
This search is designed to identify files that use a specific, hardcoded User-Agent string during their dynamic analysis, which is the tell-tale signature of a Cobalt Strike beacon attempting covert Command and Control (C2) communication.
entity:file behavior:"Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 5.2) Java/1.5.0_08"
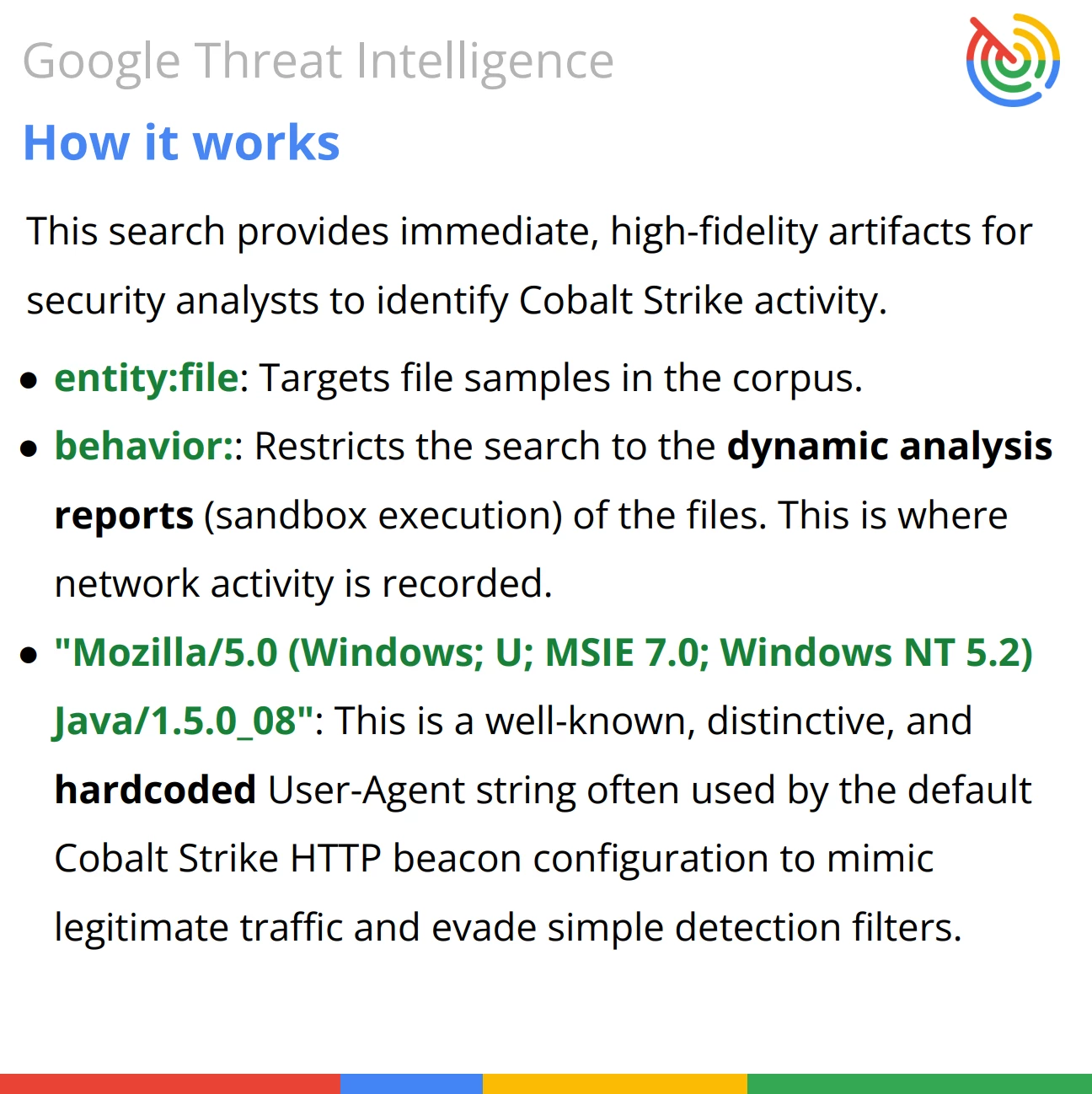
Query Breakdown: The query uses the entity filter and the behavior modifier to target files exhibiting a known, static C2 communication pattern during sandbox execution.
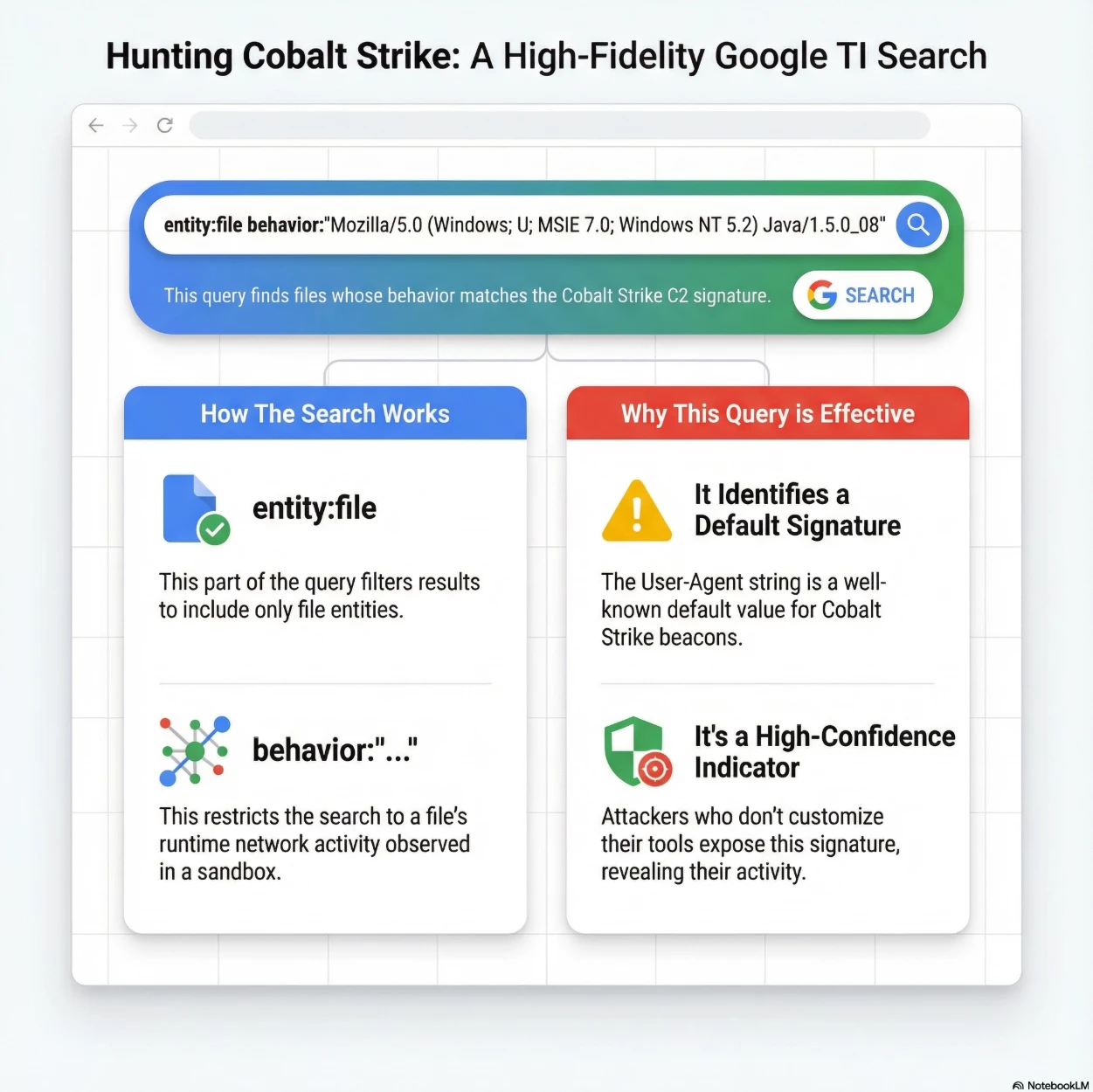
Summary of Intent: The overall goal of this search is to detect Cobalt Strike beacons that are using their default or a poorly customized configuration to establish covert C2 communication.
The search looks for:
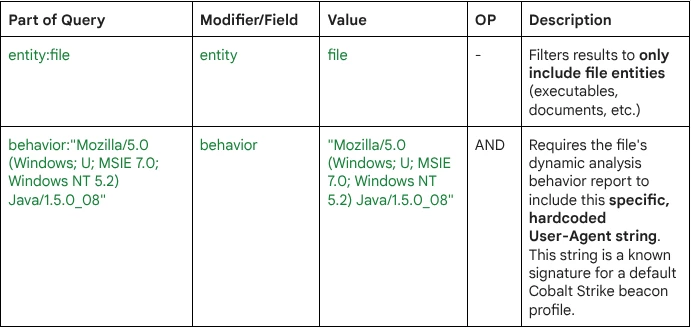
- Artifact Type: The target is a malicious file (entity:file) capable of making network connections.
- Behavioral Fingerprint: It specifically targets the file's runtime behavior (as observed in a sandbox) for the presence of the exact User-Agent string: "Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 5.2) Java/1.5.0_08".
- High-Confidence Indicator: This particular User-Agent string is a well-known default value often used by the Cobalt Strike C2 framework. Attackers who fail to customize their Malleable C2 profile will often expose this signature, making it a high-confidence indicator of compromise (IOC) for Cobalt Strike activity.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


