Helo folks,
I’m observing behavior in Google SecOps that seems to deviate from what I expected based on the documentation. I want to see if others have seen it or have insight into what’s happening internally. Below is the scenario, observations, and things I’ve already verified. I’d appreciate thoughts, explanations, or pointers to relevant internal logic.
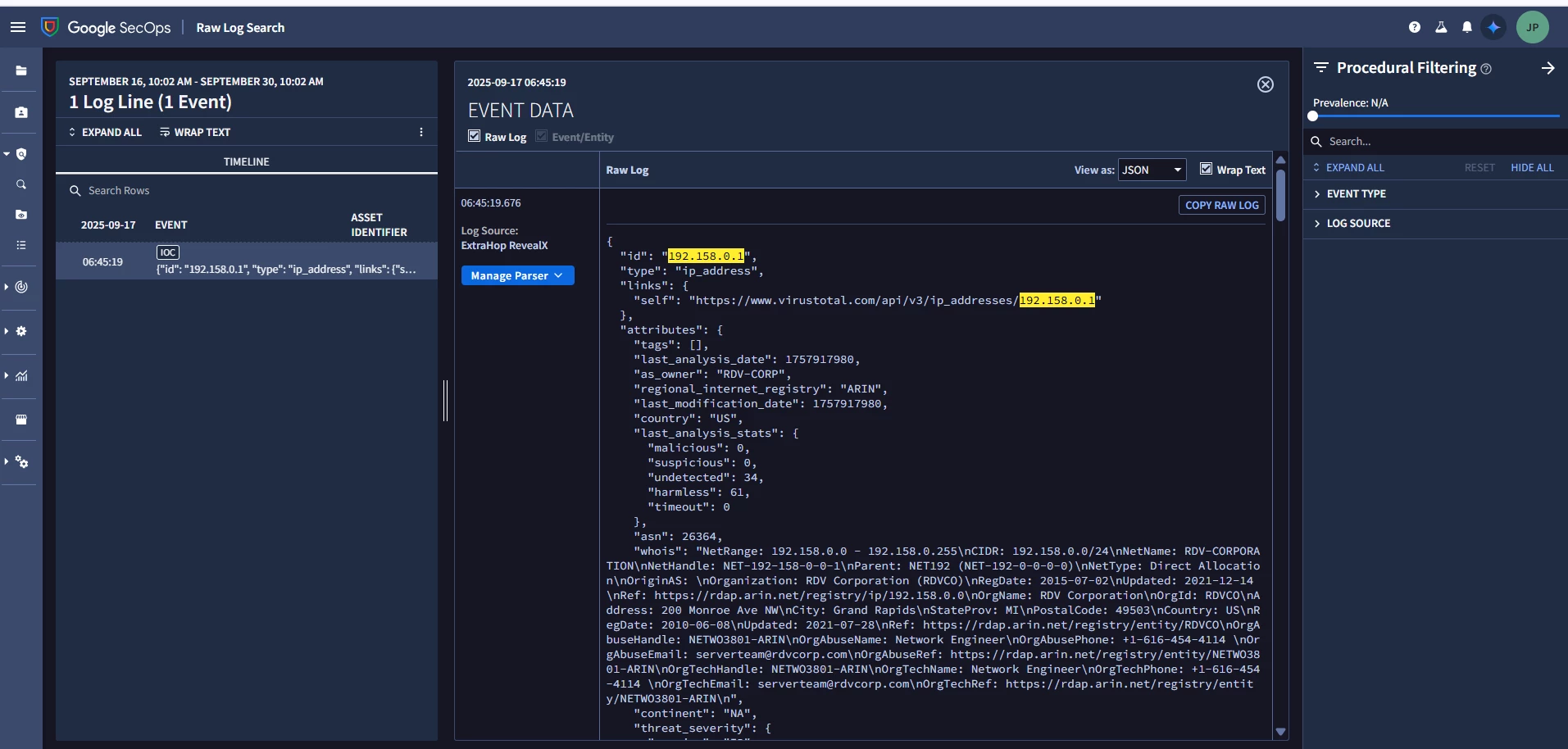
I ingest a single IOC Entity (e.g. an IP or hash) via a parser, with its metadata and interval.start_time (and without interval.end_time).
Right after ingestion, in Raw Log Search, I see exactly one entity record corresponding to that IOC, as expected.
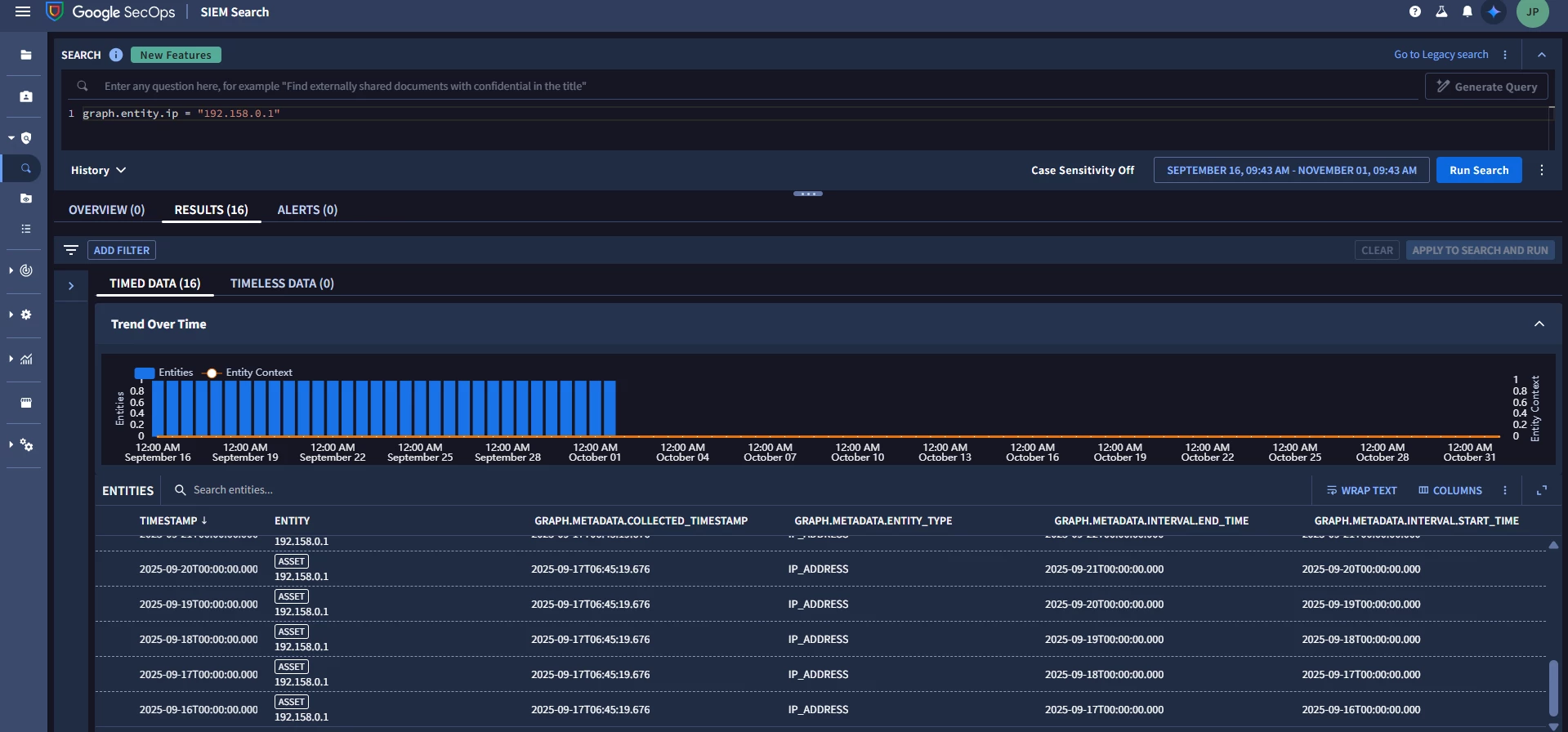
However, when I search using UDM Search over a larger time window (e.g. 1-2 Month), I see many entries (15+), each with different interval.start_time / interval.end_time, as if one entry per day.
You could see on the below attached image, when i clicked on the any entry all of them are getting highlighted which means that all of them refer to the same single entity.
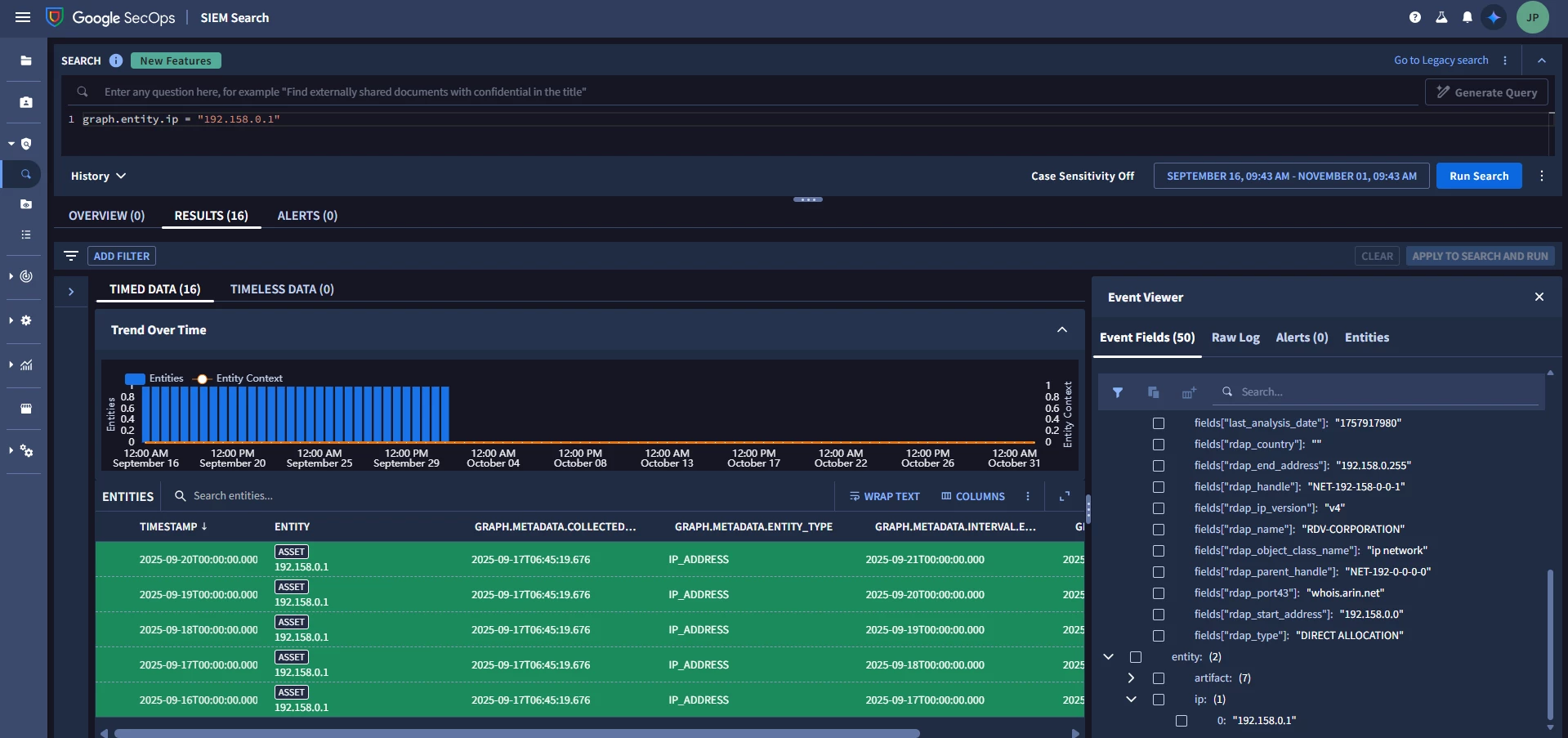
This seems inconsistent with the documented 5-day lookback / implicit TTL for entity context in Chronicle.
If anyone has deep knowledge of the entity context graph internals, or has observed similar behavior, I’d be grateful for your insight.
Major Questions :
1. Why is a new entity created each day, even though I ingested the entity only once?
2. How long does an IOC entity remain “live” in Google SecOps?
3. Why do I see inconsistencies (e.g., one entity shows 16 entries while another shows 31 entries)?
Thank you in advance!




