
Day 1: Google Threat Intelligence search a day keeps the phishing away…
This Google Threat Intelligence search query is designed to find potentially malicious or misleading domains that are similar to netflix.com but are not the official domain itself.
entity:domain fuzzy_domain:netflix.com and not domain:netflix.com creation_date:90d+
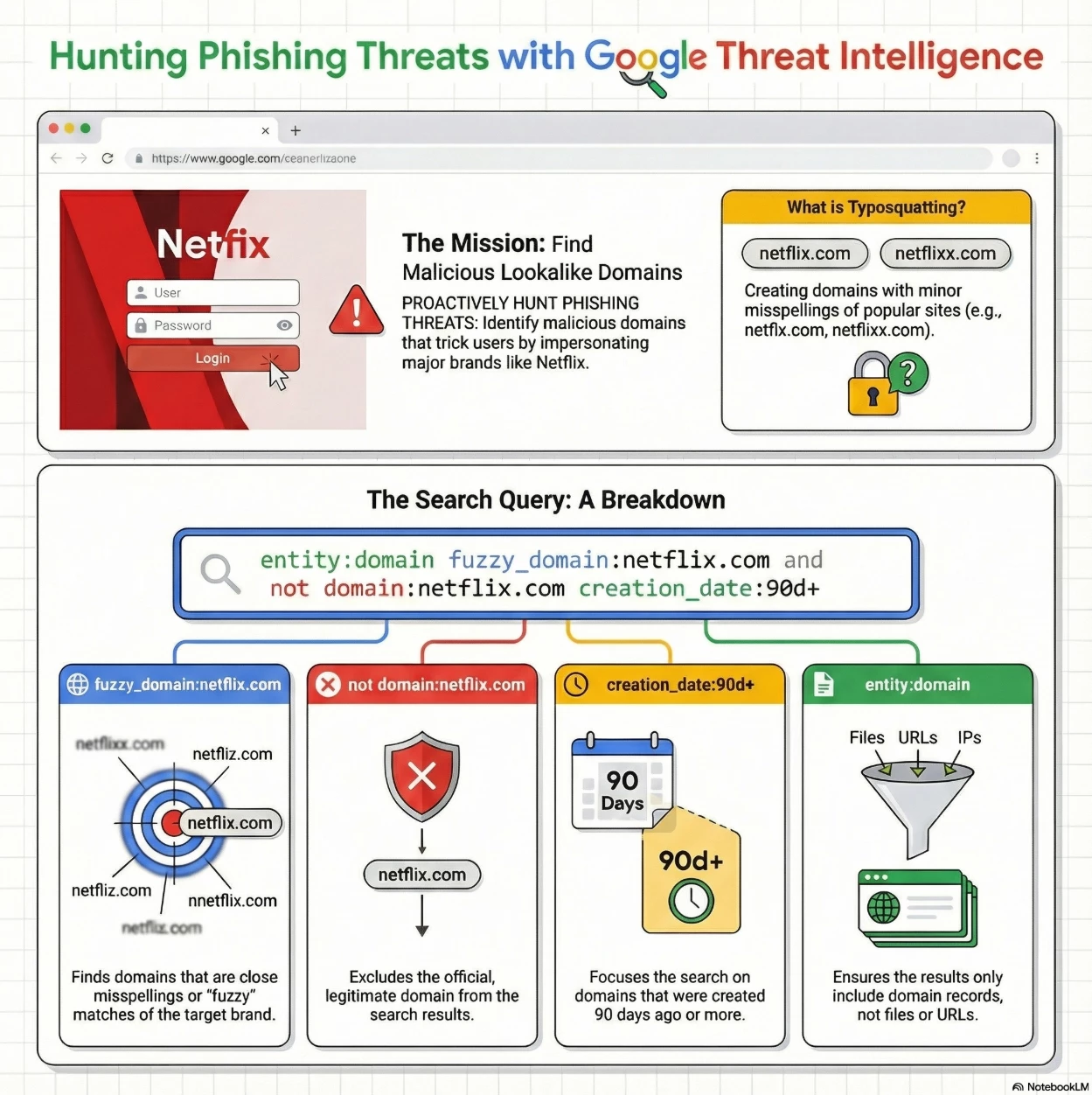
Query Breakdown: The query uses specific search modifiers (fields) and the Boolean operator (and) to precisely define the target domains.
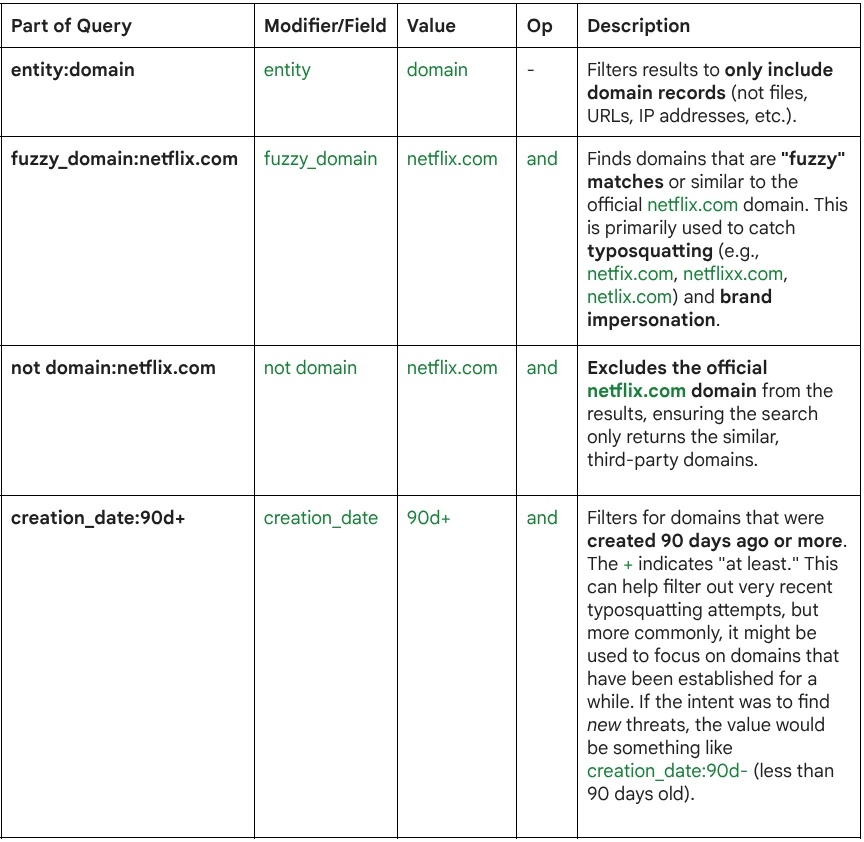
Summary of Intent: The overall goal of this search is to identify cybersquatting or typosquatting threats targeting the Netflix brand. The search looks for:
- Entity Type: Records must be domains (entity:domain).
- Similarity: The domains must be similar in spelling to netflix.com (fuzzy_domain:netflix.com).
- Exclusion: The official domain itself must be excluded (not domain:netflix.com).
- Age: The domain must have an established creation date of 90 days or more (creation_date:90d+).
Day 2: Hunt Cobalt Strike callback URLs
This VirusTotal Intelligence search query is designed to identify URLs acting as Command and Control (C2) servers by spotting a widely known default URI path associated with Cobalt Strike.
entity:url path:"/N4215/adj/amzn.us.sr.aps"

Query Breakdown: The query combines an entity filter with a specific path modifier to pinpoint potentially malicious infrastructure.
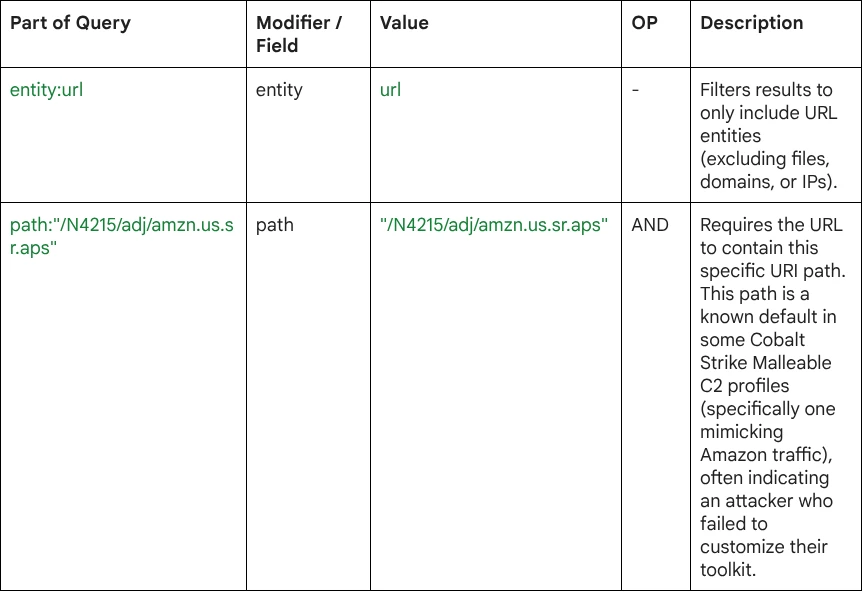
Summary of Intent: The overall goal of this search is to hunt for Cobalt Strike C2 infrastructure relying on default configurations.
The search looks for:
- Entity Type: The indicators must be URLs (entity:url).
- Known Indicator: The presence of the /N4215/adj/amzn.us.sr.aps path, which is a high-confidence indicator of a default or poorly configured Cobalt Strike beacon attempting to blend in with legitimate traffic.
Tip: You can narrow these results further by adding fs:30d+ for recent submissions or p:5+ to focus on URLs already flagged by multiple detection engines.
Day 3: Hunting Anonymous Email Vectors
This Google Threat Intelligence search query is designed to identify potentially malicious emails that leverage anonymity services, specifically targeting those from 'Onionmail.org' that contain attachments—a high-risk indicator for malware delivery.
type:email embedded_domain:onionmail.org have:email_attachment

Query Breakdown: The query combines file type, embedded domain, and metadata modifiers to pinpoint high-risk communication.
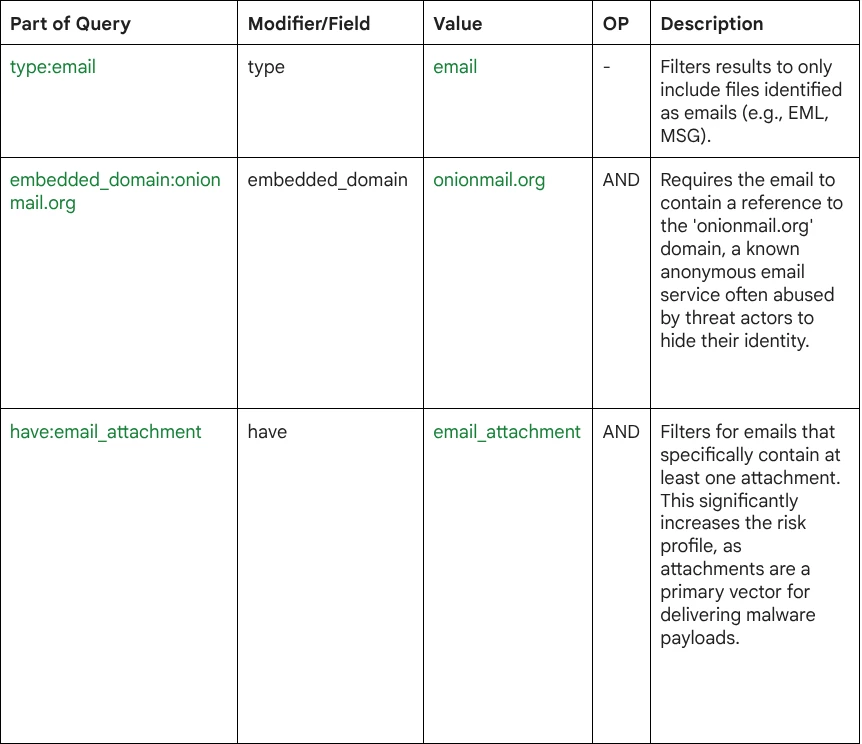
Summary of Intent: The overall goal of this search is to detect potentially malicious emails hiding behind privacy services.
The search looks for:
- File Type: The target must be an email file (type:email).
- Anonymity Service: It must utilize Onionmail.org (embedded_domain:onionmail.org), a service that can be abused for its anonymity.
- High-Risk Indicator: It must contain an attachment (have:email_attachment), distinguishing it from simple text-based spam and focusing on potential malware delivery attempts.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphics. Additional analysis and details of this search query written by the amazing


