Meta:
description = "Use case triggers when a Crowdstrike Detect event is generated"
match:
$log_id over 5m
outcome:
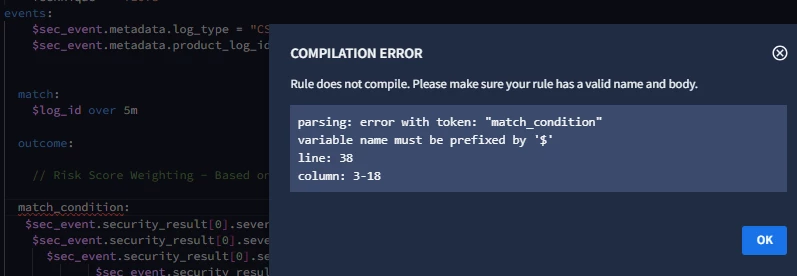
// Risk Score Weighting - Based on Detection Severity Output
$risk_score = max(if($sec_event.security_result[0].severity = "INFORMATIONAL", 10, 0)) +
max(if($sec_event.security_result[0].severity = "MEDIUM", 50)) +
max(if($sec_event.security_result[0].severity = "HIGH", 70)) +
max(if($sec_event.security_result[0].severity = "CRITICAL", 100))
$commandline = array_distinct($sec_event.principal.process.command_line)
$log_type = array_distinct($sec_event.metadata.log_type)
$hostname = array_distinct($sec_event.principal.asset.hostname)
$signature = array_distinct($sec_event.metadata.description)
$url_back_to_product = array_distinct($sec_event.metadata.url_back_to_product)
$src_user = array_distinct($sec_event.principal.user.userid)
$target_user_sid = array_distinct($sec_event.target.user.windows_sid)
$asset_id = array_distinct($sec_event.principal.asset.asset_id)
$process_file_full_path = array_distinct($sec_event.principal.process.file.full_path)
$principal_file_md5 = array_distinct($sec_event.principal.process.file.md5)
$principal_file_sha1 = array_distinct($sec_event.principal.process.file.sha1)
$principal_file_sha256 = array_distinct($sec_event.principal.process.file.sha256)
$target_file_full_path = array_distinct($sec_event.target.file.full_path)
condition:
#sec_event >= 1
}
Could ypu please suggest me and optimise the query i tried in multiple ways in optimizing Sha files and the conditional values to triggers, but looking more optimized consistent way of results.
TIA.