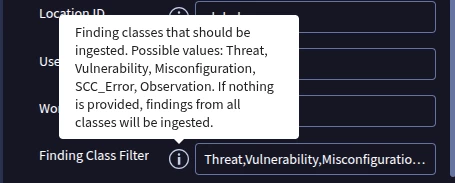
For SCCE customers, there’s a a SOAR SCC Enterprise Response Integration that can be used for ingesting Toxic Combination findings and syncing their status. What should I use if I have SCCP and SecOps? I can’t find the SCC Enterprise integration on the Marketplace. I can’t also import it from another instance.
A detection rule in SIEM would be the easiest way to go but it looks like a new log is written in SIEM every time the toxic combination finding is updated by SCC engine.
Any suggestions?