Hello All,
I am trying to integrate O365 and Intune using the documentaiton from:
https://cloud.google.com/chronicle/docs/soar/marketplace-integrations/microsoft-intune
https://cloud.google.com/chronicle/docs/ingestion/default-parsers/collect-microsoft365
Unfortunately Intune is showing me this:
[HTTP 403] The auth account provided in feed configuration lacks required permissions.Here are the permissions. I really don't understand why it won't integrate properly:
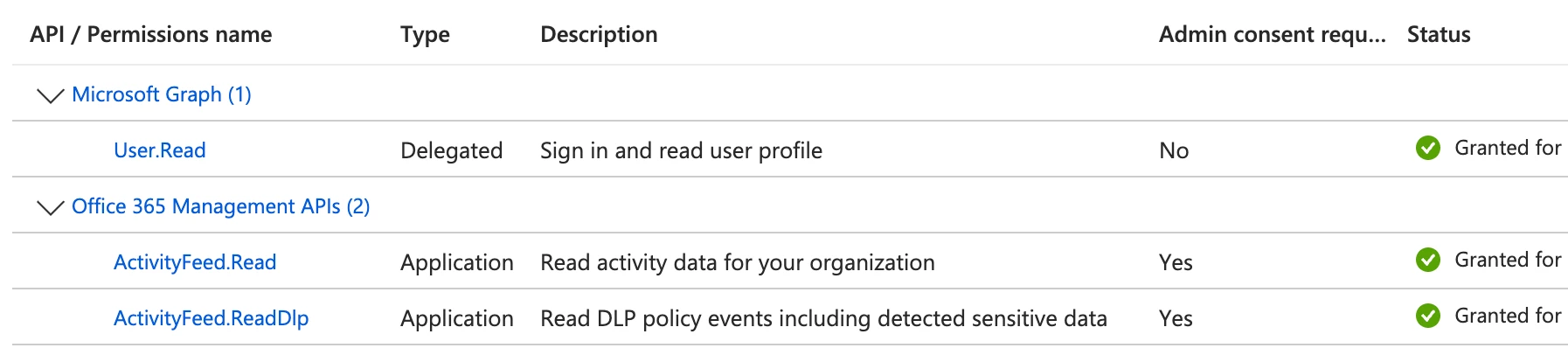
The log type is Third Party API - Intune although I get the same error for Graph API.
Secondly, with all O365 log types I get the following error:
Error: HTTP_400[HTTP 400] The feed failed because of invalid request.What you can do?Check the feed configuration. Learn more about setting up feeds. If the problem continues, contact Chronicle Support.
Again, I've followed the steps from John Stoner in the articles above and done everything here. Is there something I'm missing? Permissions below:
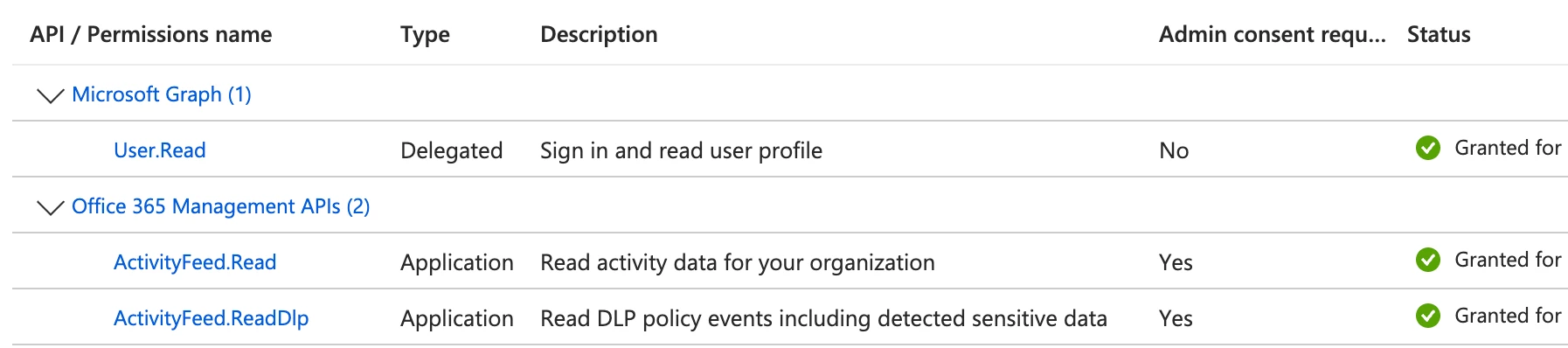
I would add that we don't have E5 licenses although surely we would still be able to see Intune/DLP activity?
Thank you