I am trying to wrap my head around outcomes section in YARA-L. Apart from the documentation, I am also looking at this blog.
My queries are tied in to the example in the aforementioned blog post.
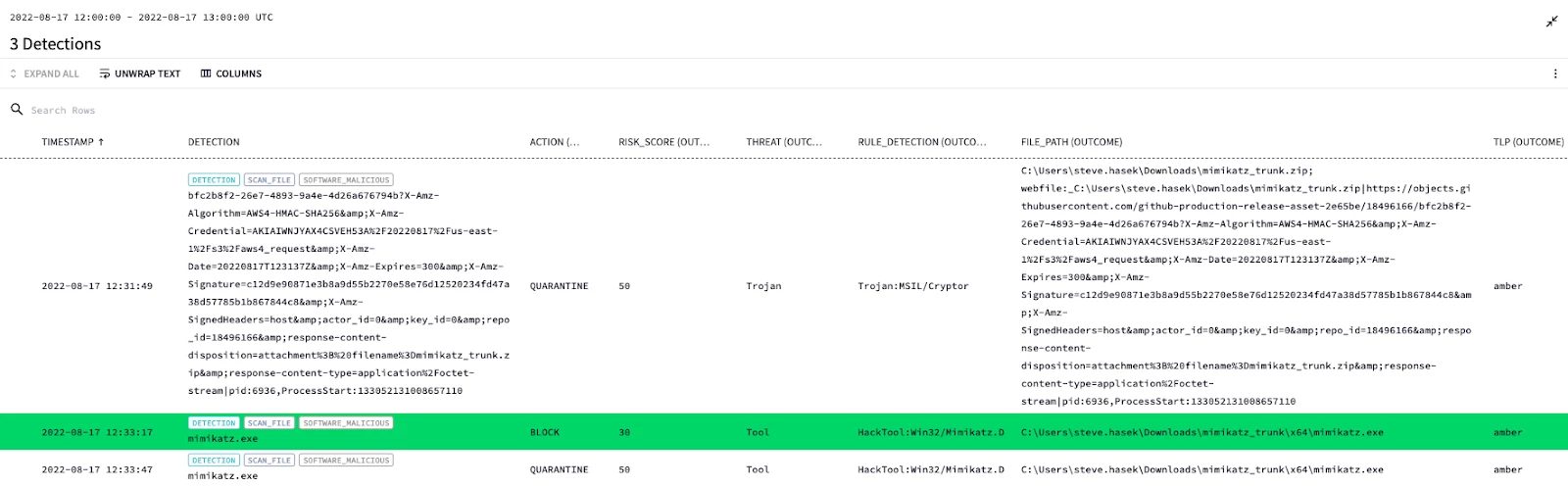
How is the following a single-event rule? The way I am thinking about it, a single-event should be comprised of a single UDM field. But here more than one UDM field is being evaluated to determine if criteria exists for the rule to fire. Can you please help me figure where I am going wrong in thinking about this.
The blog post says: The outcome section will contain values that we want to provide with our detection to add further context to the detection. What does the latter exactly mean?
Use of outcome in single event
events: $event.metadata.event_type = "SCAN_FILE" $event.security_result.category = "SOFTWARE_MALICIOUS" $event.security_result.action = $secAction $event.security_result.threat_name = $threatname $event.security_result.rule_name = $rulename $event.target.file.full_path = $targetfilepath outcome: $risk_score = max(100 - if($secAction = "QUARANTINE", 50, 0) - if($secAction = "BLOCK", 70, 0)) $action = array_distinct($secAction) $threat = array_distinct($threatname) $rule_detection = array_distinct($rulename) $file_path = $targetfilepath $tlp = "amber" condition: $event and $risk_score > 49