Hello Google Community Members,
I wonder if there is way to search for logs that were part of an alert.
Example query:
target.ip = "random_ip_that_triggered_an_alert"
magicAlertFlag =/true/ ?
is something like that possible?
Hello Google Community Members,
I wonder if there is way to search for logs that were part of an alert.
Example query:
target.ip = "random_ip_that_triggered_an_alert"
magicAlertFlag =/true/ ?
is something like that possible?
Best answer by ajohnson11
If you are searching a specific IP/entity and want to see if it has been associated with any rule detections in the time frame under the "Alerts" tab:
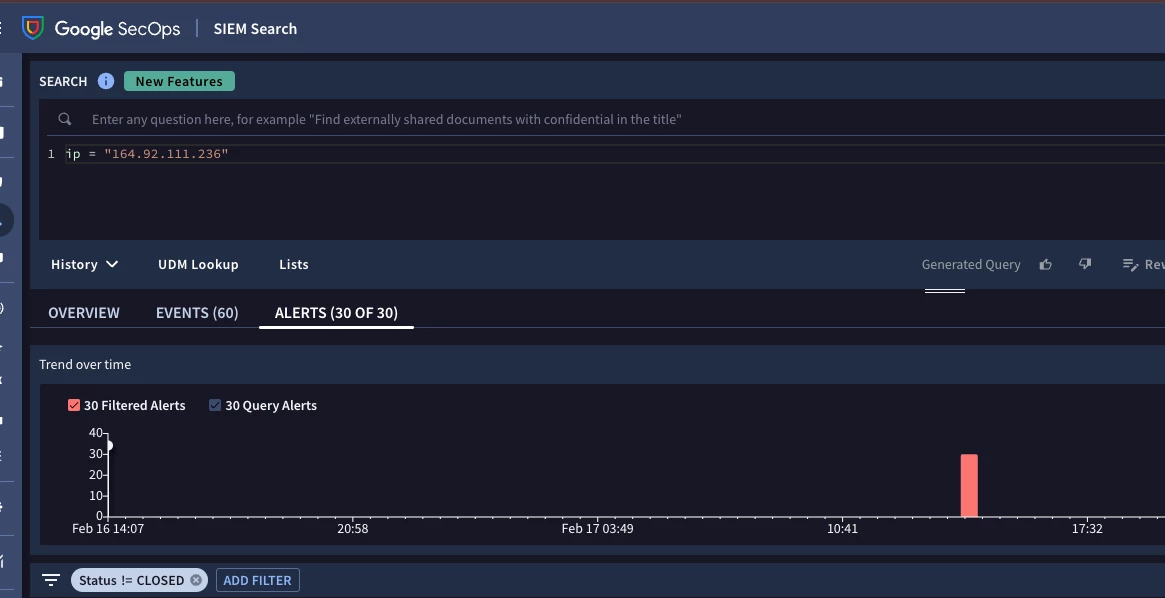
If there was a detection from a rule, the UDM events that triggered the detection should show at the bottom:
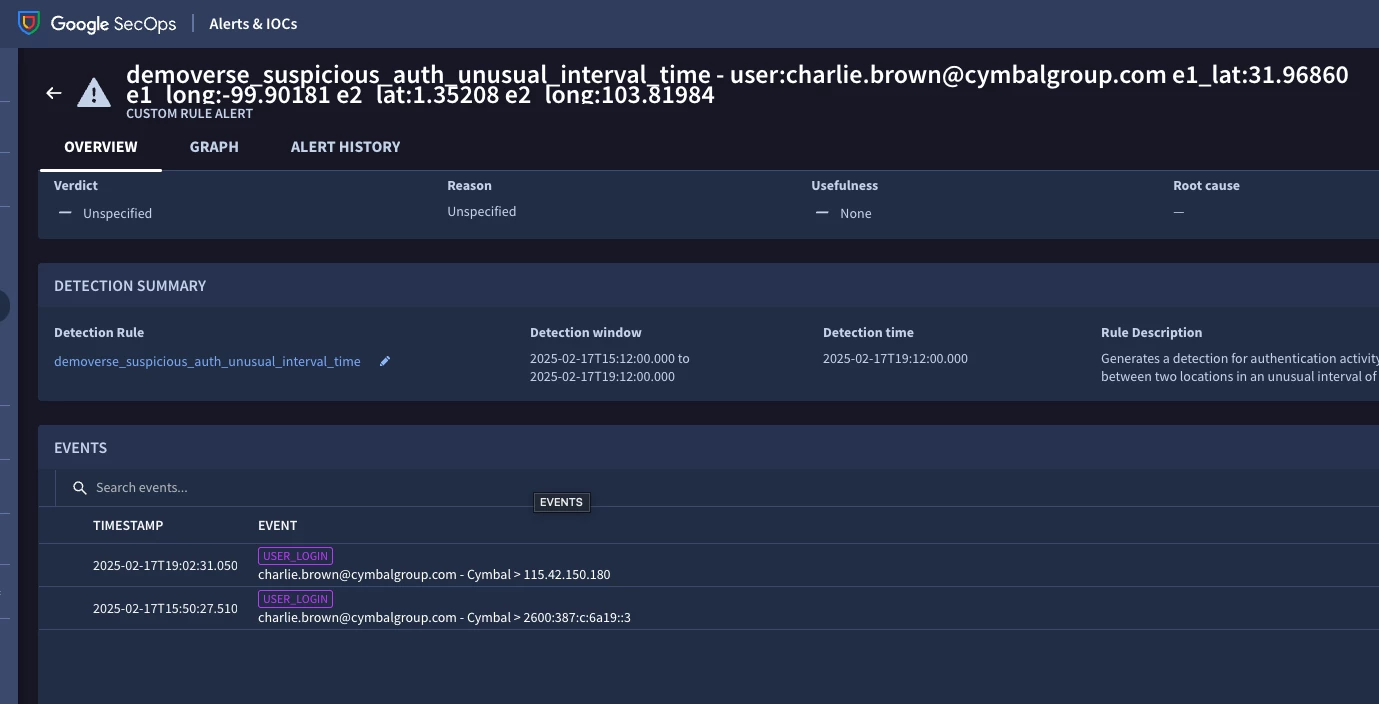
From there you could compare and select the UDM fields that match the YARA-L logic and begin searching upon those.
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.