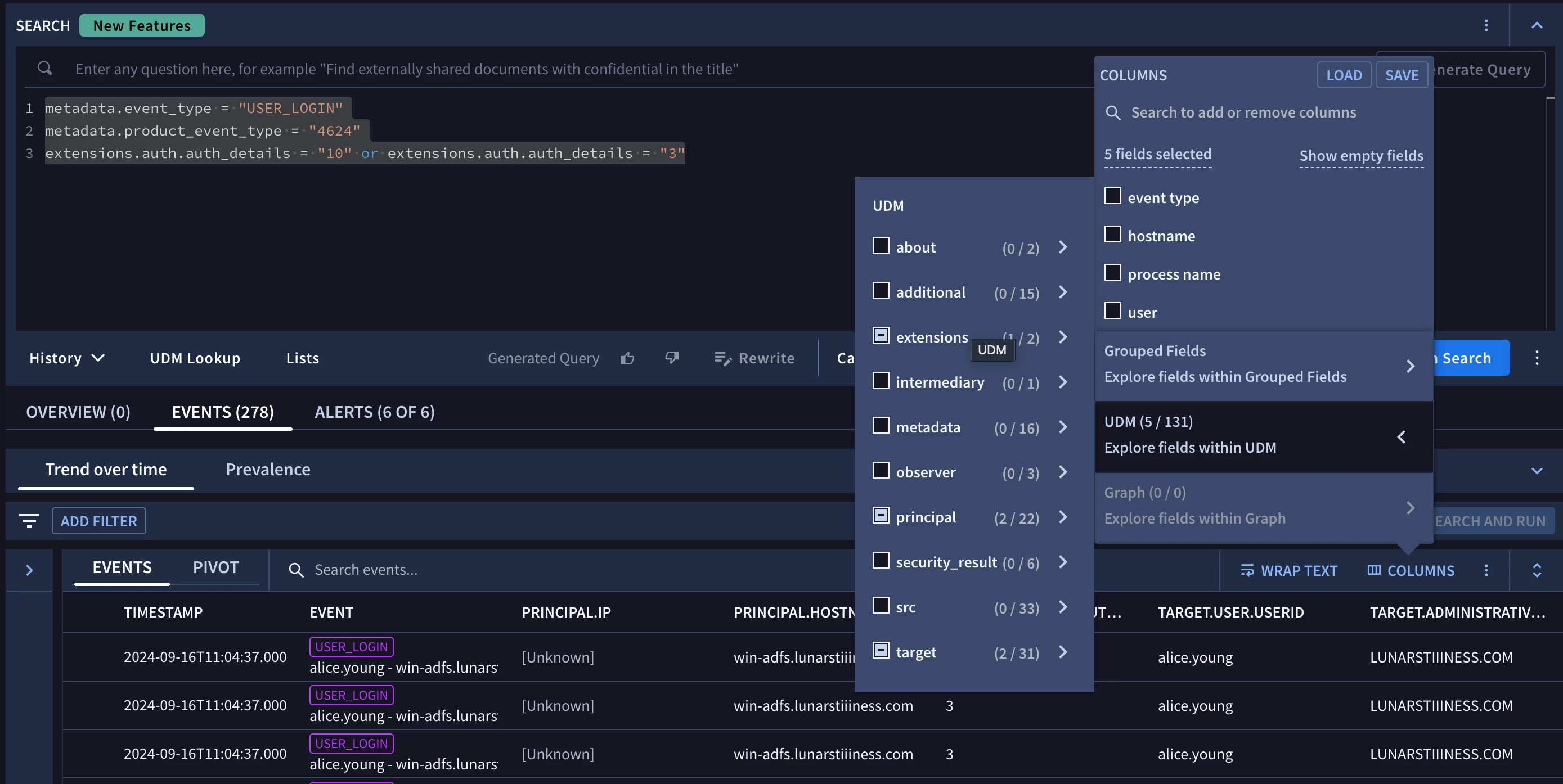
I want to be able to find successful windows logons, specifically remote logon's, and capture data from fields that are relevant to the event. I would then like to present the data from those fields to the analyst. I am able to use the
metadata.product_event_type = "4624"
to find Windows Security Events with an event ID of 4624 (successful logon event in Windows) and then I can refine and find remote logon types with
extensions.auth.auth_details = "10" or extensions.auth.auth_details = "3"
I want to match on the above events, then I want to extract the following fields from any matching event, and display the results of those fields as columns in a table with each row being an instance of the event that matches the rule.
The fields I want to capture are:
metadata.event_timestamp
extensions.auth.auth_details
principal.hostname
principal.ip
principal.process.command_line
target.administrative_domain
target.user.userid