Hi Team,
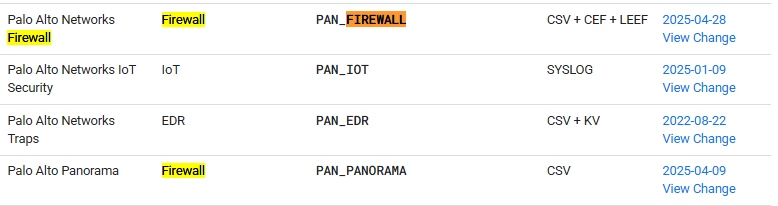
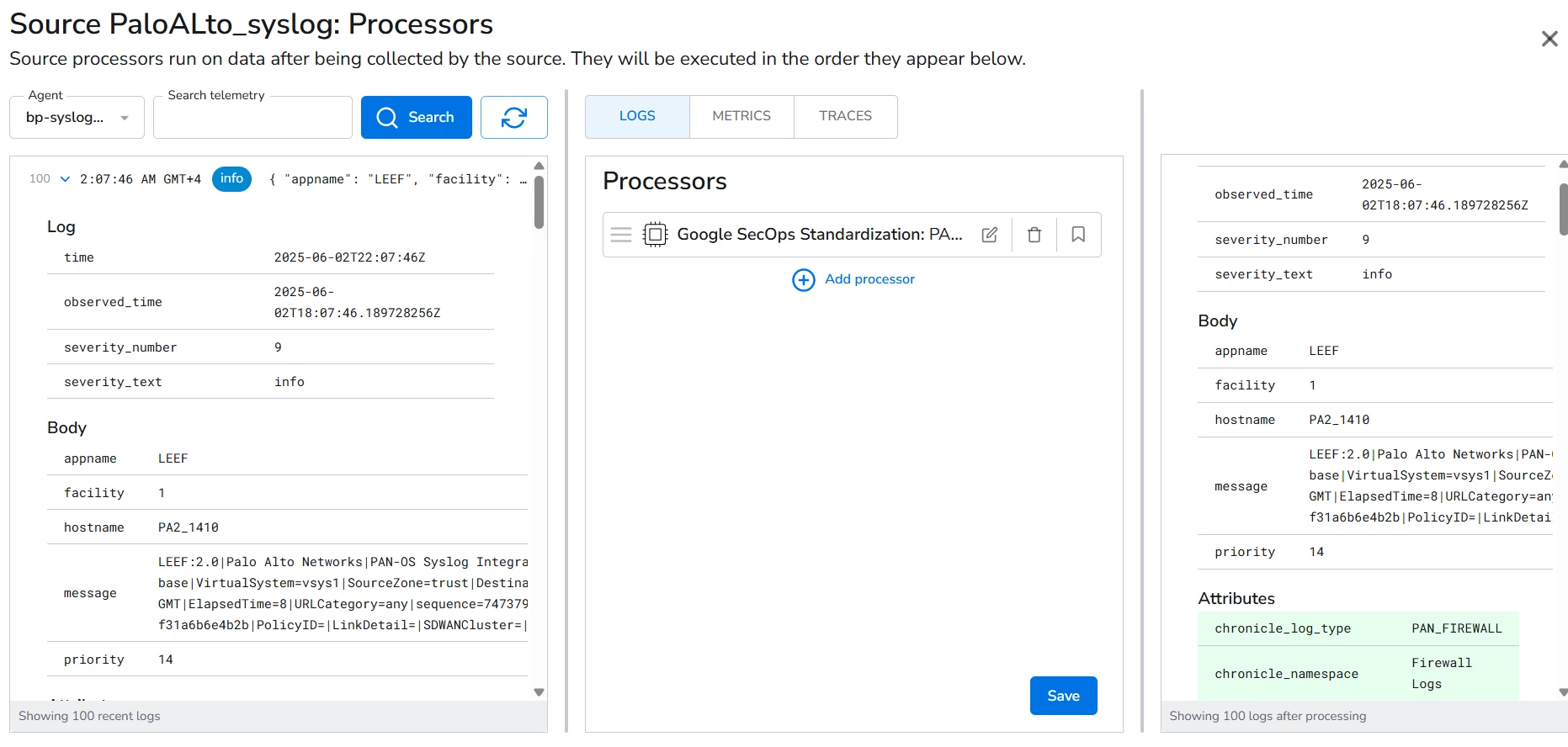
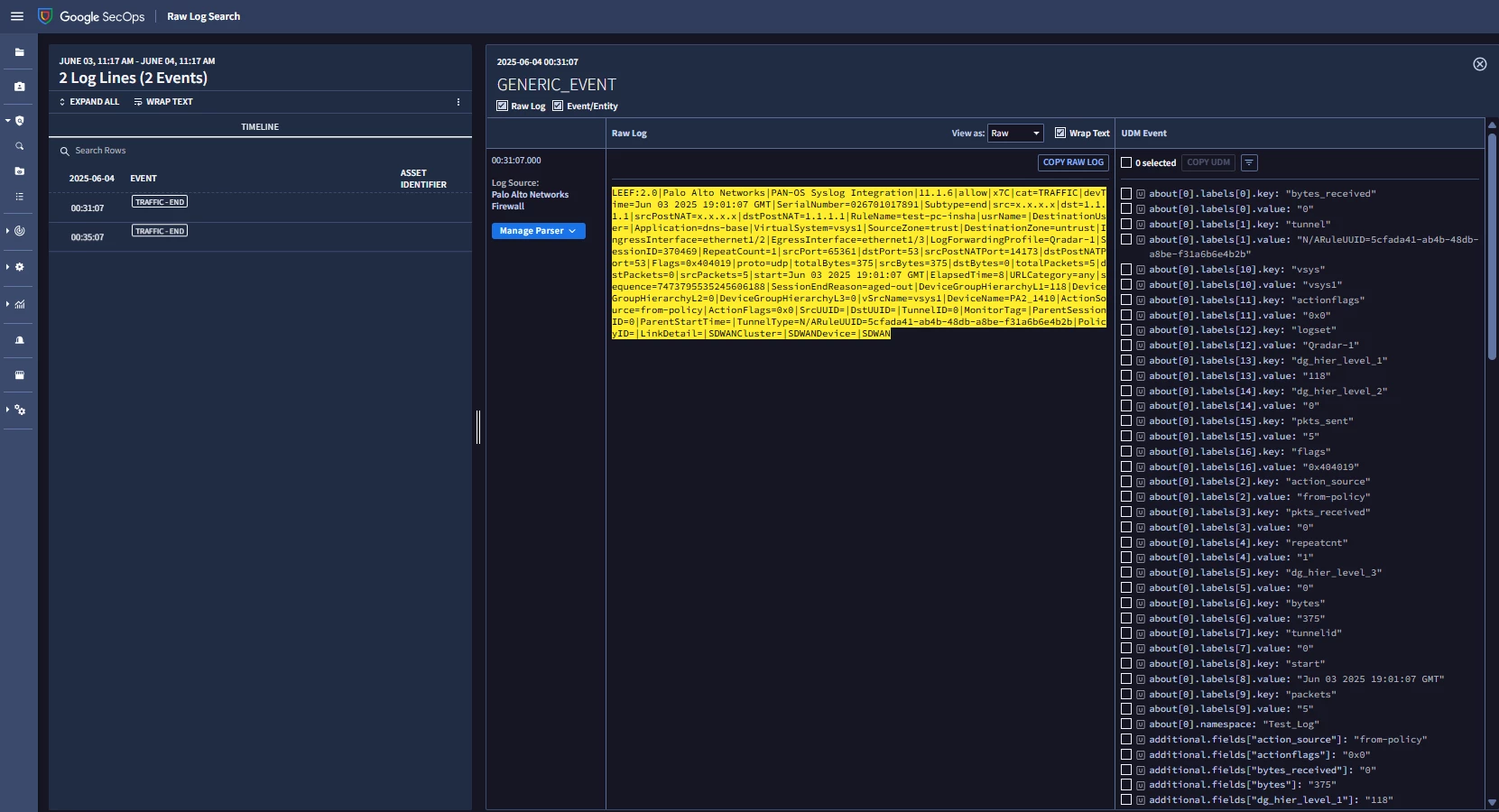
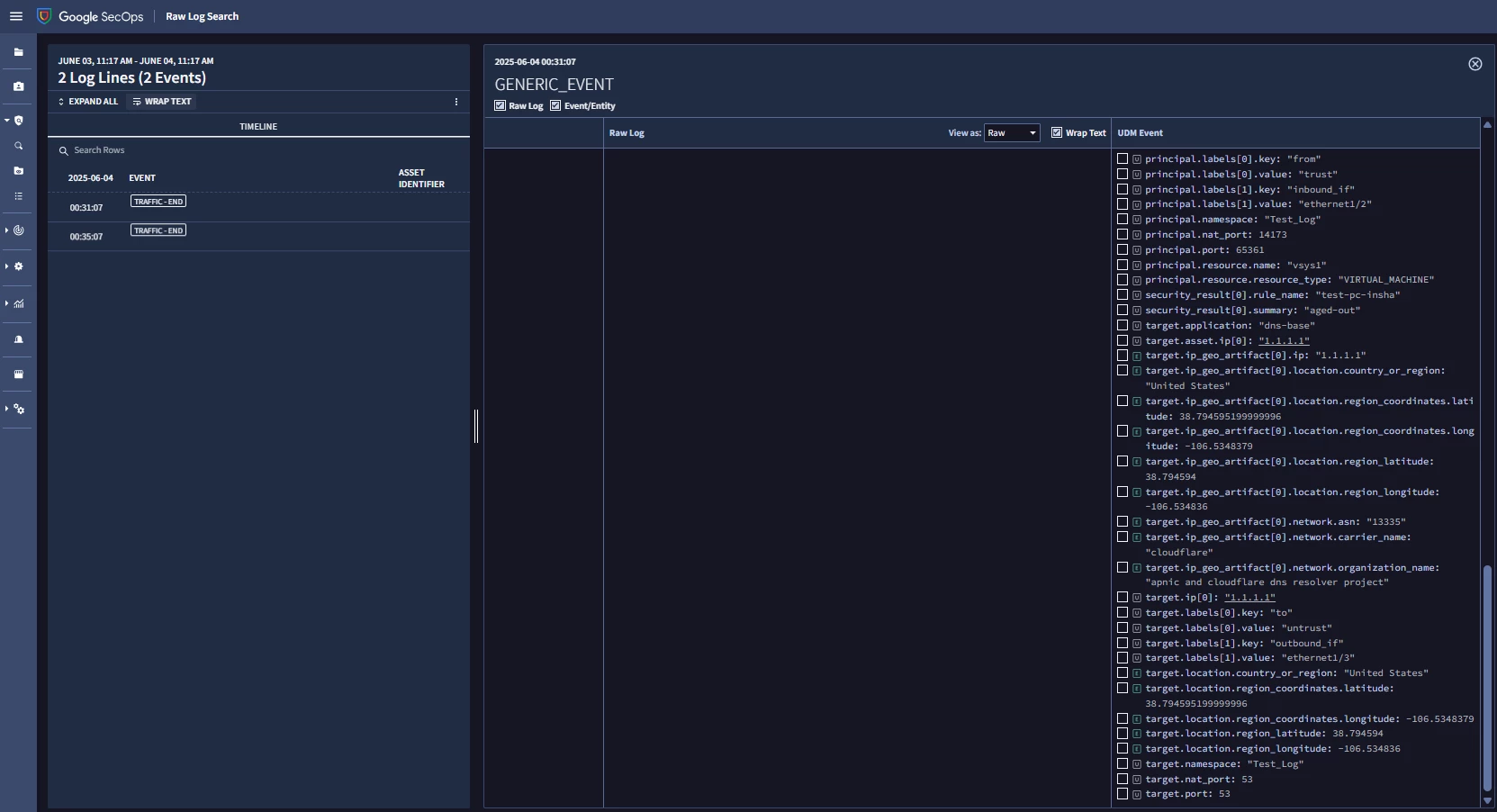
I am new to the Chronicle. I am collecting the logs from paloalto firewall using the bindplane server and able to see the logs in Secops but the logs are not getting parsed . I used the log type as "PAN_FIREWALL" in the processor configuration and the logs are in the LEEF Format.
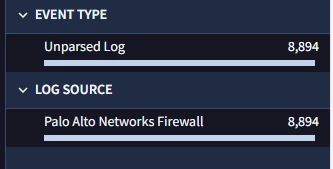
Please advise what mistake I am doing here.
Thanks
Joe