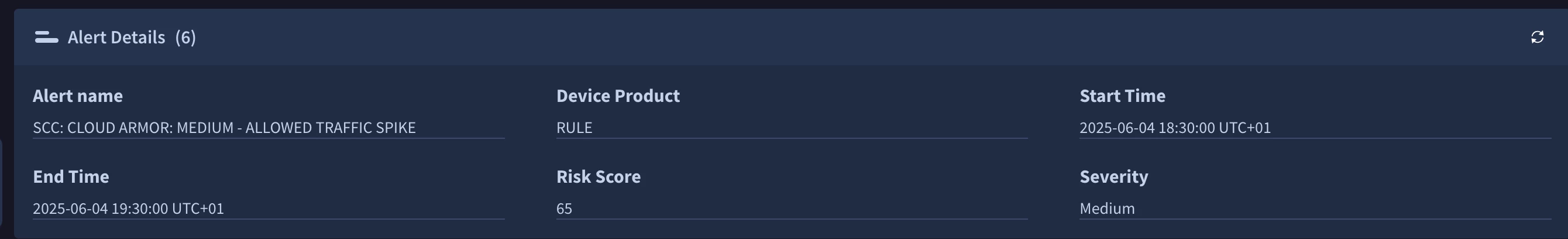
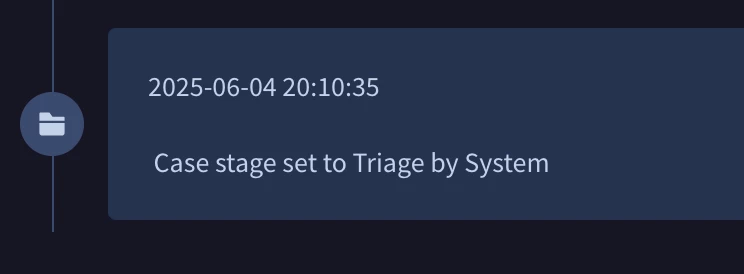
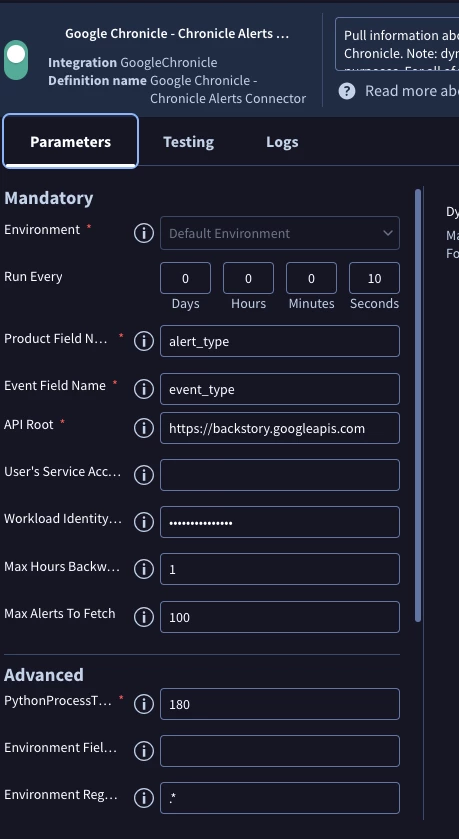
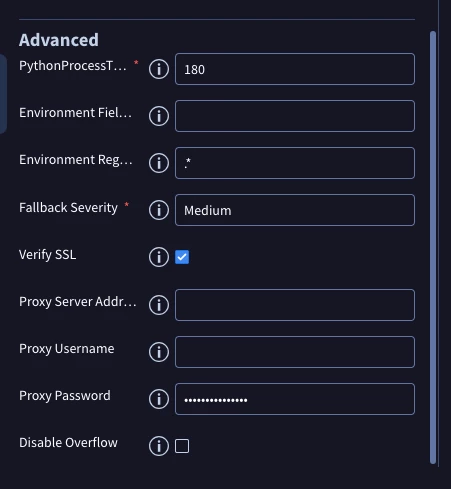
We are experiencing a significant delay between alert ingestion into Google SecOps (Chronicle SOAR) and the subsequent creation of a case. Our goal is to have a case created almost immediately when the first alert for a potential incident is ingested, provided a relevant case doesn't already exist.
Additionally, we are facing an issue with our playbook automation. Our current setup executes a playbook after a case is created in Google SecOps. This playbook is designed to create a ticket in our external SOC ticketing system. However, when subsequent related alerts are ingested into the same Google SecOps case, the playbook seems to re-trigger (or a similar process does), resulting in multiple tickets being created in our SOC ticketing system for what is essentially the same underlying incident. This creates unnecessary noise and administrative overhead for our SOC team.
We have attempted to use alert grouping with a 1-hour window and a maximum of 3 alerts, but this configuration has not resolved either the initial case creation delay or the duplicate SOC ticket issue.
Could you please provide guidance on the following:
- Minimizing Case Creation Delay: What configurations or best practices can we implement to ensure that a case is created in Google SecOps as soon as the first relevant alert is ingested?
- Preventing Duplicate SOC Tickets: How can we configure our Google SecOps cases and/or playbooks to ensure that only one ticket is created in our external SOC ticketing system when the first alert triggers case creation, and that subsequent alerts ingested into that same Google SecOps case do not generate new tickets in the external system? We need the playbook to recognize that a ticket for that SecOps case already exists.