Hey everyone,
We have an issue with restricting access to a SecOps instance.
Before, the provisioning procedure required an IDP group mapped to Chronicle's backend to grant access to users in said group. This meant that if a user was not part of the IDP group, they could not access Google SecOps. This was the case even if you used Cloud Identity.
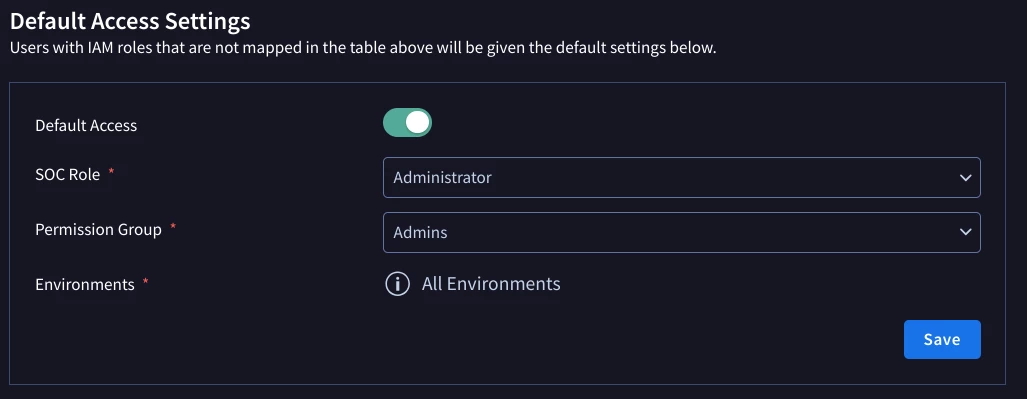
However, recently, this provisioning has changed. Now a provisioning wizard pops up and you can directly choose Cloud Identity, which makes it easier as you can now control access with GCP IAM and assign roles to any user within your GCP IAM console. However we have an issue with this new way.
We have to restrict access to only a specific group within IAM BUT users that have the EDITOR role at Org level still have access to Google SecOps and this should NOT be the case. We have tried applying a Deny policy BUT the roles associated to Chronicle in IAM are not included in DENY policies.
Does anyone have an idea of how we can restrict access to ONLY a specific group?