Good Day,
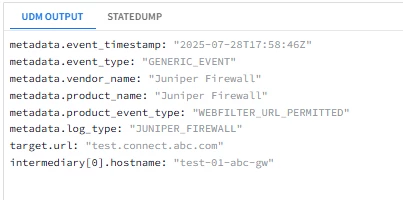
I am trying to write a parser extension for JUNIPER FIREWALL. I am trying to map the field URL to target.url but when I try and validate the parser it fails with “failed to evaluate expression: generic::invalid_argument: \"domain\" not found in state data". How do I get it to only match the extension when it sees this specific log type that the prebuilt parser doesn’t fully parse out.
The raw log is as follows:
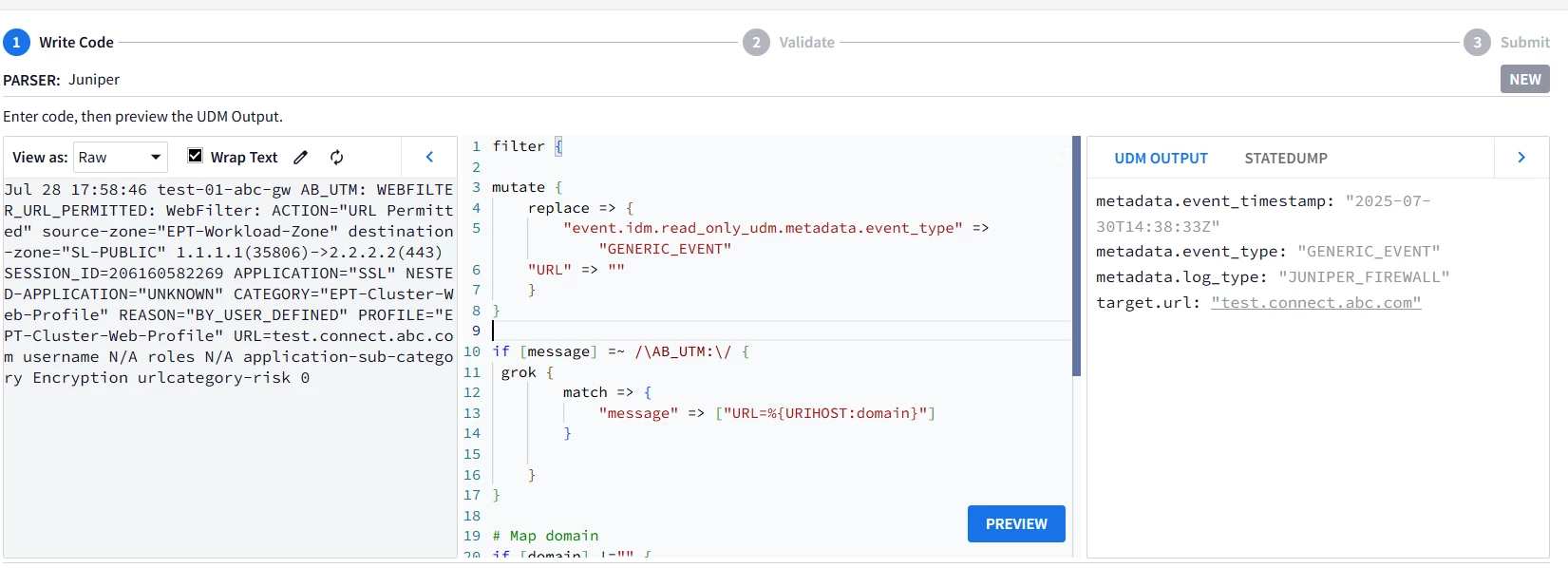
Jul 28 17:58:46 test-01-abc-gw AB_UTM: WEBFILTER_URL_PERMITTED: WebFilter: ACTION="URL Permitted" source-zone="EPT-Workload-Zone" destination-zone="SL-PUBLIC" 1.1.1.1(35806)->2.2.2.2(443) SESSION_ID=206160582269 APPLICATION="SSL" NESTED-APPLICATION="UNKNOWN" CATEGORY="EPT-Cluster-Web-Profile" REASON="BY_USER_DEFINED" PROFILE="EPT-Cluster-Web-Profile" URL=test.connect.abc.com username N/A roles N/A application-sub-category Encryption urlcategory-risk 0
Parser Syntax is as follows:
filter {
mutate {
replace => {
"URL" => ""
}
}
if [message] =~ /\AB_UTM:\/ {
grok {
match => {
"message" => ["URL=%{URIHOST:domain}"]
}
}
}
# Map domain
if [domain] !="" {
mutate {
replace => {
"event.idm.read_only_udm.target.url" => "%{domain}"
}
on_error => "invalid.target.url"
}
}
mutate {
merge => {
"@output" => "event"
}
}
}