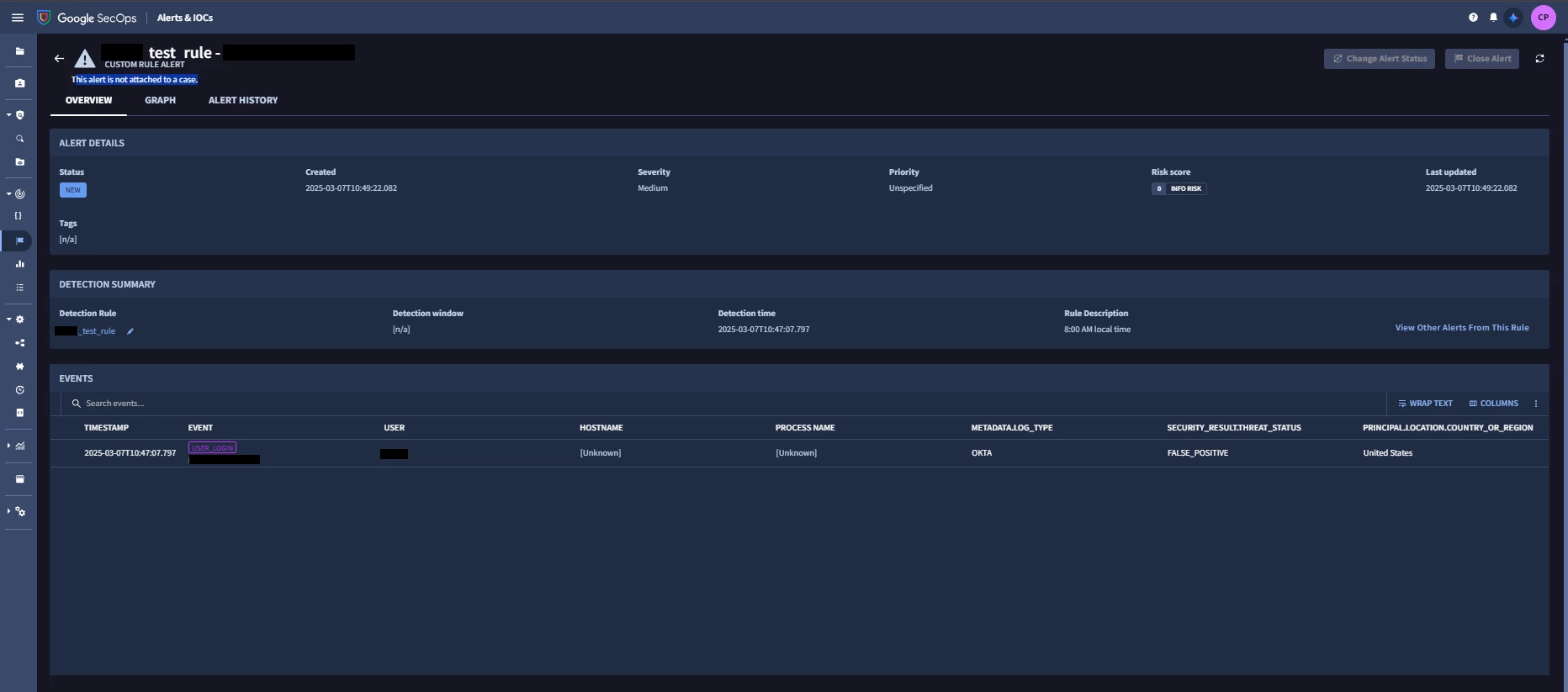
We have some simple detections that need to each trigger their own playbook. It seems you have to have a case to run the playbook, which means they each need to make their own case.
For example, I have a new_asset detection and I want to run a simple playbook that emails a DL for each detection with "Deleted Asset {asset_name}" in the subject. (This is a simple example that may be able to occur via a job or something else instead, but ignore that please. For the purpose of the question, it needs to run a playbook)
It does appear I could do this via a job that searches detections and creates cases. I tried to do something like this but I don't see API docs that show how to create the case from the job
It seems that _K_O might have figured it out here, but I could not find this endpoint in API docs anywhere "/api/external/v1/cases/CreateManualCase": https://www.googlecloudcommunity.com/gc/SecOps-SOAR/SecOps-IDE-Case-Creation-Issue-Add-Case-Description/m-p/872609