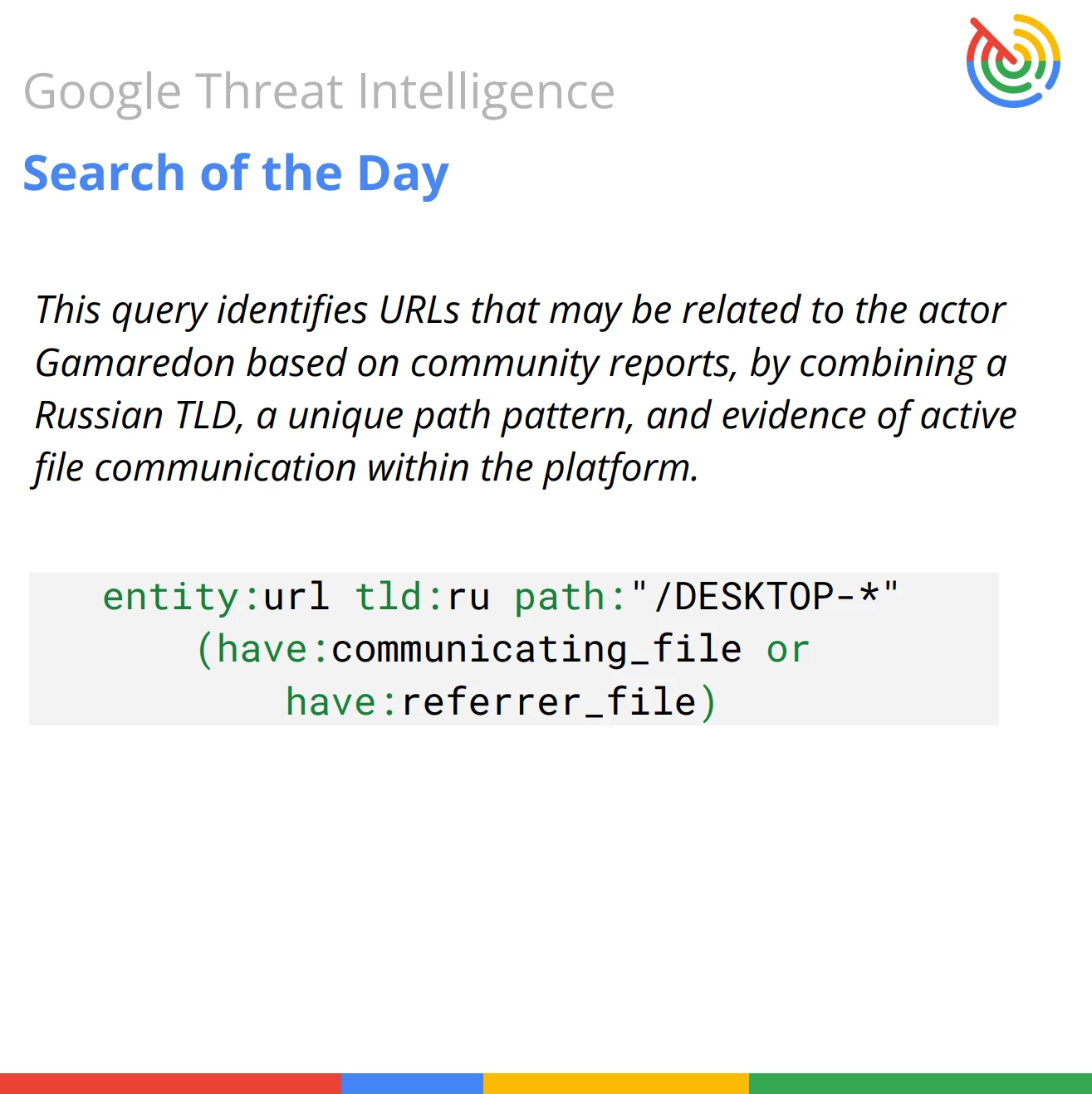


This query is designed to identify and block the Command and Control (C2) domains used by the Gamaredon (also known as Primitive Bear or UAC-0010) threat actor, a highly persistent group with reported ties to Russia, often targeting entities in Ukraine.
entity:url tld:ru path:"/DESKTOP-*" (have:communicating_file or have:referrer_file)
Query Breakdown: The query focuses on specific geographical and technical indicators tied to Gamaredon's C2 infrastructure, combined with a behavioral check to ensure the URL is actively malicious.
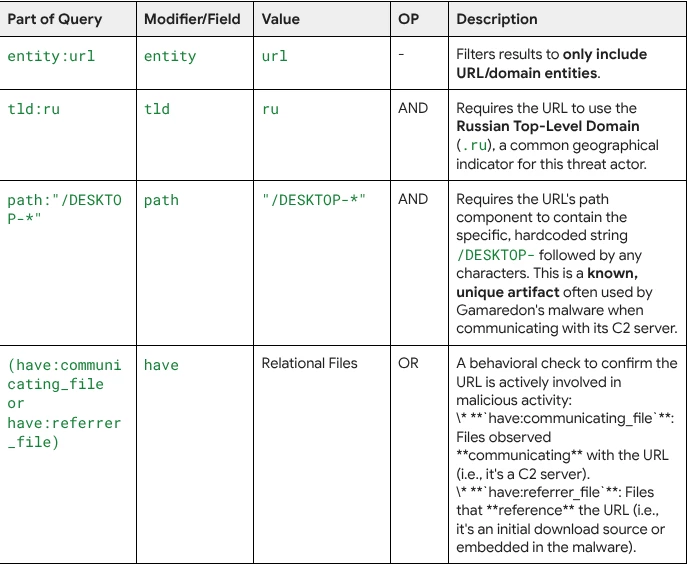
Summary of Intent: The overall goal is to use a combination of high-fidelity, hardcoded indicators to precisely identify active Gamaredon C2 infrastructure.
The search leverages:
- Geographical Indicator: Limiting the scope to .ru domains.
- High-Confidence Artifact: The specific /DESKTOP-* path structure is a strong, unique technical fingerprint of Gamaredon's C2 protocol.
- Active Malice Confirmation: The relational have:communicating_file or have:referrer_file ensures that the URL is currently an active C2 destination or file delivery point, rather than just an old or parked domain.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


