
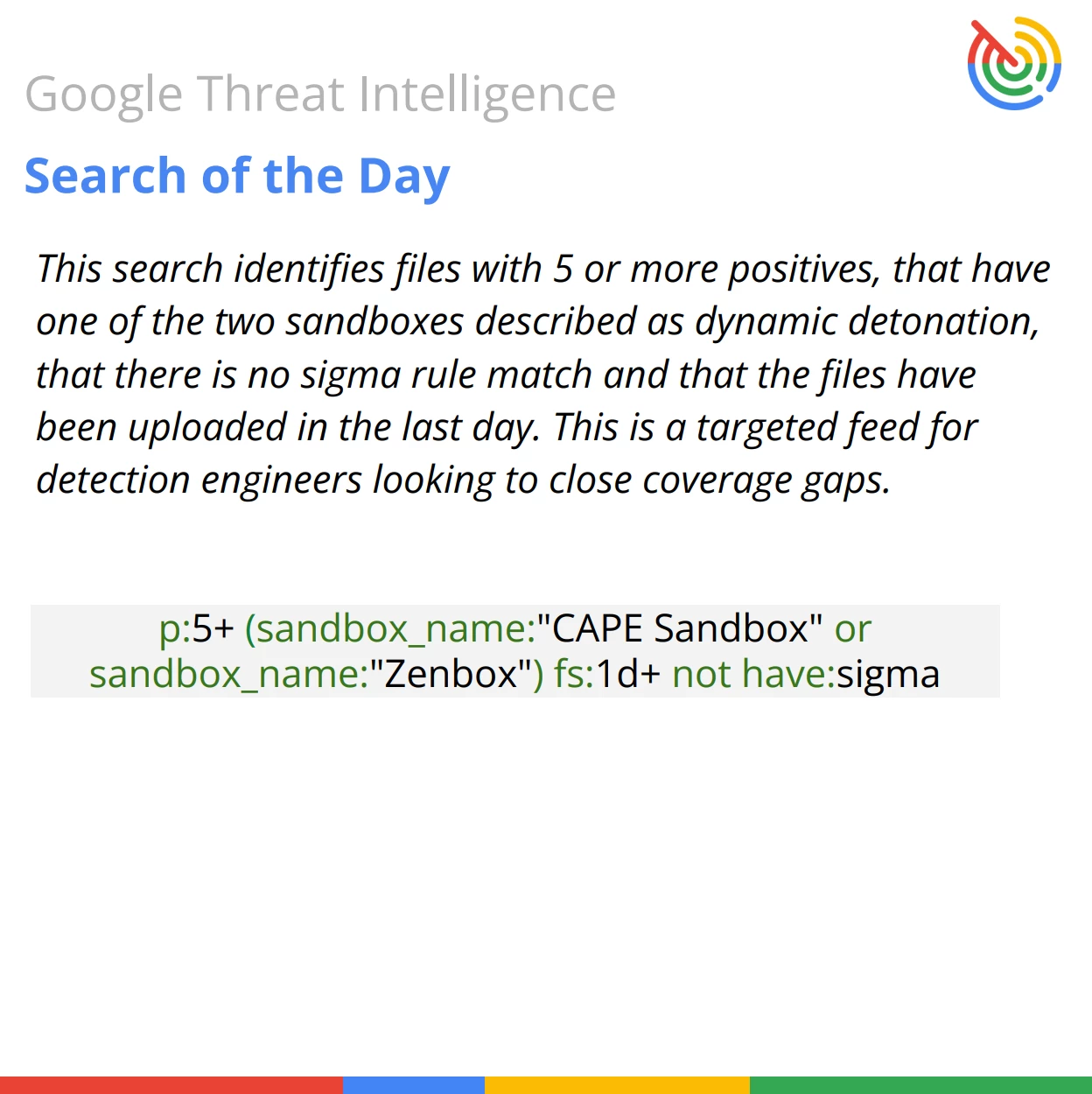


This targeted search is designed to provide an efficient, daily list of files that are newly uploaded, validated with multiple antivirus detections and high-quality sandbox reports, yet currently lack Sigma rule matches. This allows detection engineers to prioritize coverage gaps in their security monitoring infrastructure.
p:5+ (sandbox_name:"CAPE Sandbox" or sandbox_name:"Zenbox") fs:1d+ not have:sigma
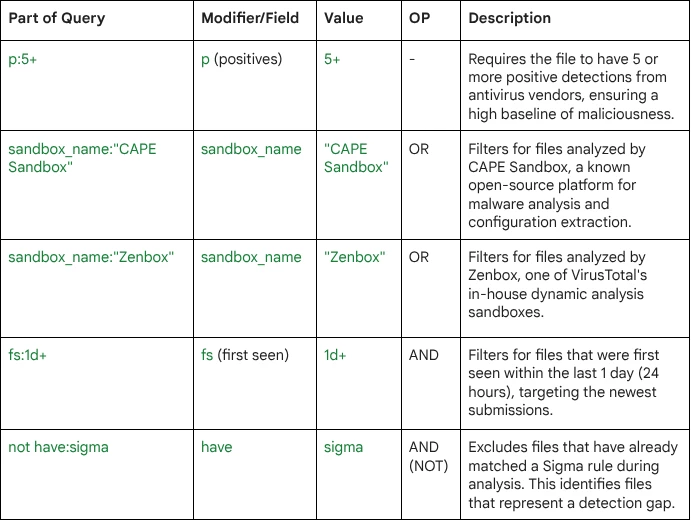
Query Breakdown: The query combines reputation, behavioral analysis, recency, and detection coverage filters to isolate high-priority files for detection engineering.
Summary of Intent: The overall goal of this search is to identify and prioritize coverage gaps in detection engineering by focusing on confirmed malicious files with high-quality, recent behavioral data that have not yet triggered a standardized detection rule.
The search looks for:
- High Confidence: Files must be confirmed malicious with at least 5 AV detections (p:5+).
- High-Quality Behavior: It specifically requires analysis from CAPE or Zenbox sandboxes, which provide detailed, reliable dynamic analysis reports.
- Recency: Files must be newly submitted (fs:1d+), ensuring the threat is a current priority and not an old, well-known sample.
- Detection Gap: The not have:sigma modifier is the key, filtering out files that are already covered by Sigma rules. Sigma rules are YAML-based, platform-independent detection definitions used to standardize how suspicious activity is described across different SIEM platforms. By excluding files that have Sigma matches, the query pinpoints new, active threats that need immediate attention from detection engineers to create new rules.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


