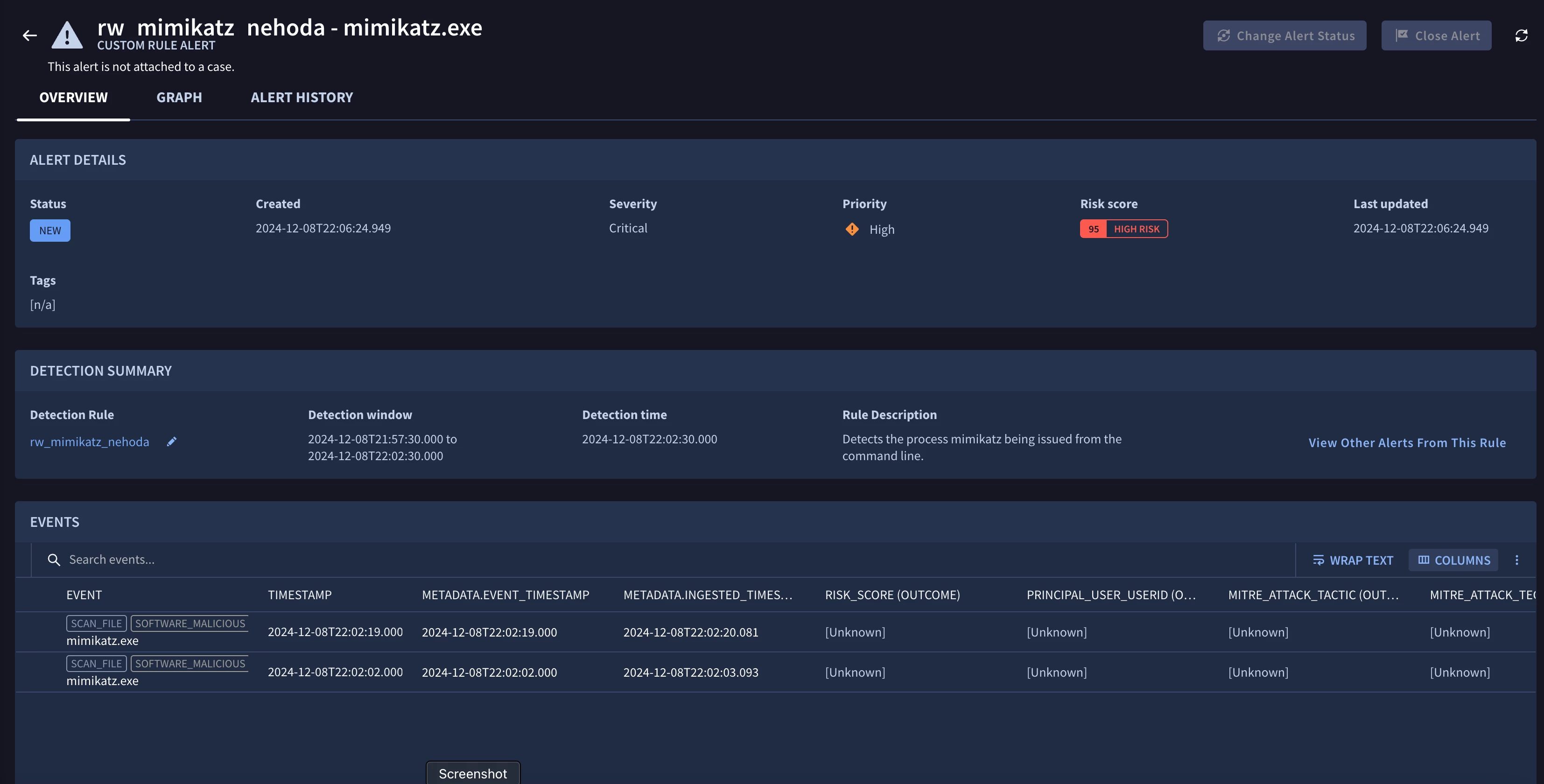
When looking at SIEM > Rules & Detections > Rules Editor, I can see when I created a rule or updated it.
When looking to see when it last ran or when it will run next all I can find is this somewhat disappointing chart (image) which purports to show "Matches," "Rule Runs" and "Run Errors."
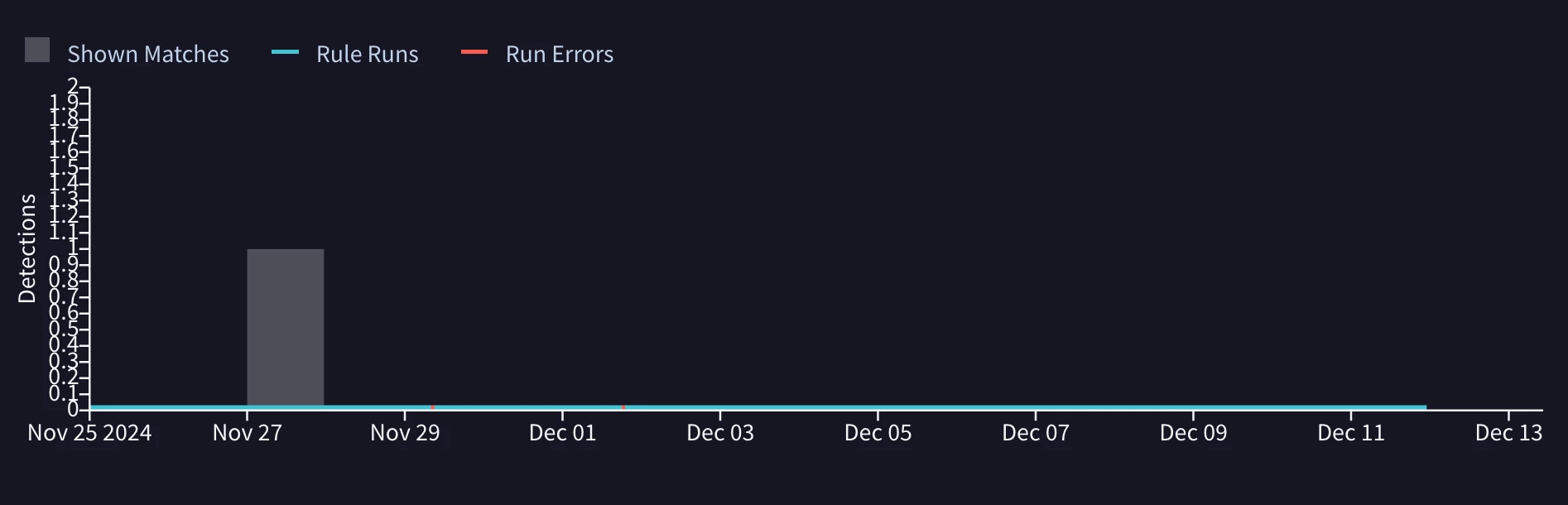
In the image above there's no hover - tool-tip or other info I can see to show me a timestamp of the rule run.
What is a definitive way to find the history of my runs per rule and when the rule is next scheduled to run?
thanks





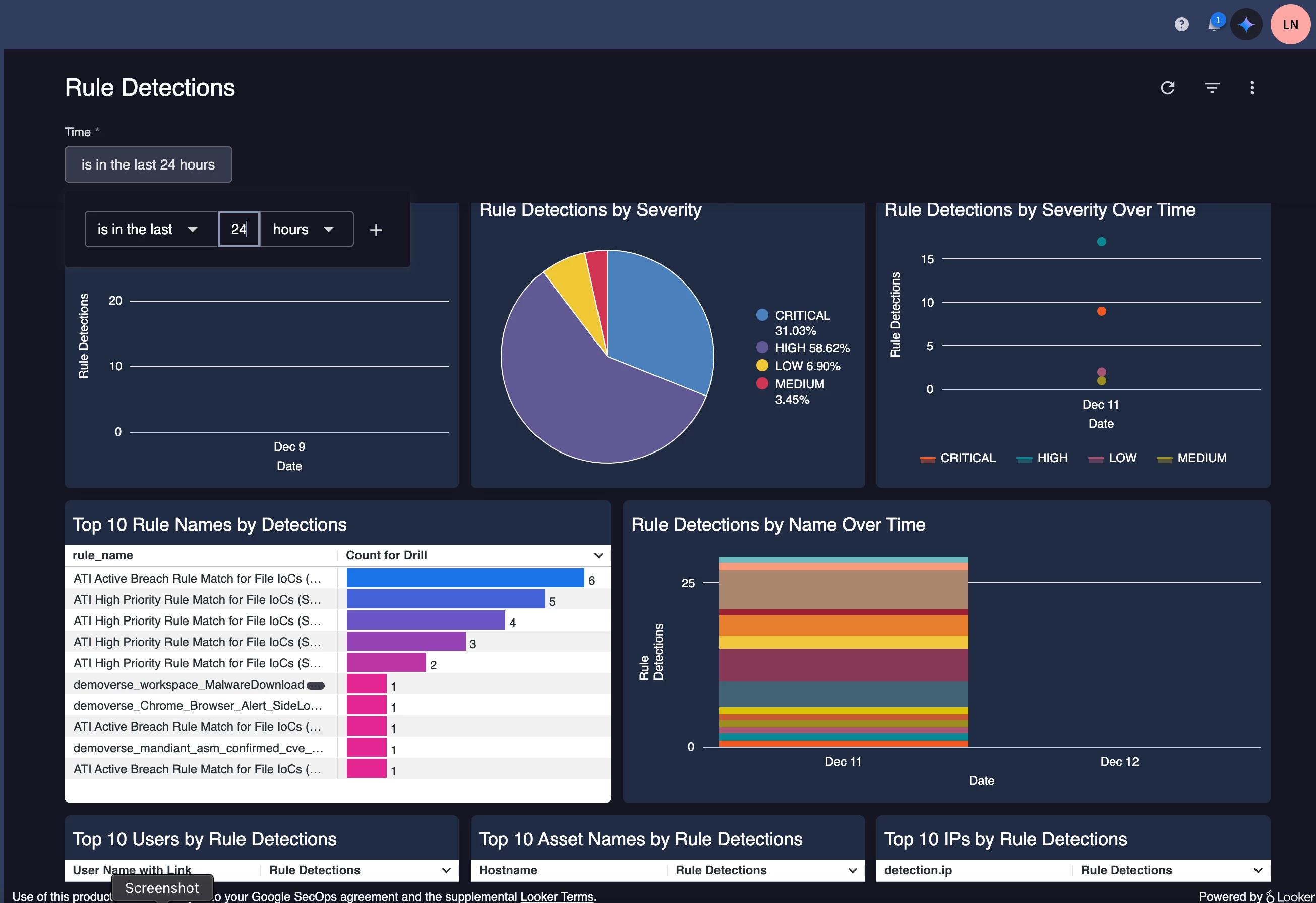
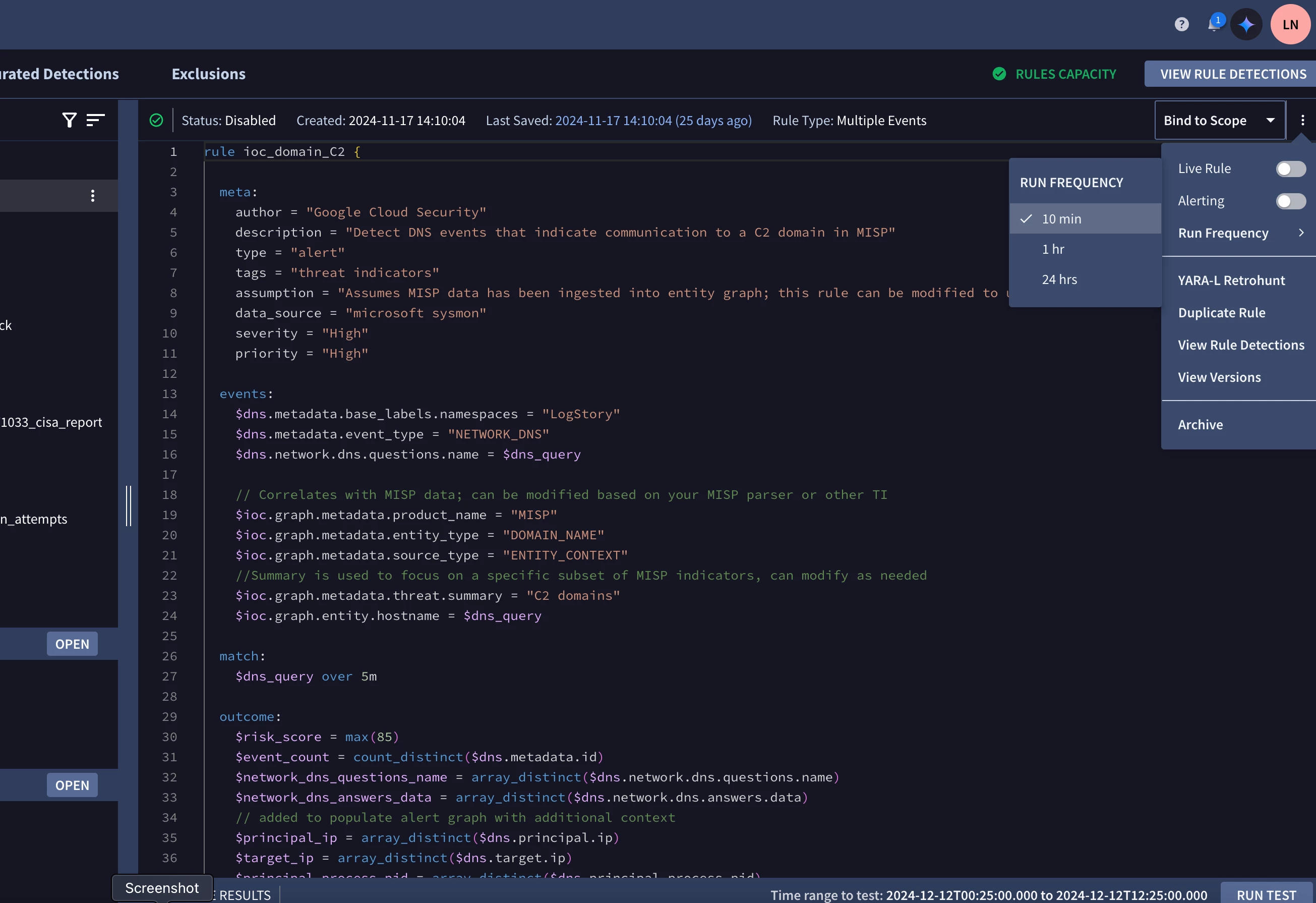
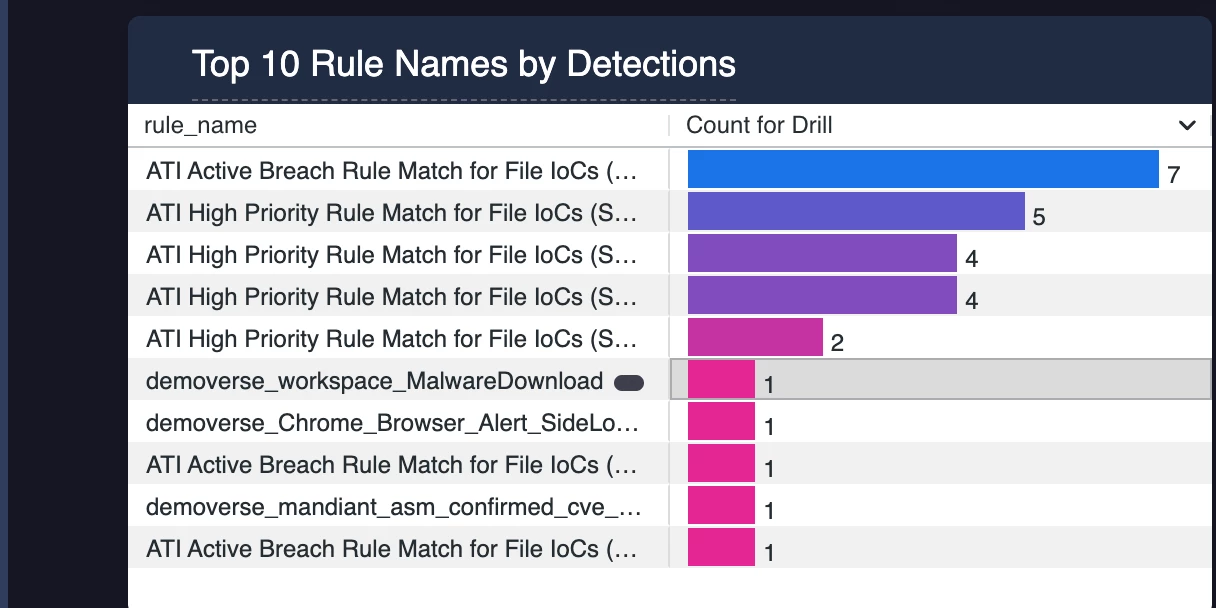 This is for the last 48hrs - so the top rule ran 7 times in 48 hours.
This is for the last 48hrs - so the top rule ran 7 times in 48 hours. 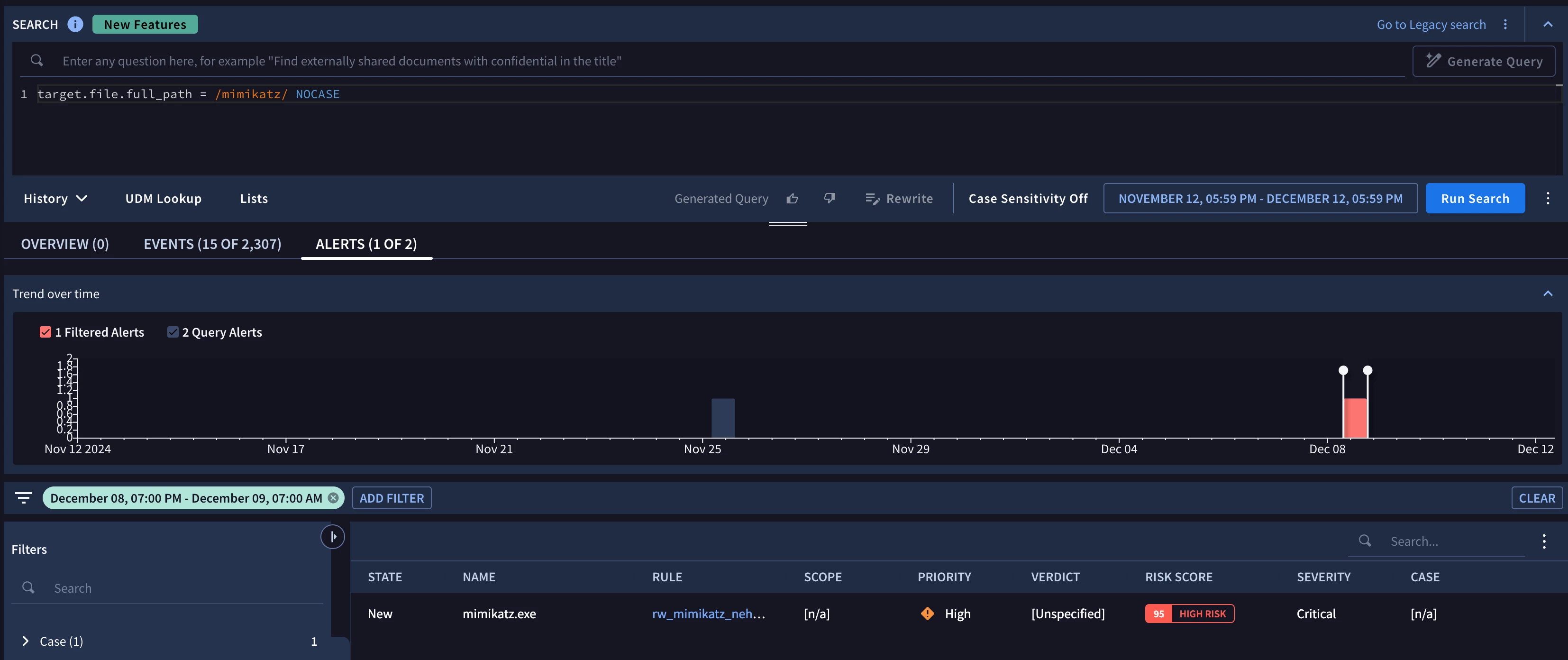 If you drill further into this you will see more information by doing a search for something specific in your rule in question ( whatever triggers your rule)
If you drill further into this you will see more information by doing a search for something specific in your rule in question ( whatever triggers your rule) 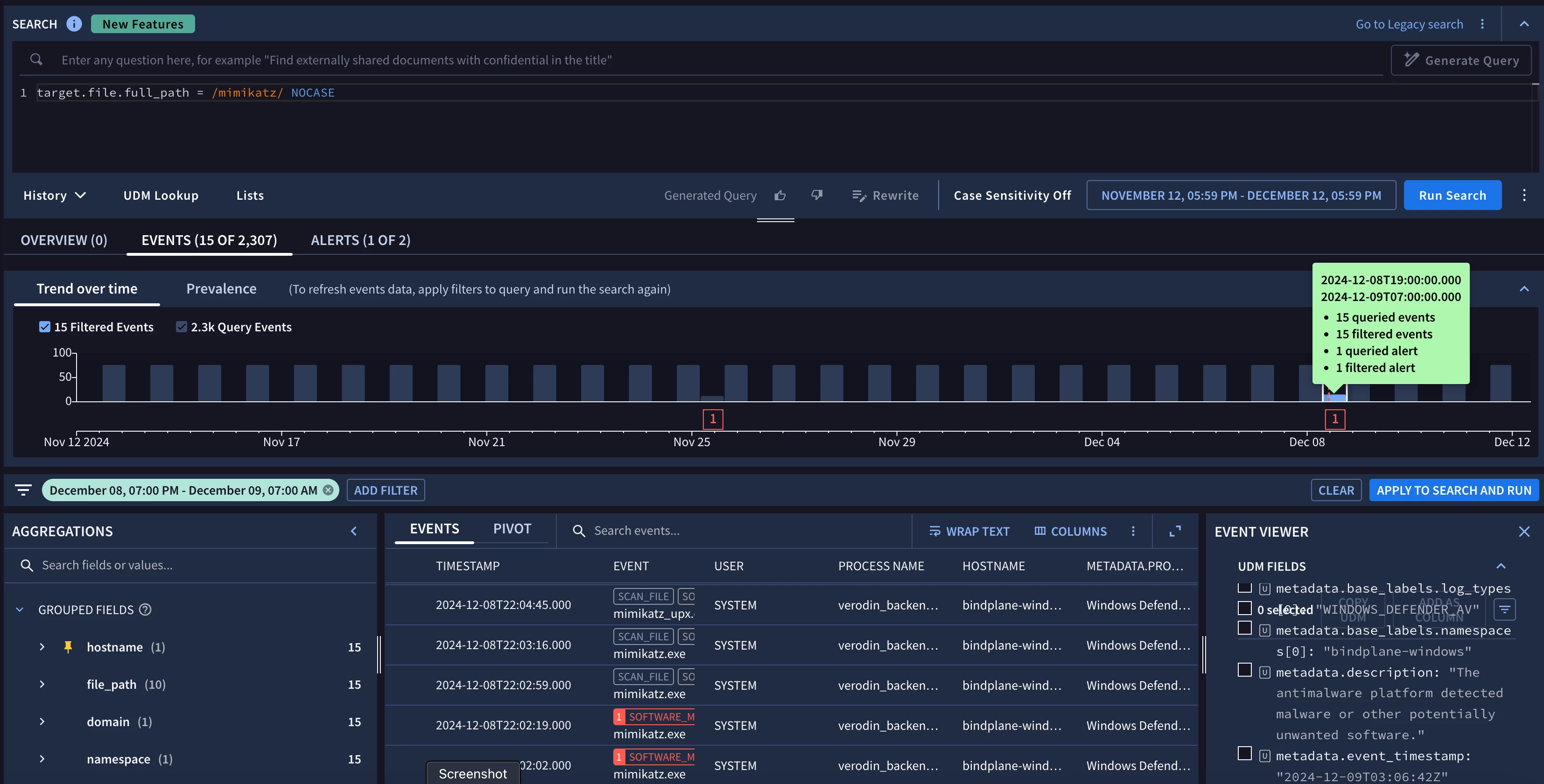 You see the timestamp of your event.
You see the timestamp of your event.