Hello, Google support team.
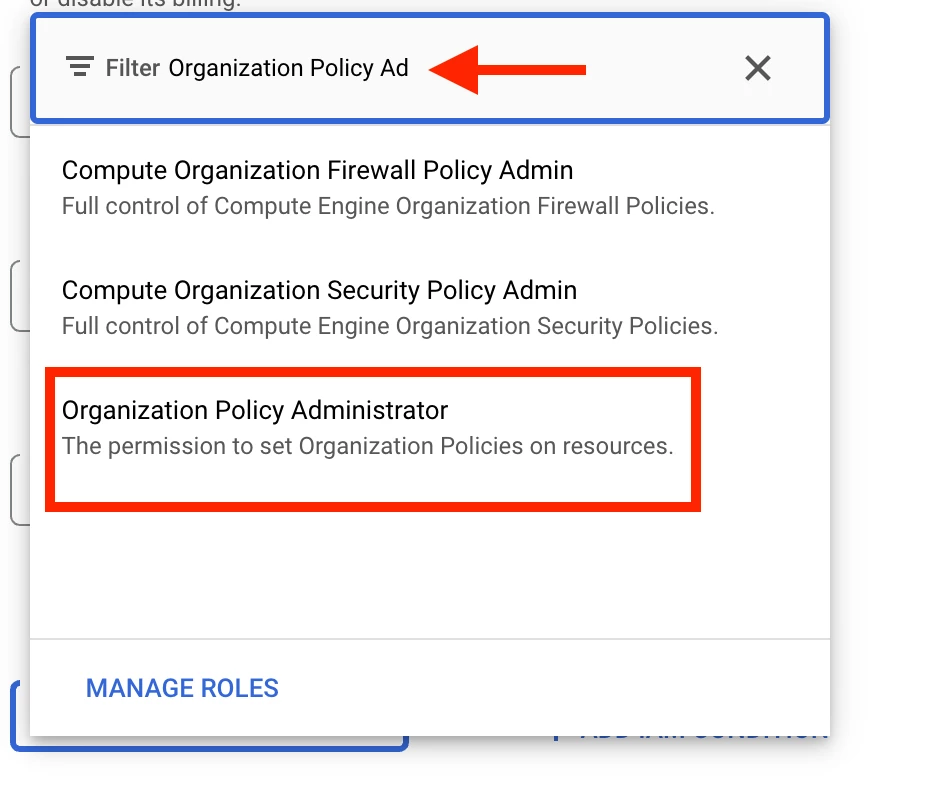
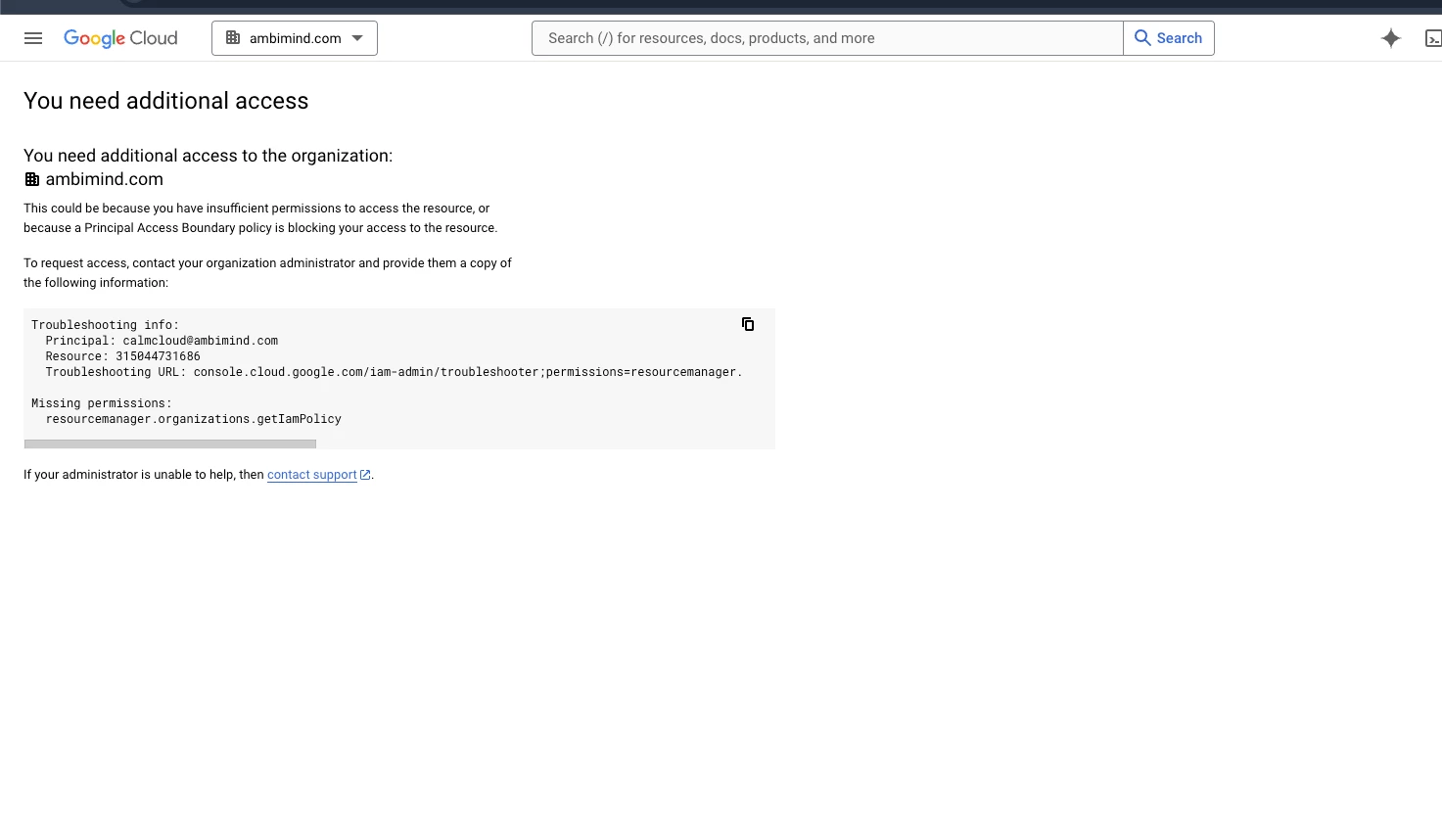
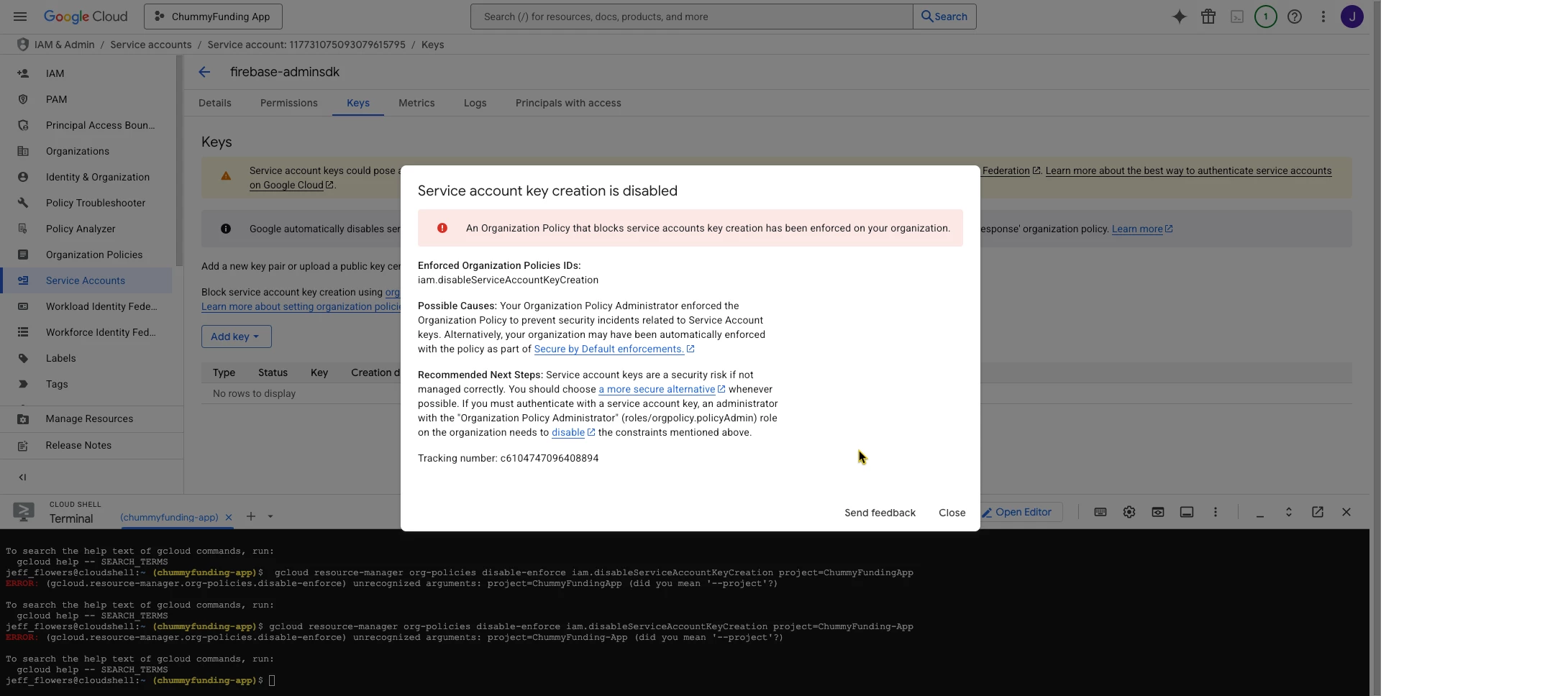
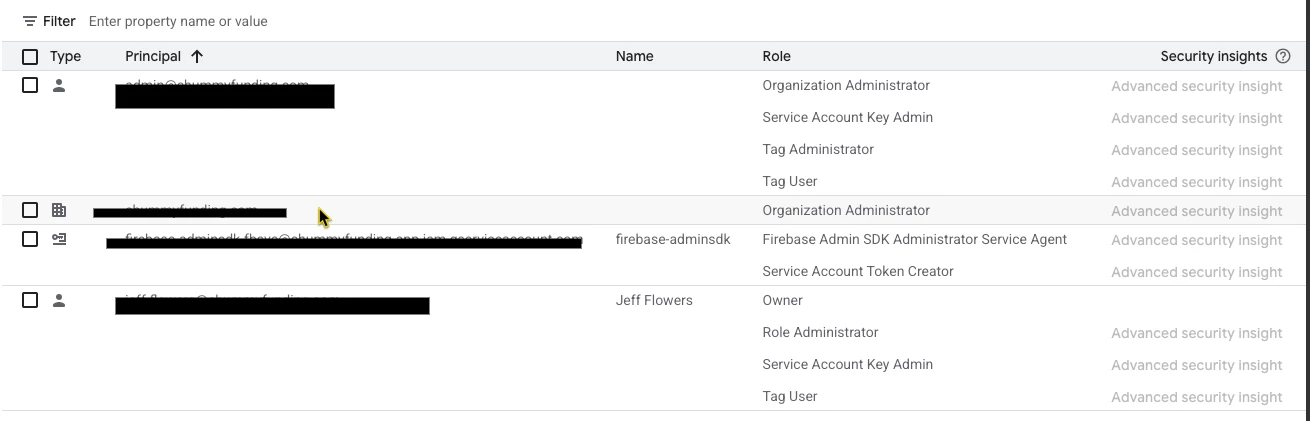
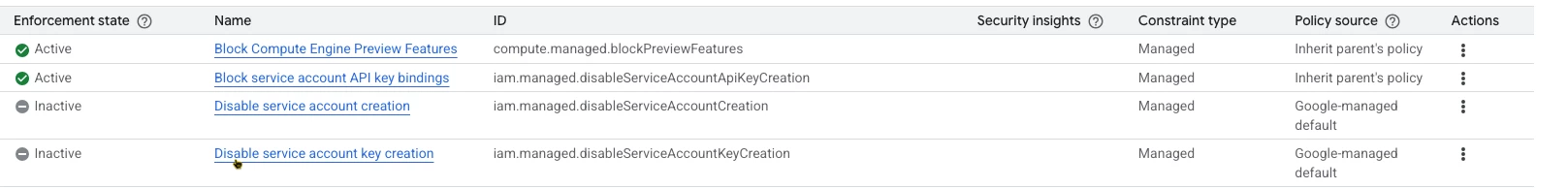
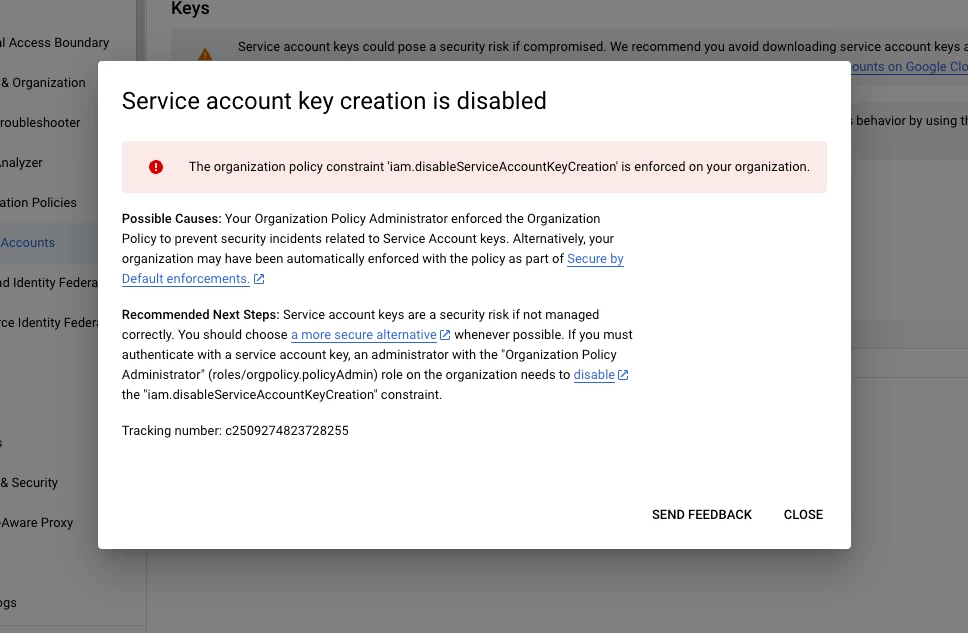
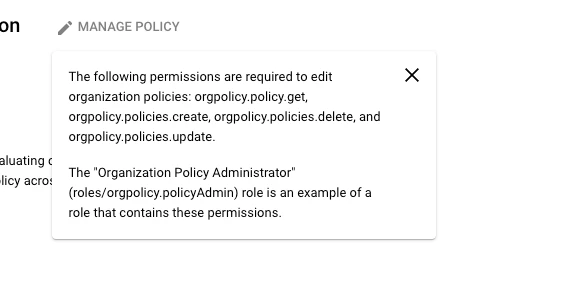
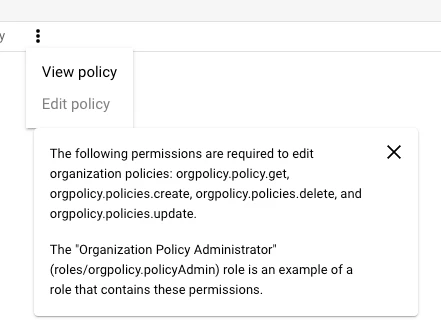
I'm trying to crate a or download a json file for firebase push notifications. while creating the json file i'm facing an issue "The organization policy constraint 'iam.disableServiceAccountKeyCreation' is enforced on your organization." which is mentioned in the screenshot.
Can you please help or provide us any way of doing things right.
Thanks.





 .
.