Hello!
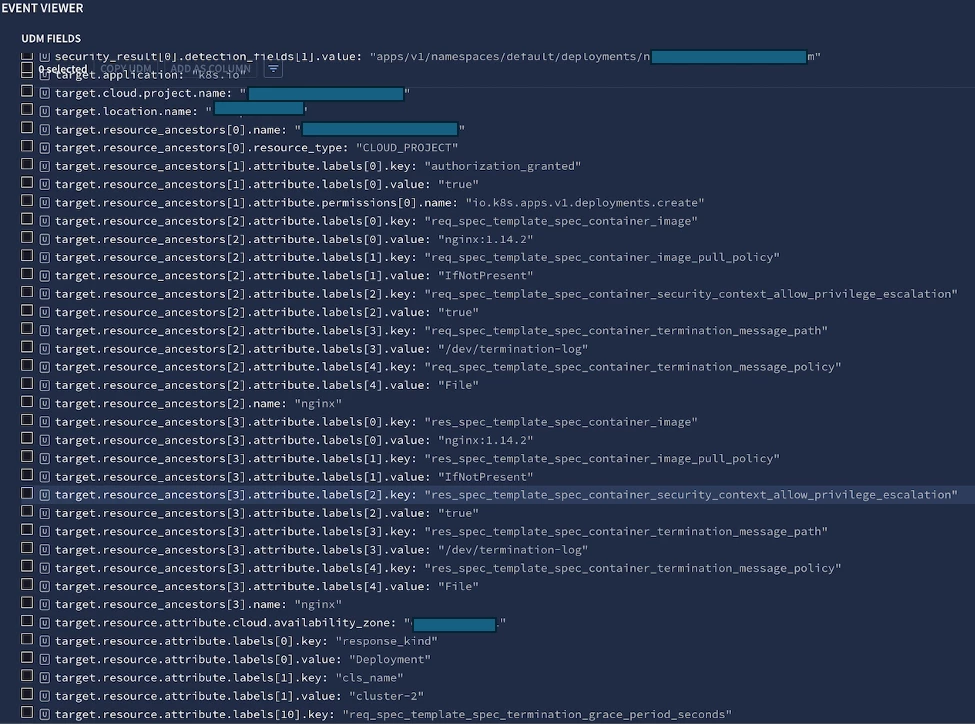
When a deployment is created in Kubernetes, it is possible to add a field as part of the securityContext named runAsUser. If the value in this field is 0, that means the deployment is run as root, which is not good at all from a security perspective. So, we would like to detect when this happens using Chronicle.
In the documentation (https://cloud.google.com/chronicle/docs/ingestion/default-parsers/collect-audit-logs), it is possible to see an entry that ends with runAsUser, so that means the parser is able to do so. Also in the code it is shown:
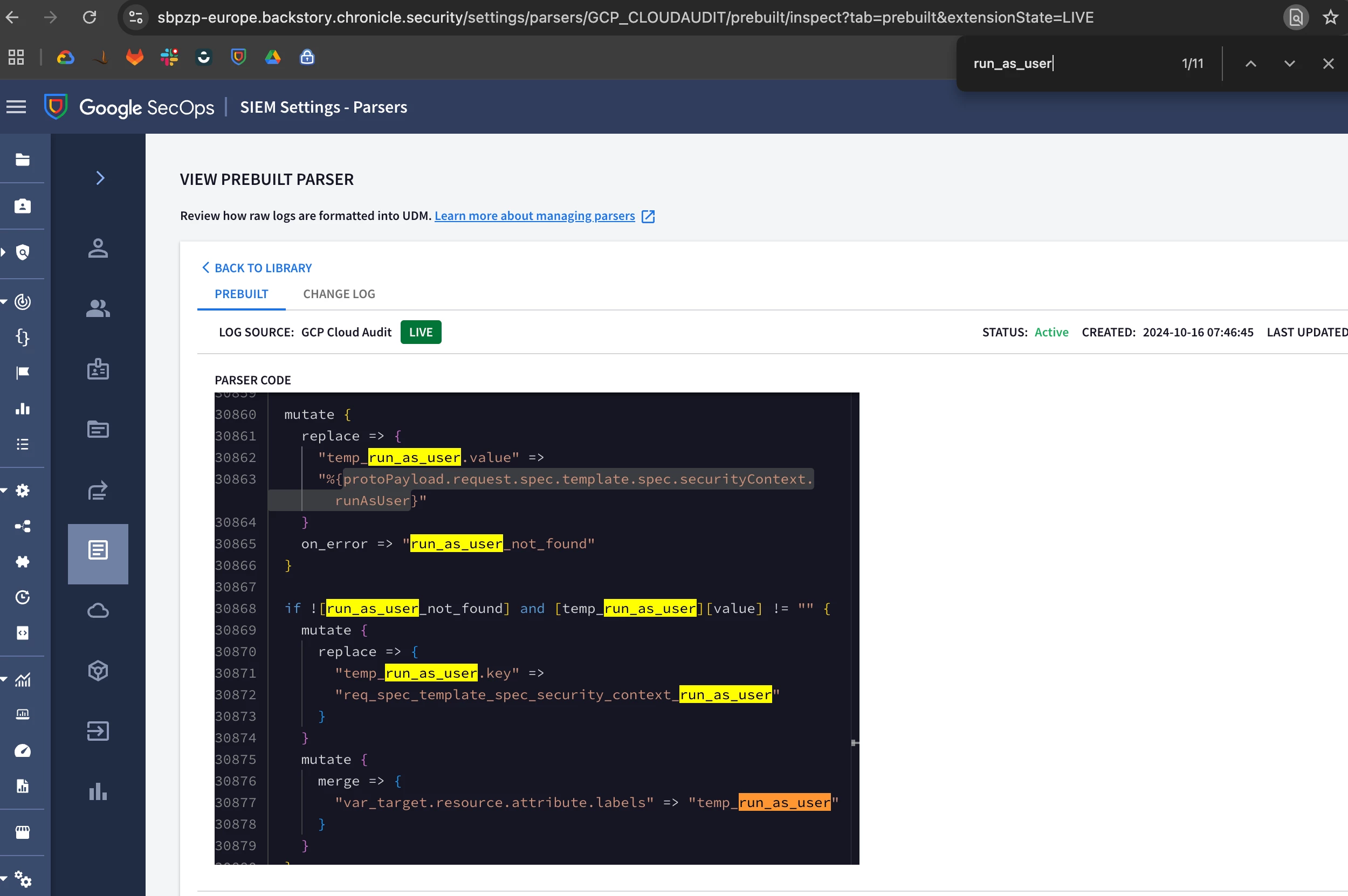
But when I create the deployment and SecOps process it, the field is not display. What could I do?