex",
"colour": "#691672",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2268",
"name": "malware:Qakbot",
"colour": "#0d53a3",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2388",
"name": "threat-actor:MUMMY SPIDER",
"colour": "#1cb6e7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2343",
"name": "malware:TrickBot",
"colour": "#96e38c",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2179",
"name": "attack-pattern:Ransomware",
"colour": "#5d7d17",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
}
],
"_AttributeFlattened": [
{
"id": "1323097",
"event_id": "58243",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": true,
"uuid": "d1f93f40-460e-47dc-9fac-3c7431239274",
"timestamp": "1627412847",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "177.85.167.10",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "1574",
"name": "malware:emotet",
"colour": "#ad00ff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2505",
"name": "malware:Dridex",
"colour": "#691672",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2268",
"name": "malware:Qakbot",
"colour": "#0d53a3",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2388",
"name": "threat-actor:MUMMY SPIDER",
"colour": "#1cb6e7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2343",
"name": "malware:TrickBot",
"colour": "#96e38c",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2179",
"name": "attack-pattern:Ransomware",
"colour": "#5d7d17",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
]
}
}
{
"Event": {
"id": "58243",
"org_id": "1",
"date": "2021-01-05",
"info": "Partner Submission: Ransomware, malspam activity potentially associated with MUMMY SPIDER, Dridex, Emotet, TrickBot, Qakbot. Reported on 05 January 2021. (Alert ID: 4fe45ac9)",
"uuid": "861e0297-893f-4c4b-83a8-c1c63216b071",
"published": true,
"analysis": "0",
"attribute_count": "130",
"orgc_id": "31",
"timestamp": "1627412846",
"distribution": "0",
"sharing_group_id": "0",
"proposal_email_lock": false,
"locked": true,
"threat_level_id": "4",
"publish_timestamp": "1747893242",
"sighting_timestamp": "0",
"disable_correlation": false,
"extends_uuid": "",
"protected": null,
"Attribute": [
{
"id": "1323097",
"event_id": "58243",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": true,
"uuid": "d1f93f40-460e-47dc-9fac-3c7431239274",
"timestamp": "1627412847",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "177.85.167.10",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "1574",
"name": "malware:emotet",
"colour": "#ad00ff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2505",
"name": "malware:Dridex",
"colour": "#691672",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2268",
"name": "malware:Qakbot",
"colour": "#0d53a3",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2388",
"name": "threat-actor:MUMMY SPIDER",
"colour": "#1cb6e7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2343",
"name": "malware:TrickBot",
"colour": "#96e38c",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2179",
"name": "attack-pattern:Ransomware",
"colour": "#5d7d17",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
],
"Tag": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "1574",
"name": "malware:emotet",
"colour": "#ad00ff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2505",
"name": "malware:Dridex",
"colour": "#691672",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2268",
"name": "malware:Qakbot",
"colour": "#0d53a3",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2388",
"name": "threat-actor:MUMMY SPIDER",
"colour": "#1cb6e7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2343",
"name": "malware:TrickBot",
"colour": "#96e38c",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2179",
"name": "attack-pattern:Ransomware",
"colour": "#5d7d17",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
}
],
"_AttributeFlattened": [
{
"id": "1323097",
"event_id": "58243",
"object_id": "0",
"object_relation": null,
"category": "Network activity",
"type": "ip-dst",
"to_ids": true,
"uuid": "d1f93f40-460e-47dc-9fac-3c7431239274",
"timestamp": "1627412847",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "177.85.167.10",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "1574",
"name": "malware:emotet",
"colour": "#ad00ff",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2505",
"name": "malware:Dridex",
"colour": "#691672",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2268",
"name": "malware:Qakbot",
"colour": "#0d53a3",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2388",
"name": "threat-actor:MUMMY SPIDER",
"colour": "#1cb6e7",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2343",
"name": "malware:TrickBot",
"colour": "#96e38c",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2179",
"name": "attack-pattern:Ransomware",
"colour": "#5d7d17",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
]
}
}{
"Event": {
"id": "58297",
"org_id": "1",
"date": "2025-05-28",
"info": "Member Submission: Phishing, malspam, Credential pharming activity potentially associated with Astaroth, Remcos, Agent Tesla, Netsupport RAT, ZPHP (Alert ID: c9e9d8f9)",
"uuid": "cdd13659-ab51-4b33-bd60-0dde0443f71f",
"published": true,
"analysis": "0",
"attribute_count": "16",
"orgc_id": "31",
"timestamp": "1748464239",
"distribution": "0",
"sharing_group_id": "0",
"proposal_email_lock": false,
"locked": true,
"threat_level_id": "4",
"publish_timestamp": "1748476827",
"sighting_timestamp": "0",
"disable_correlation": false,
"extends_uuid": "",
"protected": null,
"Attribute": [
{
"id": "1324223",
"event_id": "58297",
"object_id": "0",
"object_relation": null,
"category": "Payload delivery",
"type": "sha256",
"to_ids": true,
"uuid": "14e999a2-2622-427d-9698-a5120da6dc74",
"timestamp": "1748464239",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "3c54060447cd33a5aa4ce88e0dceec813b5c1917653c414aa101b7e4df321f28",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2128",
"name": "tactic:Defense Evasion",
"colour": "#518465",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2082",
"name": "audience-industry:Retail Banking",
"colour": "#185dda",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2163",
"name": "malware:ZPHP",
"colour": "#63867e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2118",
"name": "malware:Netsupport RAT",
"colour": "#7b6da8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2089",
"name": "malware:Astaroth",
"colour": "#34101f",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2129",
"name": "tactic:Credential Access",
"colour": "#f2b63f",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2130",
"name": "malware:Agent Tesla",
"colour": "#dfc4e0",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2132",
"name": "tactic:Collection",
"colour": "#b33ab0",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2140",
"name": "malware:Remcos",
"colour": "#9e7dc6",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2134",
"name": "tactic:Discovery",
"colour": "#c01e03",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
],
"Tag": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2128",
"name": "tactic:Defense Evasion",
"colour": "#518465",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2082",
"name": "audience-industry:Retail Banking",
"colour": "#185dda",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2163",
"name": "malware:ZPHP",
"colour": "#63867e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2118",
"name": "malware:Netsupport RAT",
"colour": "#7b6da8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2089",
"name": "malware:Astaroth",
"colour": "#34101f",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2129",
"name": "tactic:Credential Access",
"colour": "#f2b63f",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2130",
"name": "malware:Agent Tesla",
"colour": "#dfc4e0",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2132",
"name": "tactic:Collection",
"colour": "#b33ab0",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2140",
"name": "malware:Remcos",
"colour": "#9e7dc6",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2134",
"name": "tactic:Discovery",
"colour": "#c01e03",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false
}
],
"_AttributeFlattened": [
{
"id": "1324223",
"event_id": "58297",
"object_id": "0",
"object_relation": null,
"category": "Payload delivery",
"type": "sha256",
"to_ids": true,
"uuid": "14e999a2-2622-427d-9698-a5120da6dc74",
"timestamp": "1748464239",
"distribution": "5",
"sharing_group_id": "0",
"comment": "",
"deleted": false,
"disable_correlation": false,
"first_seen": null,
"last_seen": null,
"value": "3c54060447cd33a5aa4ce88e0dceec813b5c1917653c414aa101b7e4df321f28",
"Sighting": [],
"_allTags": [
{
"id": "10",
"name": "tlp:green",
"colour": "#33FF00",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2128",
"name": "tactic:Defense Evasion",
"colour": "#518465",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2082",
"name": "audience-industry:Retail Banking",
"colour": "#185dda",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2088",
"name": "attack-pattern:malspam",
"colour": "#8d99c8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2163",
"name": "malware:ZPHP",
"colour": "#63867e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2077",
"name": "attack-pattern:Phishing",
"colour": "#2976dc",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2118",
"name": "malware:Netsupport RAT",
"colour": "#7b6da8",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2089",
"name": "malware:Astaroth",
"colour": "#34101f",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2129",
"name": "tactic:Credential Access",
"colour": "#f2b63f",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2130",
"name": "malware:Agent Tesla",
"colour": "#dfc4e0",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2083",
"name": "audience-region:Americas",
"colour": "#d0832e",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2132",
"name": "tactic:Collection",
"colour": "#b33ab0",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2140",
"name": "malware:Remcos",
"colour": "#9e7dc6",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2134",
"name": "tactic:Discovery",
"colour": "#c01e03",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
},
{
"id": "2084",
"name": "attack-pattern:Credential pharming",
"colour": "#25961b",
"exportable": true,
"user_id": "0",
"hide_tag": false,
"numerical_value": null,
"is_galaxy": false,
"is_custom_galaxy": false,
"local_only": false,
"inherited": true
}
]
}
]
}
}