1) Can we fetch Mitre attack details based on tactic ID
2) Can we fetch "Get all groups using all techniques." using technique ID
1) Can we fetch Mitre attack details based on tactic ID
2) Can we fetch "Get all groups using all techniques." using technique ID
To fetch mitre attack details based on the technique id (e.g. T1595), you could use the Mitre ATT&CK Integration (https://cloud.google.com/chronicle/docs/soar/marketplace-integrations/mitre-att-and-ck). There you have to use "external id" as the identifier. I'm not sure if it also works with the tactic id (e.g. TA0043). But it shouldn't be that difficult for the tactics to manage it themselves. I guess there aren't many changes to the tactics.
To fetch mitre attack details based on the technique id (e.g. T1595), you could use the Mitre ATT&CK Integration (https://cloud.google.com/chronicle/docs/soar/marketplace-integrations/mitre-att-and-ck). There you have to use "external id" as the identifier. I'm not sure if it also works with the tactic id (e.g. TA0043). But it shouldn't be that difficult for the tactics to manage it themselves. I guess there aren't many changes to the tactics.
we have already implemented enrich by technique id... i was looking for using tactic id
we have already implemented enrich by technique id... i was looking for using tactic id
I would just implement it myself. The data can be found here (https://github.com/mitre/cti/tree/master/enterprise-attack/x-mitre-tactic). Depending on how up to date you need the data, I would fetch the data or save the json locally.
I would just implement it myself. The data can be found here (https://github.com/mitre/cti/tree/master/enterprise-attack/x-mitre-tactic). Depending on how up to date you need the data, I would fetch the data or save the json locally.
How about
2) Can we fetch "Get all groups using all techniques." using technique ID
How about
2) Can we fetch "Get all groups using all techniques." using technique ID
Hello,
The current Marketplace integration has this functionality. The action is called "Get Associated Intrusions". This returns the information for the groups.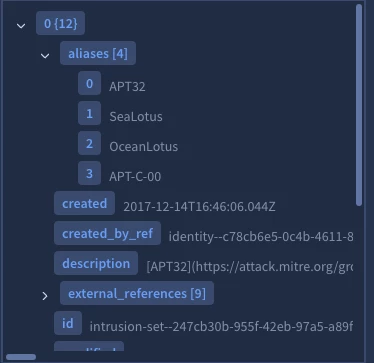
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.