Hi,
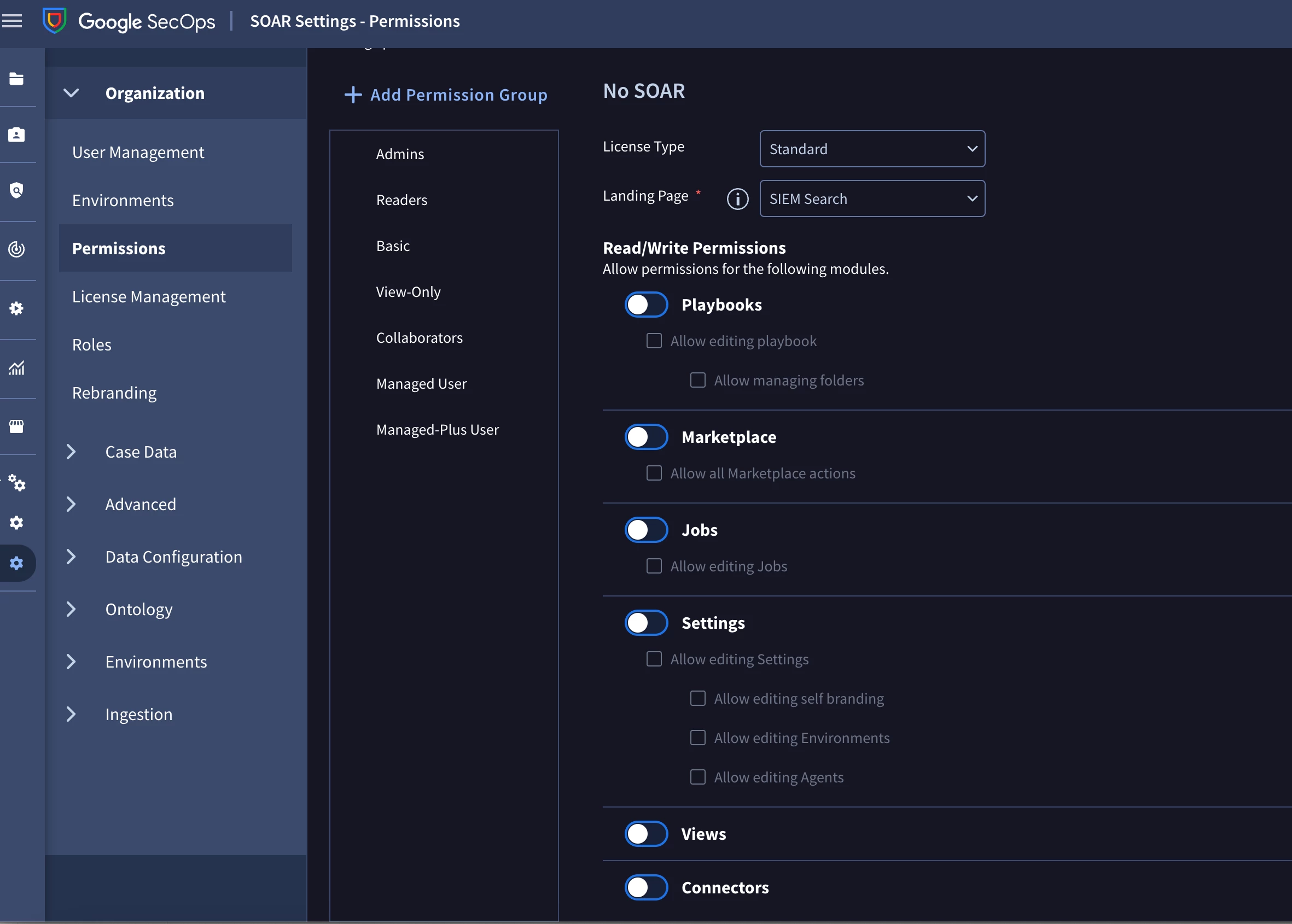
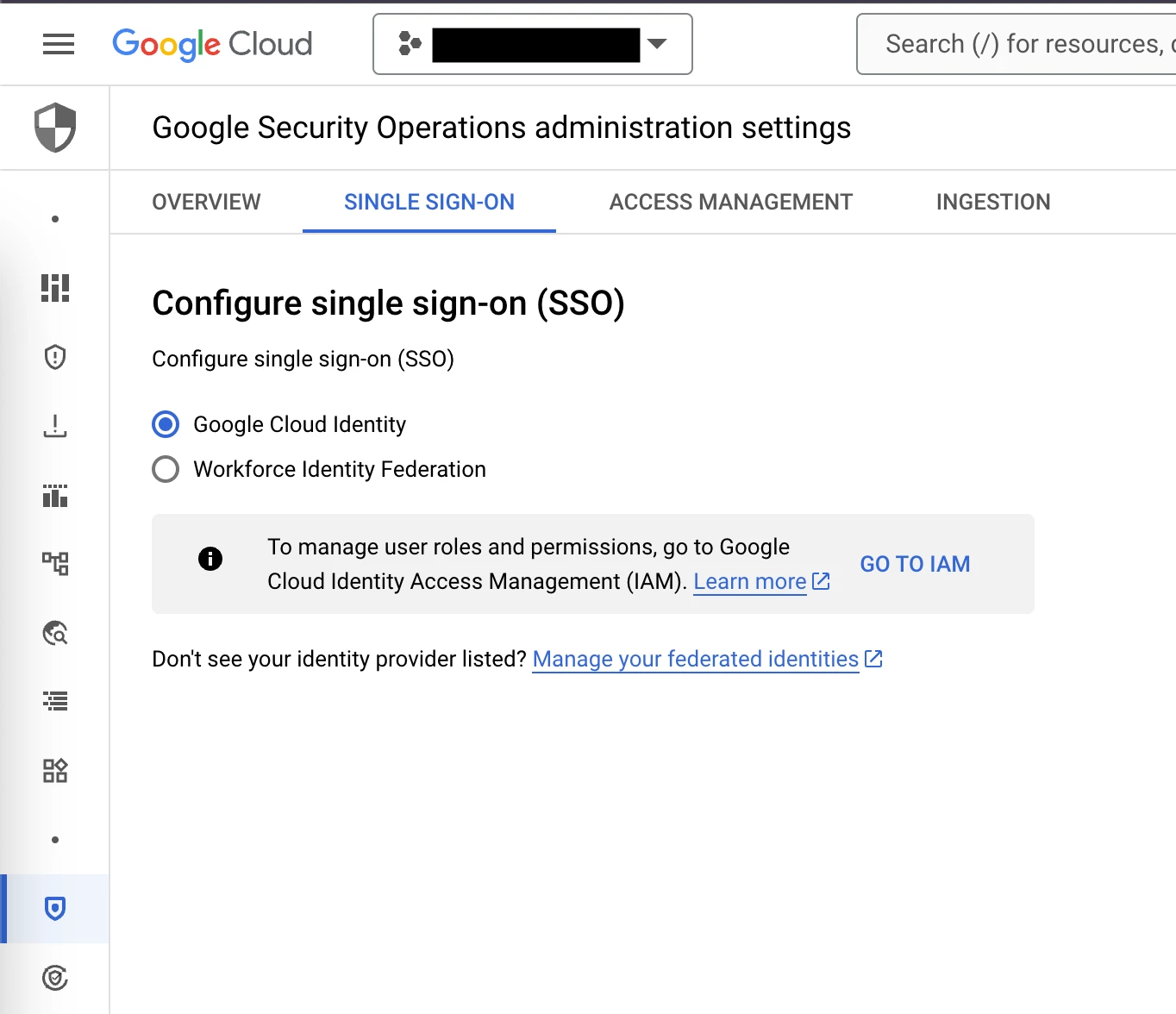
I need to create a users' group that would only be granted access to the SIEM parts of the SecOps instance or potentially, have the ability to only also access a specific environment on the SOAR.
I tried to follow this guide, but the information there is incorrect.
Can anyone share the minimum roles or permissions for that?
These are the permissions that I assigned to the group of users that the user belongs to:
chronicle.dataAccessScopes.get
chronicle.dataAccessScopes.list
chronicle.instances.get
chronicle.instances.report
chronicle.operations.get
chronicle.operations.list
resourcemanager.projects.get
This is the error I'm getting:
Thanks