Hello everyone, hope you're all having a great day!
I tried searching on documentations and in this forum for this specific message but had no success.
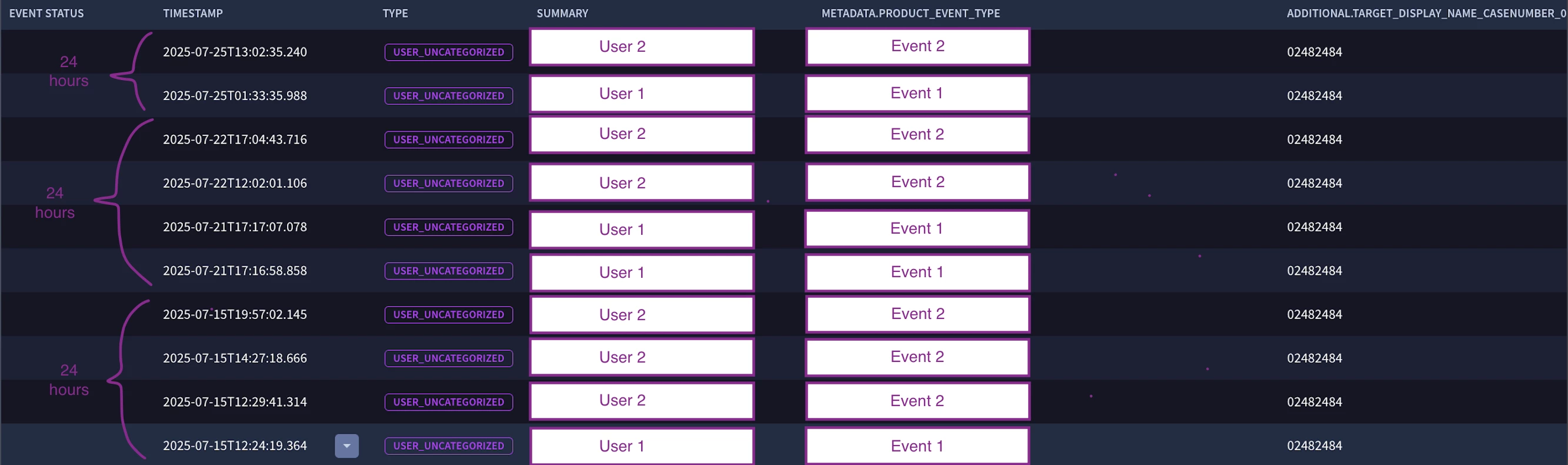
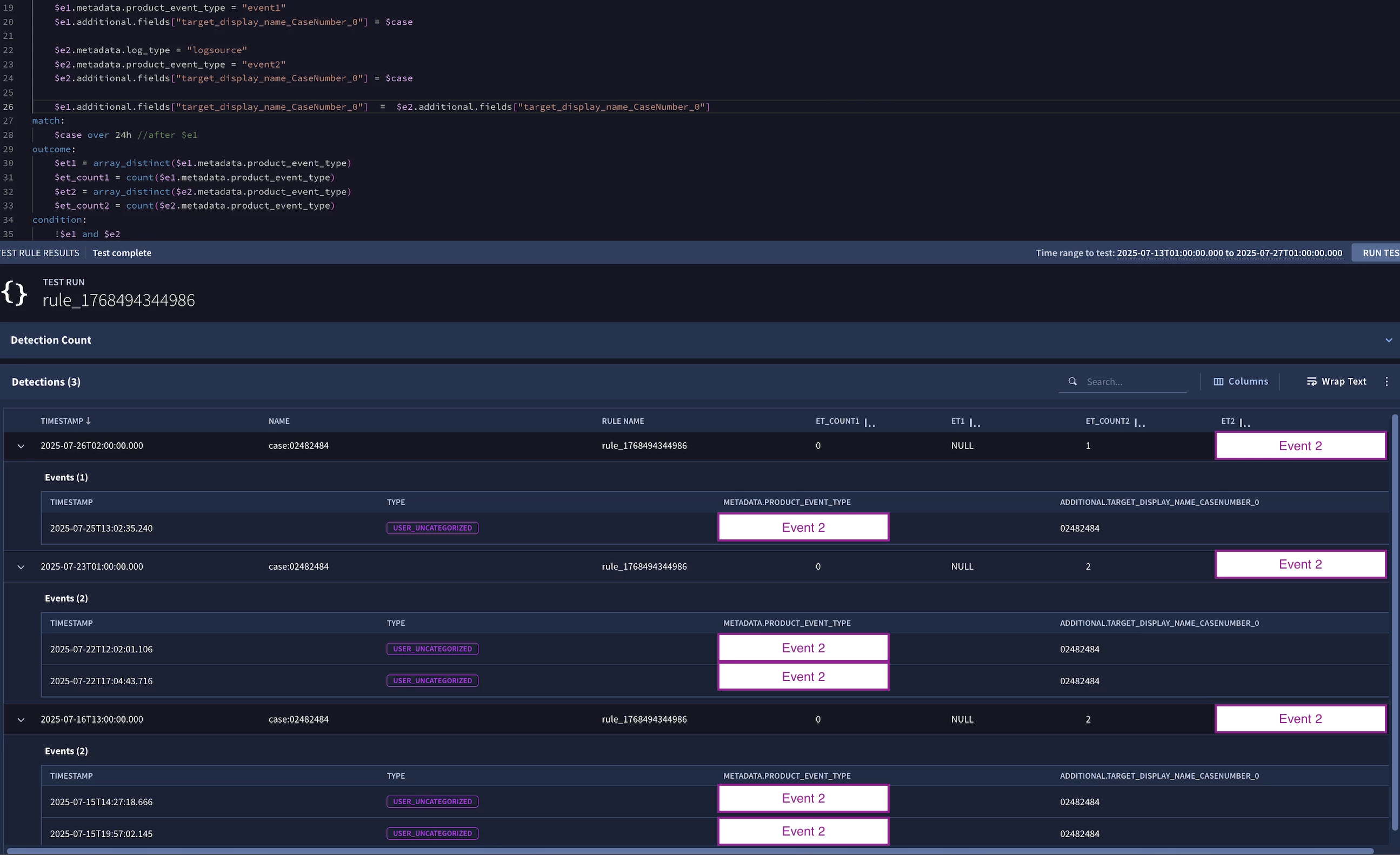
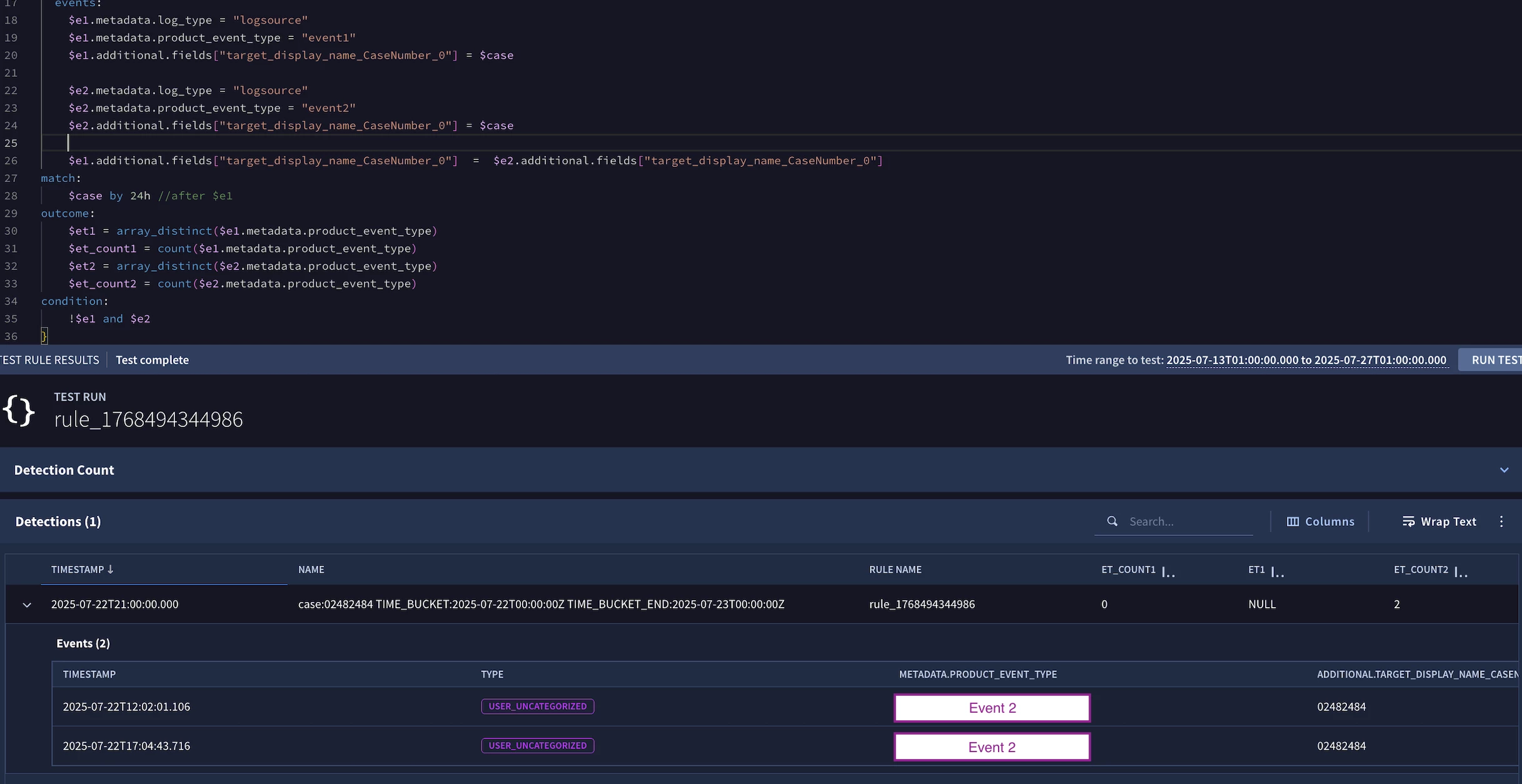
I'm currently working in the following detection (Parameters were made generic for sharing purposes).
The objective of this rule is to detect any occurrence of Event2 for which, in a 24 hours span previous to it's timestamp, there's no Event1 with a mutually shared eventcasenumber value;
events:
$e1.metadata.log_type = "logsource"
$e1.metadata.product_event_type = "event1"
$e1.metadata.product_event_type = $event1
$e2.metadata.log_type = "logsource"
$e2.metadata.product_event_type = "event2"
$e2.metadata.product_event_type = $event1
$e1.additional.fields["eventcasenumber"] = $e2.additional.fields["eventcasenumber"]
match:
$event2 over 24h after $event1
condition:
#e1 = 0 and #e2 > 0
I'm getting the following error and I couldn't find any reference in documentations or in posts here, I have no clue what it actually means.
semantic analysis: pivot event variable $event1 is not properly bounded
Does anyone knows what this error means and how to "bound" the pivot event variable?
Compiling works fine if a remove the "after $event1" portion of Match, but this line proved essential for proper grouping of logs based on my testings.
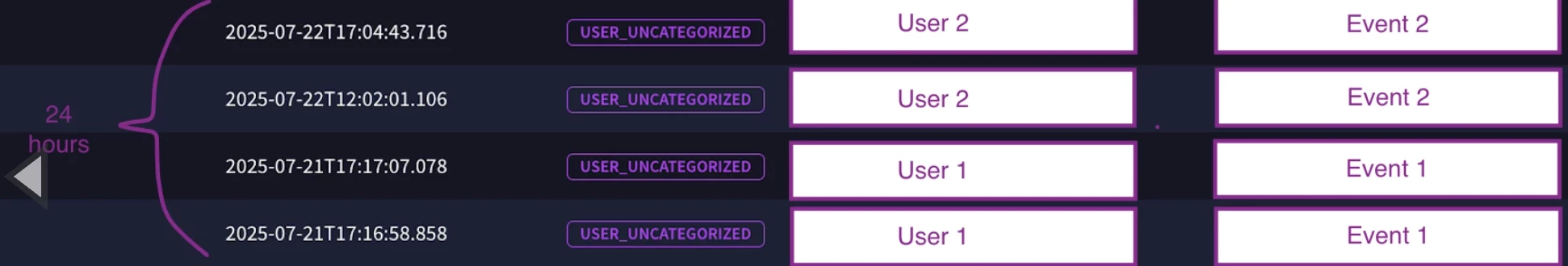
Without it, grouping of events is messed up and it alerts event2 occurrences that clearly have a matching Event1 within a 24h timespan with shared eventcasenumber.
For context:
- Event1 and 2 are related to a support action from the system, so they must share a common eventcasenumber;
- Event1 is an authorization for Event2 to happen;
- Event1 authorization is valid for 24hours and multiple Event2 are permitted in a 24hours span.
- After 24 hours a new Event1 log is expected. It may share the same casenumber as previous Event1 authorizations.
Appreciate any light you can shed, thanks all!