Hello Community,
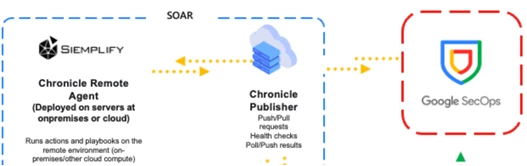
I am trying to clearly understand the design and deployment model of Google SecOps SOAR Remote Agents, specifically when the target systems (for example, FortiGate firewalls or other on-prem security tools) are hosted inside a private customer network.
I would like clarification on the following points:
-
Hosting Model
-
Do we need to create a VM in the customer private network to host remote agent?
-
Is the Remote Agent always expected to run on a dedicated VM or server inside the customer’s private network?
-
Is this the recommended and supported architecture for interacting with internal devices such as firewalls, AD, or other non-internet-exposed systems?
-
-
Allowing Access for Remote Agent to Google Publisher and Firewall