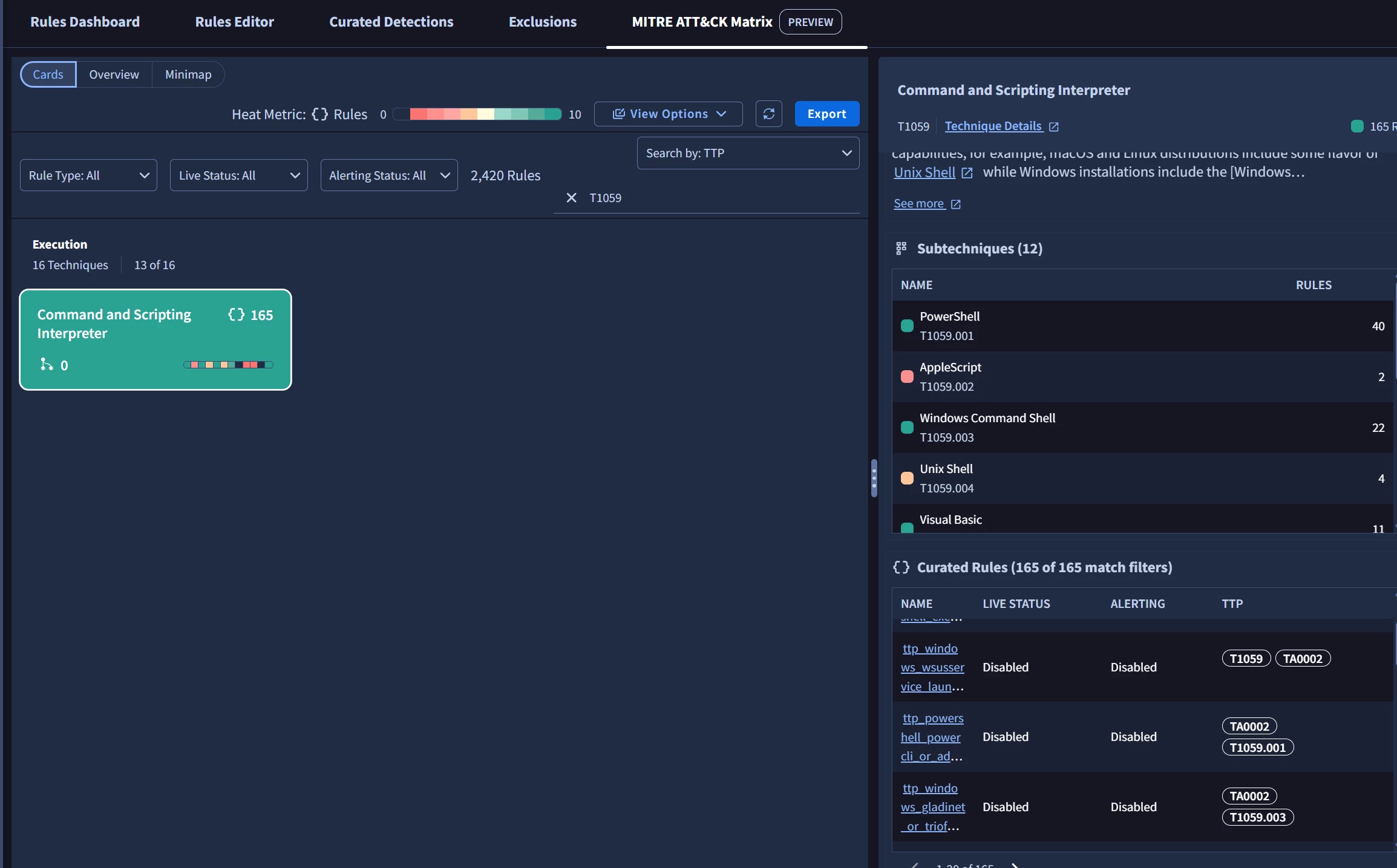
Hello Team,
We’re currently performing a MITRE ATT&CK analysis for the curated detections using the MITRE ATT&CK Matrix dashboard.
While the dashboard makes it easy to see how many rules exist per technique, identifying each rule’s corresponding rule name, rule set, and category is quite challenging — I have to review them individually. For techniques with a large number of rules, this becomes very time-consuming.
I’m focusing only on curated rules, and it seems that the Ruleset dashboard doesn’t support MITRE queries — the mapping appears to be available only in the rules field, which doesn’t seem to work for curated content.
Is there any way to generate a sheet like the example snippet below directly from the dashboard or through any other approach/tool?
Thanks in advance for your help!