
This search query is designed to hunt for newly created or emerging malware that specifically targets information (stealers) by leveraging Program Database (PDB) file metadata which is often overlooked but can contain revealing developer-left strings.
entity:file metadata:".pdb" metadata:"stealer" p:5+ fs:30d+
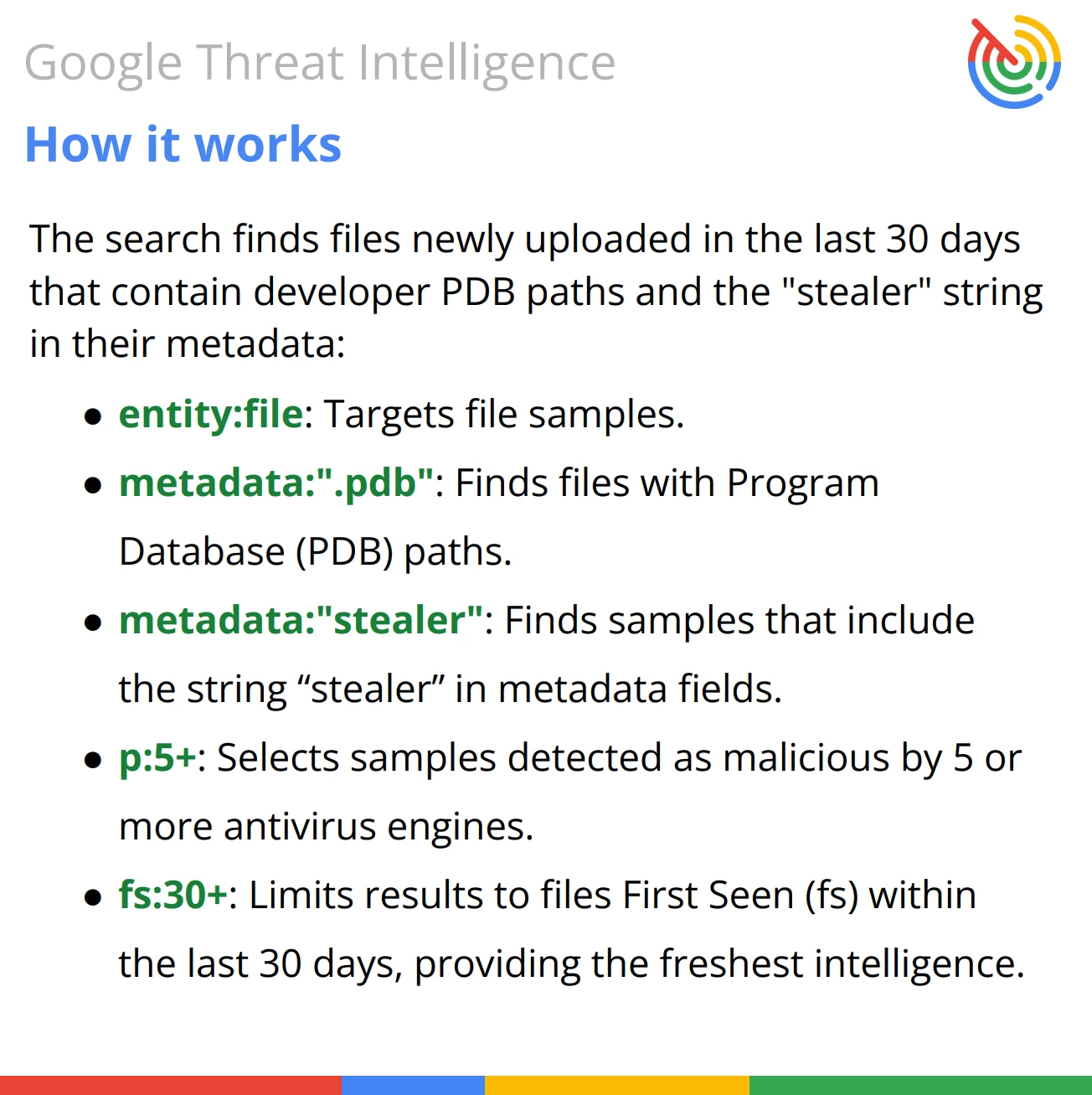
Query Breakdown: The query proactively identifies new or emerging information-stealer malware families by analyzing non-traditional metadata that threat actors often forget to scrub.
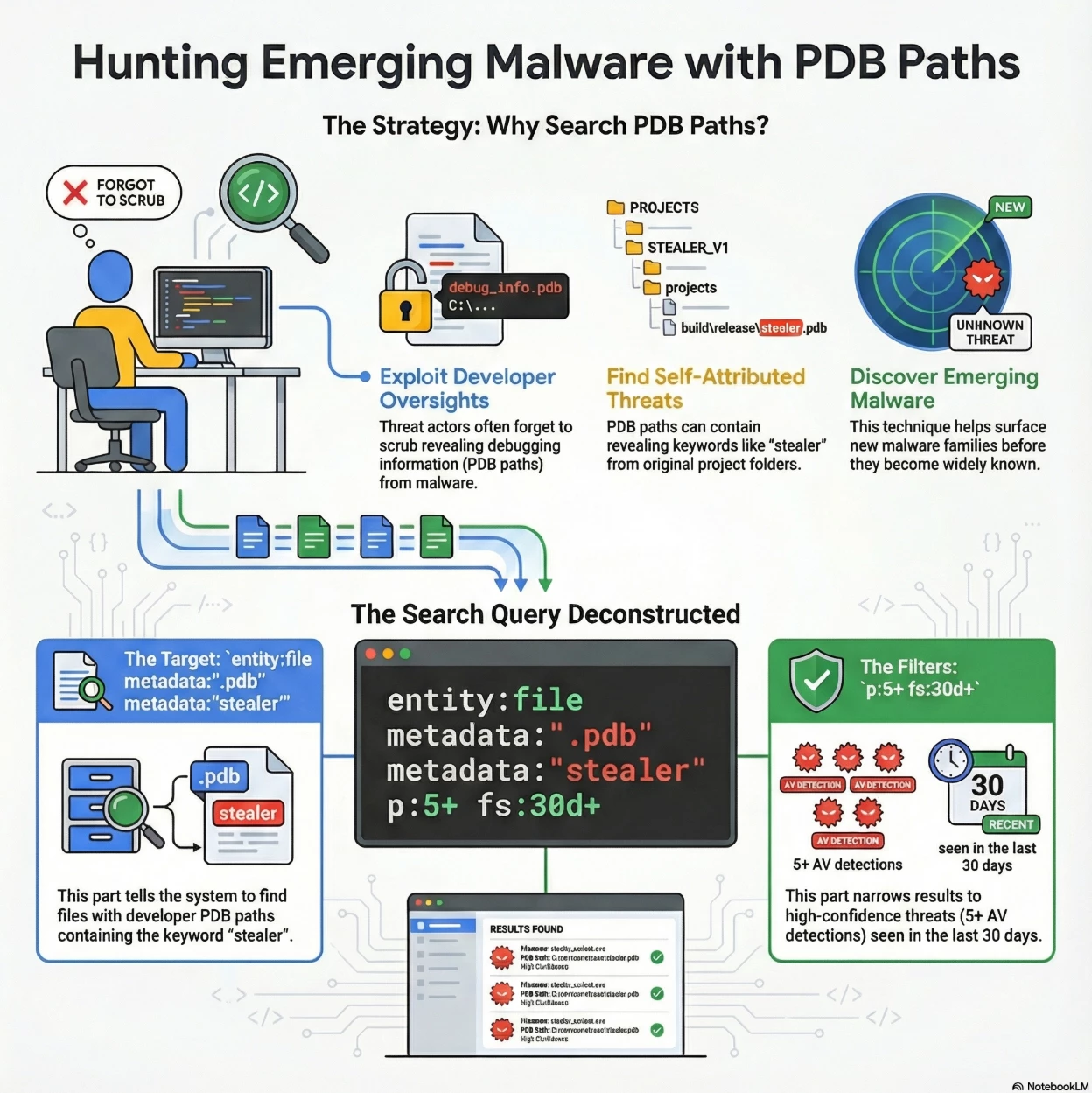
Summary of Intent: The overall goal of this search is to proactively identify new or emerging information-stealer malware families by analyzing non-traditional metadata that threat actors often forget to scrub.
The search looks for:
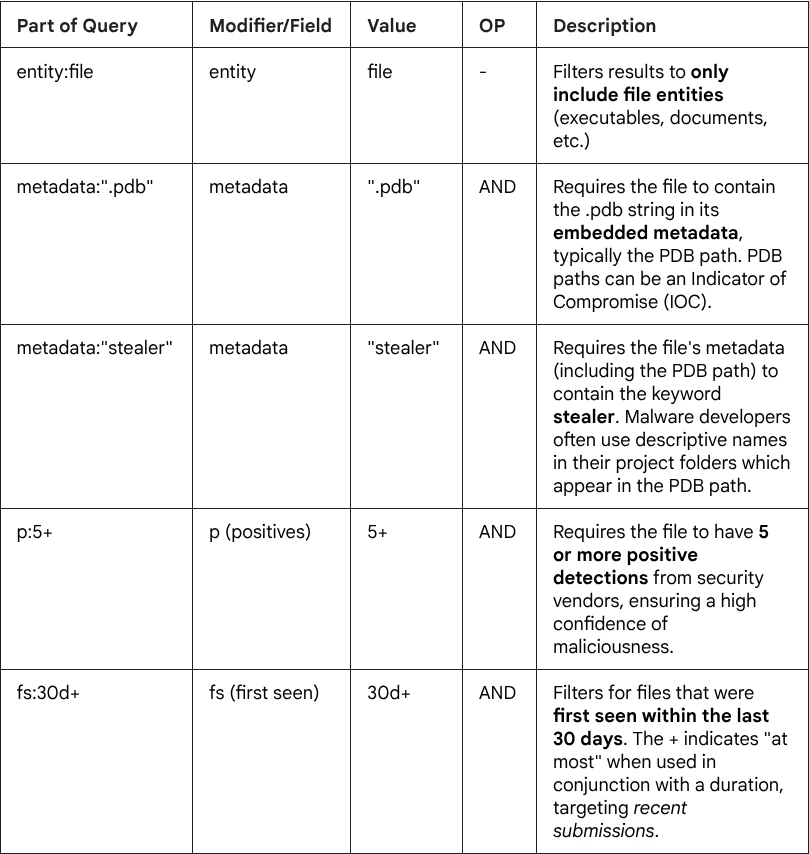
- Artifact Type: The search focuses on files (entity:file).
- Developer Clues (PDB): It leverages Program Database (PDB) paths (embedded in executables). PDB files contain debugging information linking the compiled binary back to the source code files and directory structure. Threat actors sometimes forget to remove this path or use descriptive project/folder names (like "stealer") which, when compiled, get embedded in the final executable.
- Malware Type: The presence of the string stealer in the PDB path is a very strong, self-attributed indicator of the file's primary malicious capability (information stealing).
High Confidence & Recency: By requiring 5 or more detections (p:5+), the query filters for files that are definitively malicious, and by restricting the first seen date to the last 30 days (fs:30d+), it focuses the results on new or recently used malware.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


