Hi
I am trying to build an alert
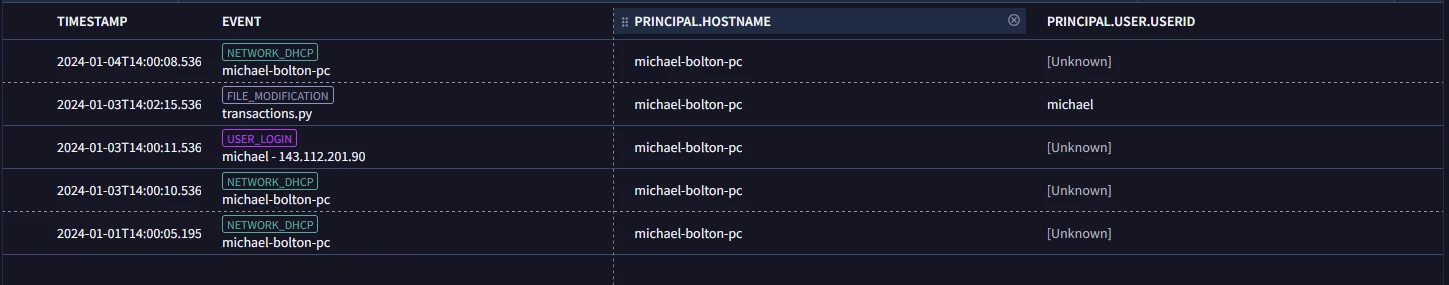
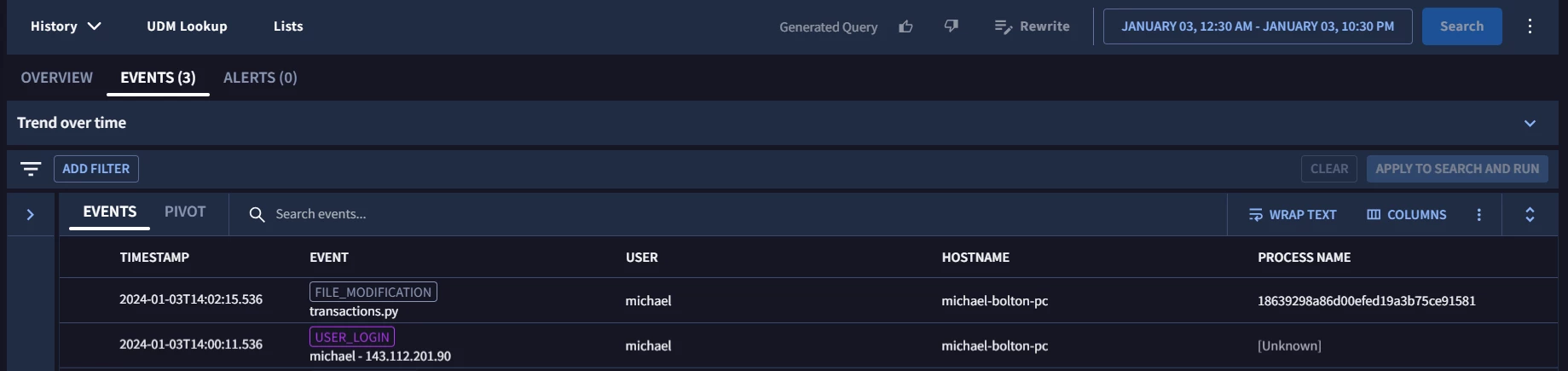
What i am trying to achieve is on a particular time for same user on the same machine there should more than 1 of the event type . However my below query is not triggering this detection. Can you suggest where i am going wrong ? Also is there a SLACK channel where we can get interact for such doubts ?
Query i created is this
rule Multiple_endpoint_changes {
meta:
author = "Rahul"
description = "It detects an abnormally large number of endpoint changes per user account, as they relate to reboots, checks, file system, user, and registry changes."
severity = "Medium"
events:
(
$e.metadata.event_type = "FILE_MODIFICATION" or
$e.metadata.event_type = "USER_LOGIN" or
$e.metadata.event_type = "USER_CHANGE_PERMISSIONS" or
$e.metadata.event_type = "REGISTRY_MODIFICATION" or
$e.metadata.event_type = "SERVICE_MODIFICATION" or
$e.metadata.event_type = "SYSTEM_AUDIT_LOG_WIPE"
)
$e.principal.hostname = "michael-bolton-pc"
$e.principal.user.userid = "michael"
$e.principal.hostname = $hostname
$e.principal.user.userid = $userid
$e.metadata.event_type = $event_type
match:
$hostname,$userid over 15m
condition:
#event_type > 1
}