

This search identifies files whose malware configuration contains SMTP or IMAP fields, which typically indicates the malware uses an email-based mechanism for communication or data exfiltration.
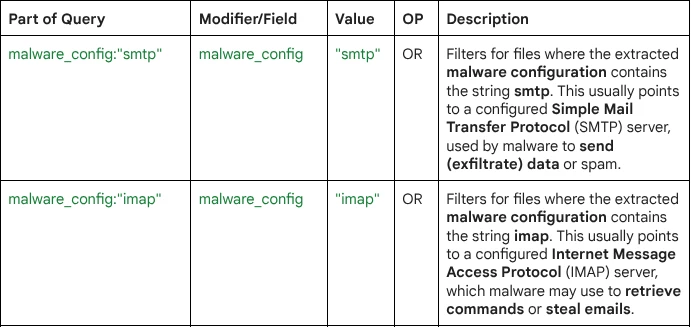
malware_config:"smtp" or malware_config:"imap"
Query Breakdown: The query uses the malware_config modifier, which is a premium VirusTotal Intelligence feature that contains configuration details extracted for specific malware families.
Summary of Intent: The overall goal of this search is to detect malware that leverages standard email protocols (SMTP/IMAP) for its operations, focusing on the configuration data extracted from the malicious file.
The search looks for:
- Protocol-Based Threat: It targets malware that includes hardcoded or configurable fields for SMTP (for sending) or IMAP (for receiving/reading) email credentials or server details.
- Exfiltration/C2 Indicator: The presence of SMTP configuration is a strong indicator that the malware intends to exfiltrate stolen data (like credentials or logs) by sending it as an email attachment or body to an attacker-controlled mailbox.
- Configuration Detail: By using the malware_config modifier, the query bypasses searching the file's static content and instead looks in the structured, decrypted configuration data that security tools have already extracted from the sample. This is a high-fidelity way to detect the malware's intended network communication methods.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


