

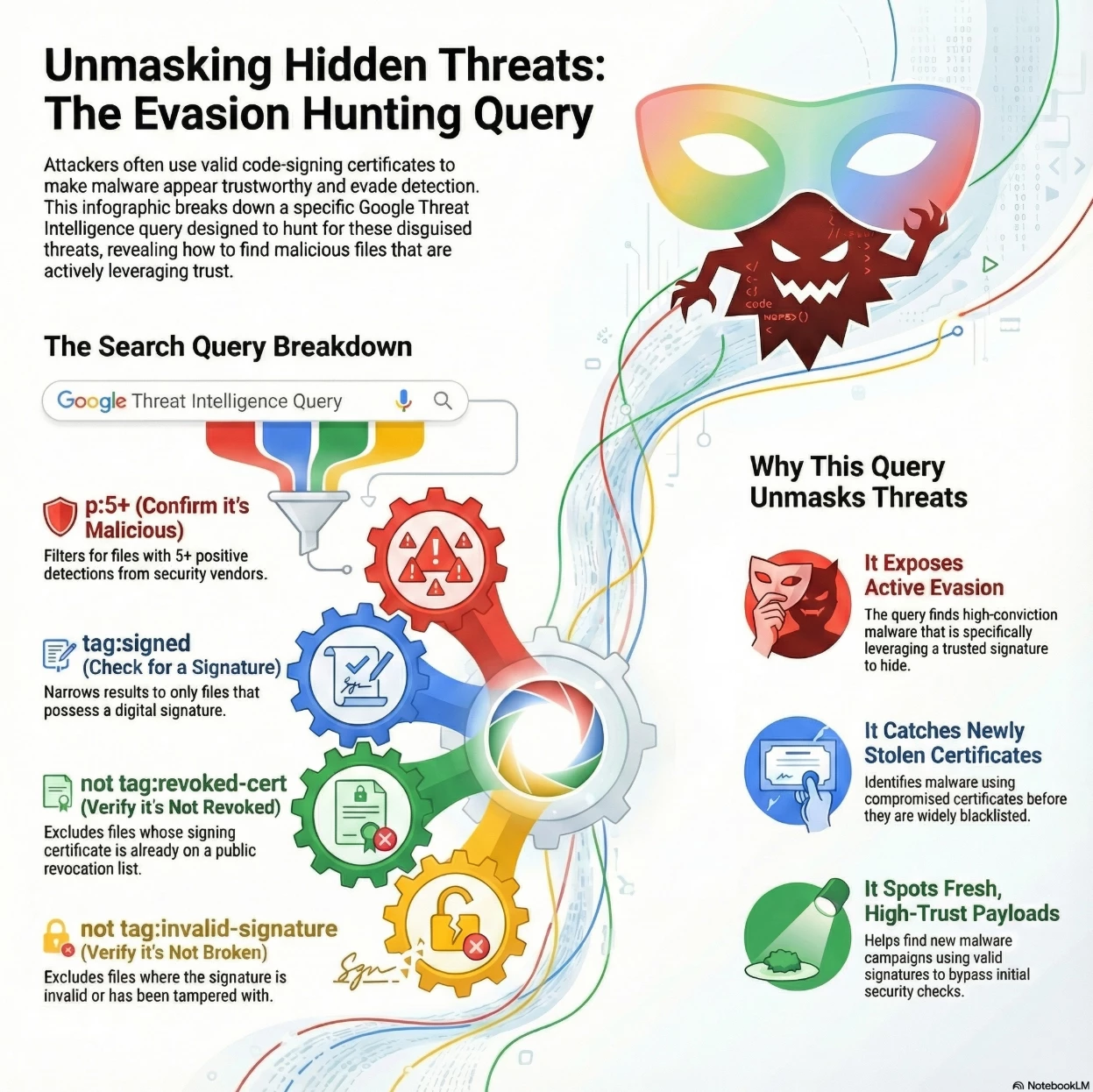
This targeted search is designed to hunt for files that are high-conviction malware but still rely on a valid, non-revoked digital signature. This often points directly to newly stolen code-signing certificates or fresh, high-trust payloads.
tag:signed not tag:revoked-cert not tag:invalid-signature p:5+
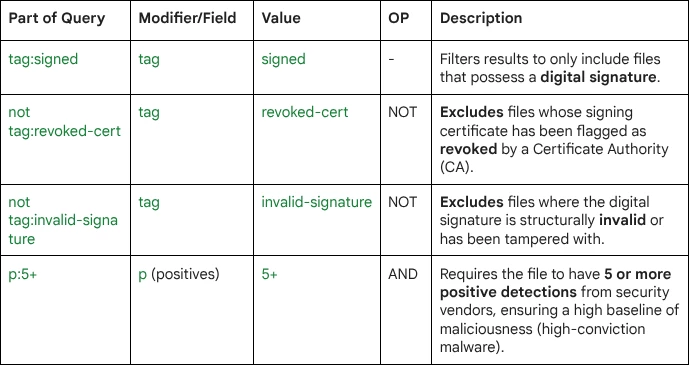
Query Breakdown: The query combines reputation filters (p:5+) with certificate validation tags to isolate threats that are actively attempting to evade detection by leveraging trust.
Summary of Intent: The overall goal of this search is to identify active threats leveraging compromised digital signatures for trust and evasion.
The search looks for:
- High-Confidence Malware: The file must be flagged by 5 or more AV engines (p:5+), confirming its malicious nature.
- Digital Trust: The file must be digitally signed (tag:signed).
- Active Evasion: The key is the combination of maliciousness (p:5+) with the absence of revocation or invalidity tags (not tag:revoked-cert not tag:invalid-signature).
This filter isolates:- Newly Stolen Certificates: Malware signed with a certificate that has been recently compromised but not yet added to Certificate Revocation Lists (CRLs).
- Fresh Payloads: New malware campaigns that are successfully using a legitimate or compromised, but still trusted, certificate to bypass security measures that rely solely on signature status.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


