Hi All,
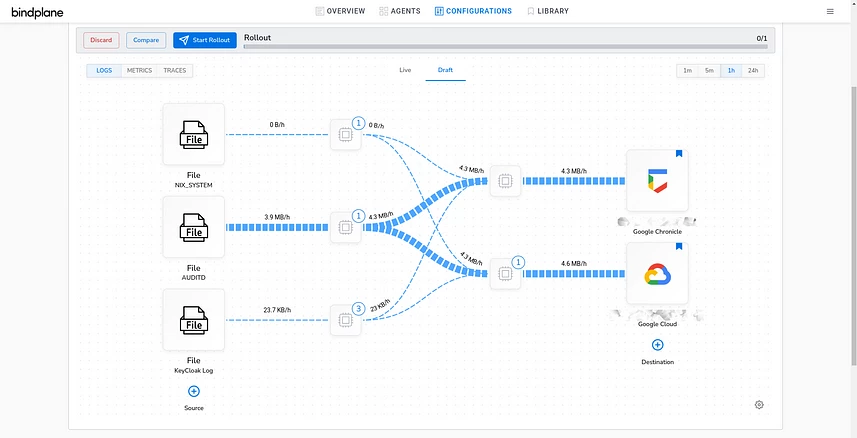
We're soon to be moving to SecOps and have a significant On-Prem footprint with a number of log sources.
I'm curious to learn what sort of logging infrastructure others in similar situations are using in your environment. I'm investigating options like fluentd, logstash, cribl etc. One of the requirements is that I don't have budget for big expensive solutions.