Hi
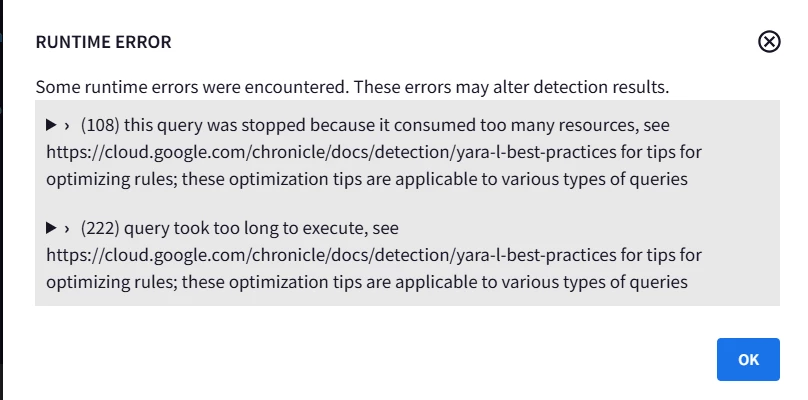
I am trying to build the below rule , where in i am trying to compare the different target SHA 256hash value appearing in any product (Crowdstrike, windows,meraki ,defender etc) with Google Safe browsing .
If i have to do this individually for each product then i would need to build multiple alerts as the event type is different for different products
Crowdstrike - metadata.event_type = "PROCESS_UNCATEGORIZED"
Meraki - metadata.event_type = "SCAN_FILE"
Defender - "USER_UNCATEGORIZED"
rule_google_safebrowsing_file_process_creation {
meta:
description = "Detection of process/file events that match Safe Browsing hashes , which are files deemed to be malicious"
severity = "Critical"
priority = "High"
events:
($execution.target.process.parent_process.file.sha256 = $sha256 or
$execution.target.process.file.sha256 = $sha256 or
$execution.target.file.sha256 = $sha256 ) and
// join execution event with Safe Browsing graph
$safebrowse.graph.entity.file.sha256 = $sha256
// Safe Browsing file hashes provided by GCTI Feed
$safebrowse.graph.metadata.product_name = "Google Safe Browsing"
$safebrowse.graph.metadata.entity_type = "FILE"
$safebrowse.graph.metadata.source_type = "GLOBAL_CONTEXT"
match:
$sha256 over 1h
condition:
$execution and $safebrowse
}
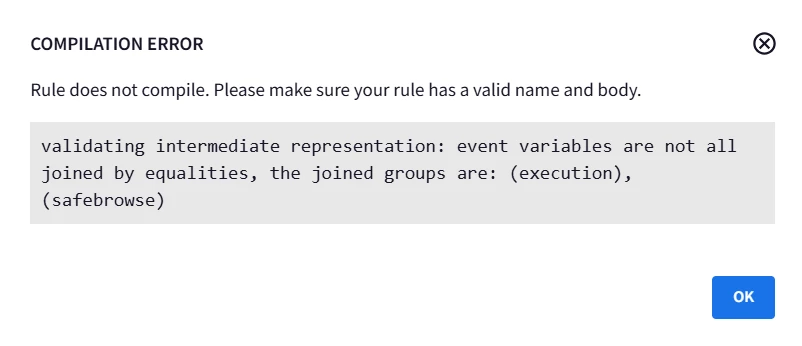
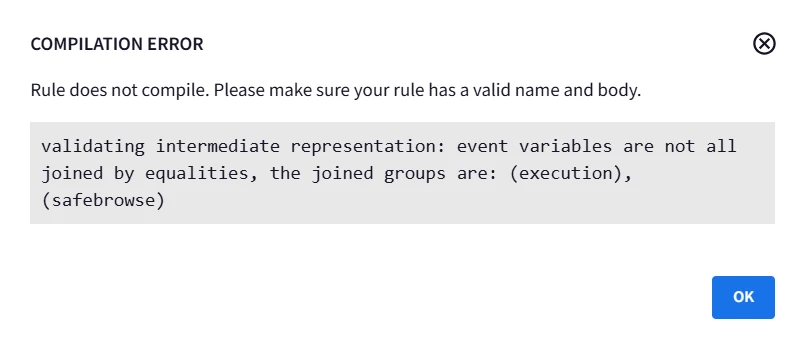
However on doing so it gives this error message