Hi All
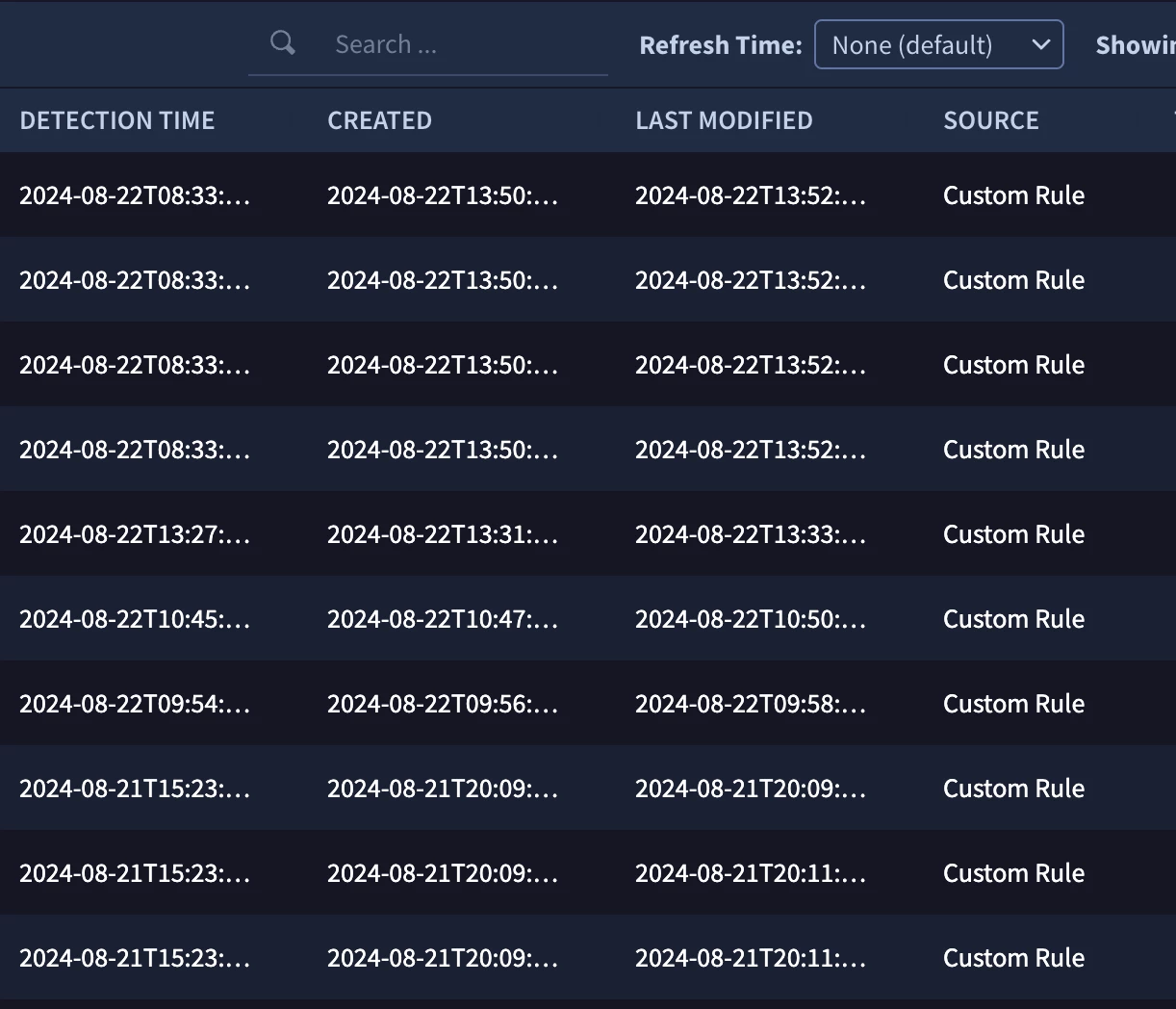
Can someone tell me what the Last modified time in the Detection > Alerts menu in Google SecOps means?
What changes from the first detected Detection Time of a detected event cause the Last modified value to be displayed?
Can someone explain what each field means?