
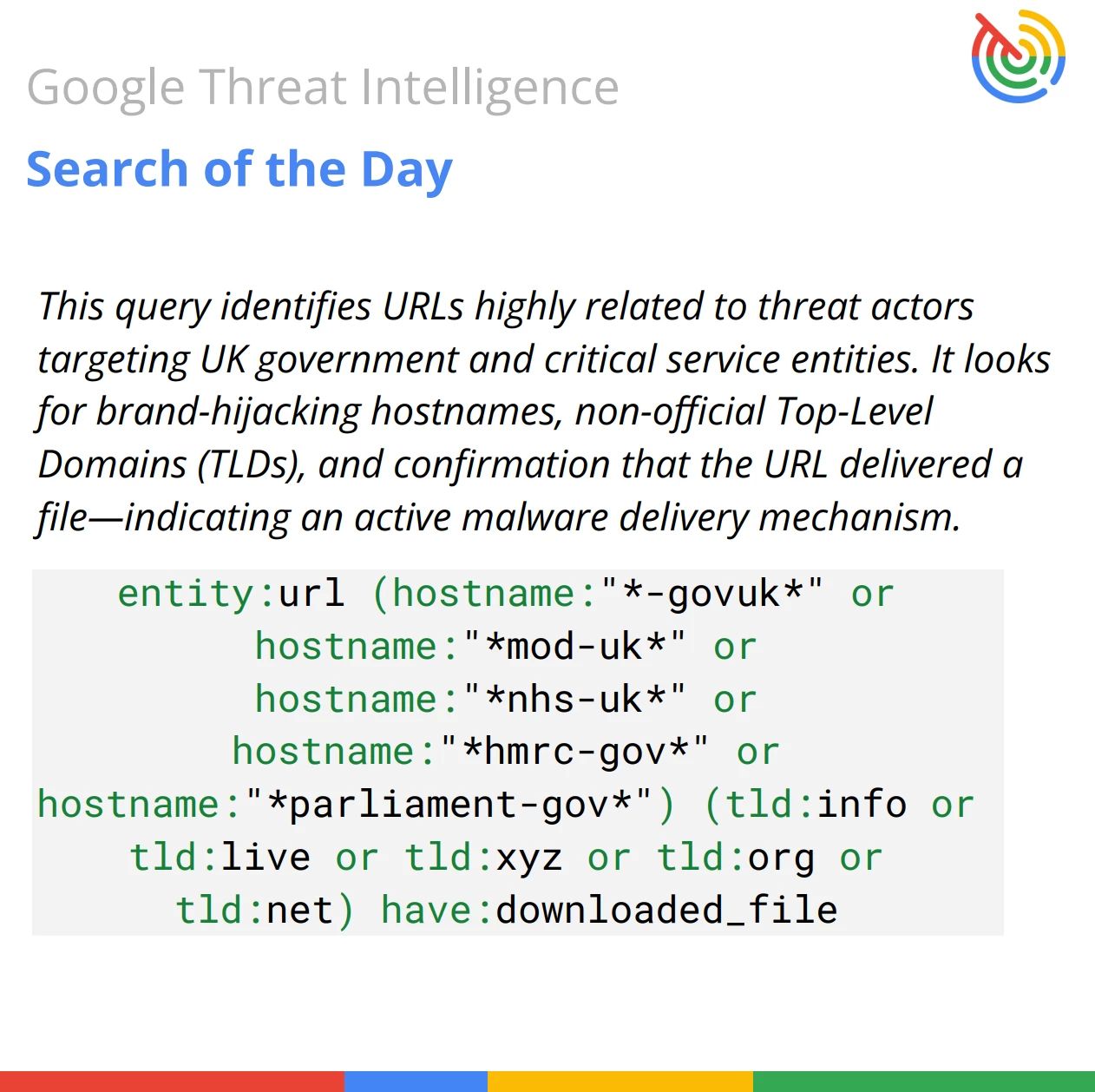
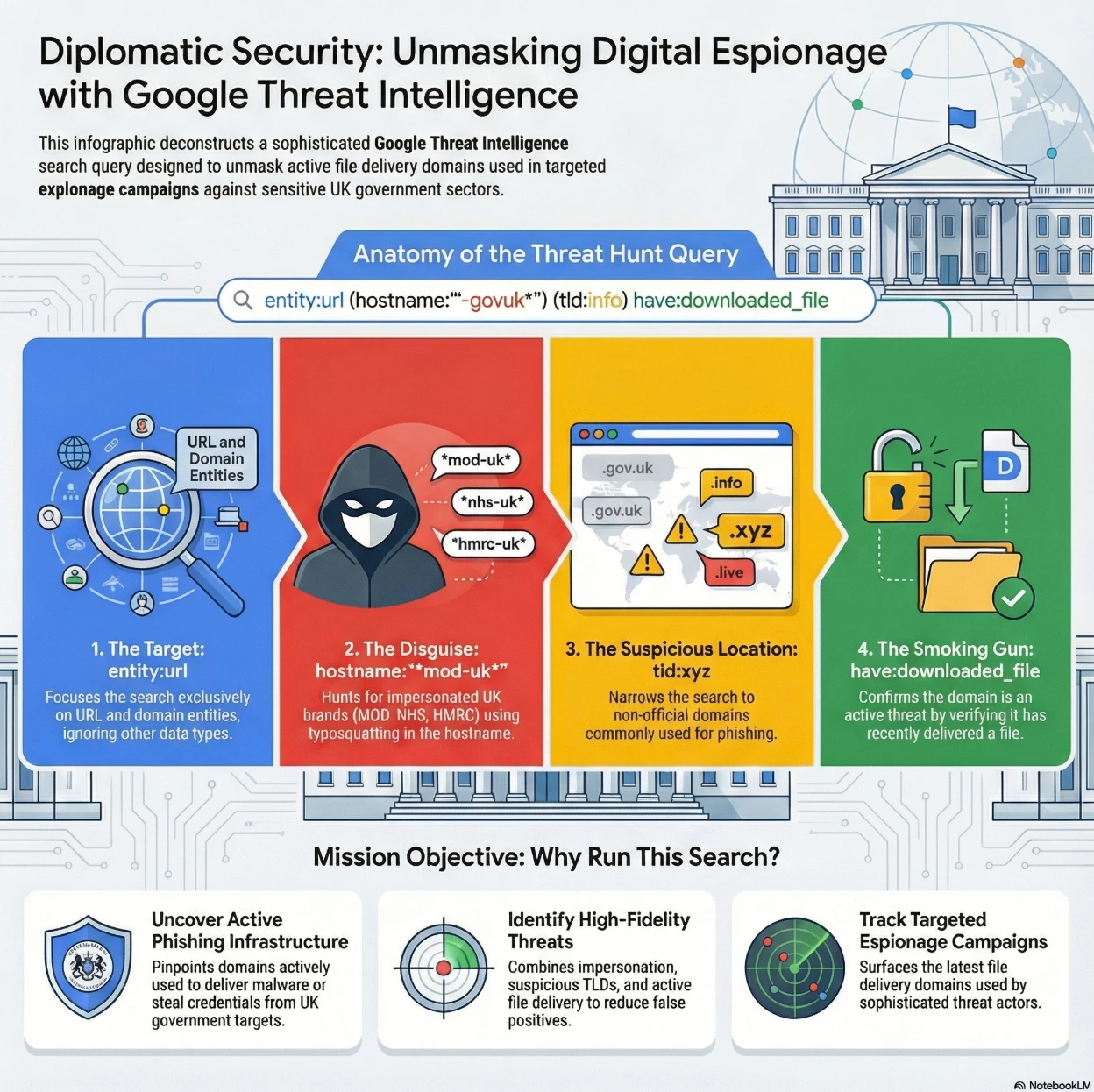
This sophisticated search is designed to unmask active file delivery domains used by threat actors in targeted espionage campaigns against sensitive UK sectors like the Ministry of Defence (MOD), National Health Service (NHS), and His Majesty's Revenue and Customs (HMRC).
entity:url (hostname:"*-govuk*" or hostname:"*mod-uk*" or hostname:"*nhs-uk*" or hostname:"*hmrc-gov*" or hostname:"*parliament-gov*") (tld:info or tld:live or tld:xyz or tld:org or tld:net) have:downloaded_file
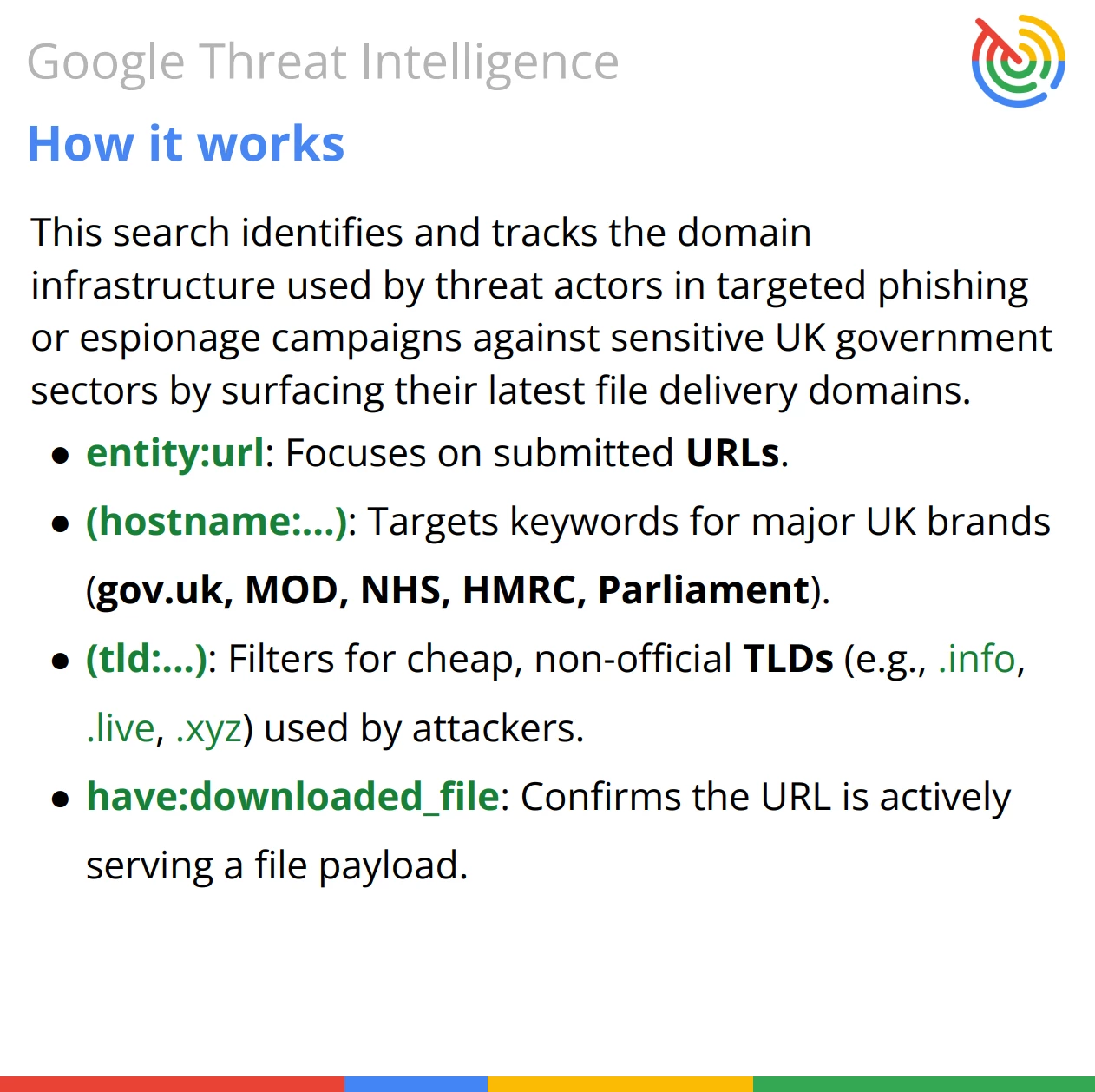
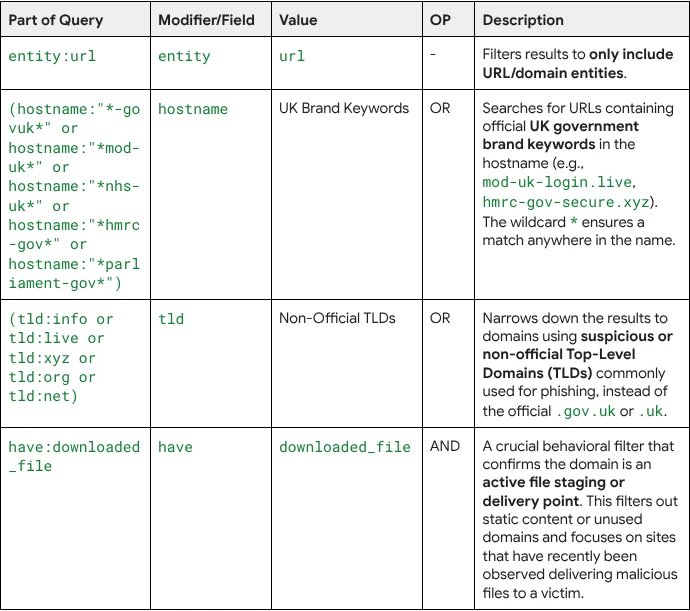
Query Breakdown: The query uses the entity:url filter to target domains and then applies a multi-part filter to catch typosquatting or brand impersonation combined with a high-confidence behavioral indicator.
Summary of Intent: The overall goal is to identify active phishing infrastructure that is impersonating key UK government services to deliver malware (espionage) or steal credentials.
The search effectively combines:
- Impersonation: Looking for the specific brand keywords (mod-uk, nhs-uk, hmrc-gov, etc.).
- Suspicious Infrastructure: Requiring the use of non-standard TLDs (.xyz, .live, etc.)—the classic typosquatting setup.
- Active Malice: Requiring confirmation (have:downloaded_file) that the URL has been recently used to distribute a malicious payload, confirming it is not just a parked domain but an active threat actor delivery mechanism.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


