

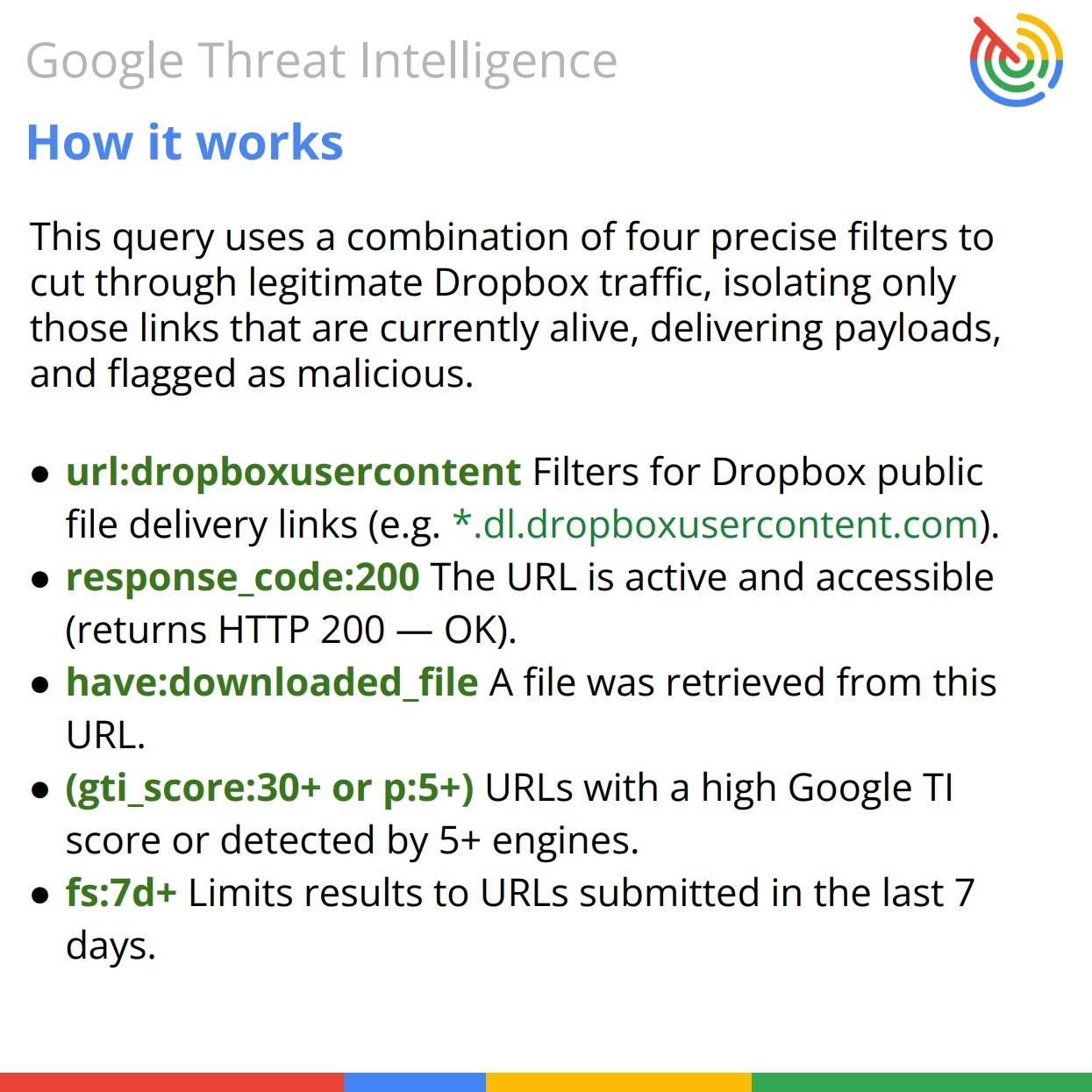
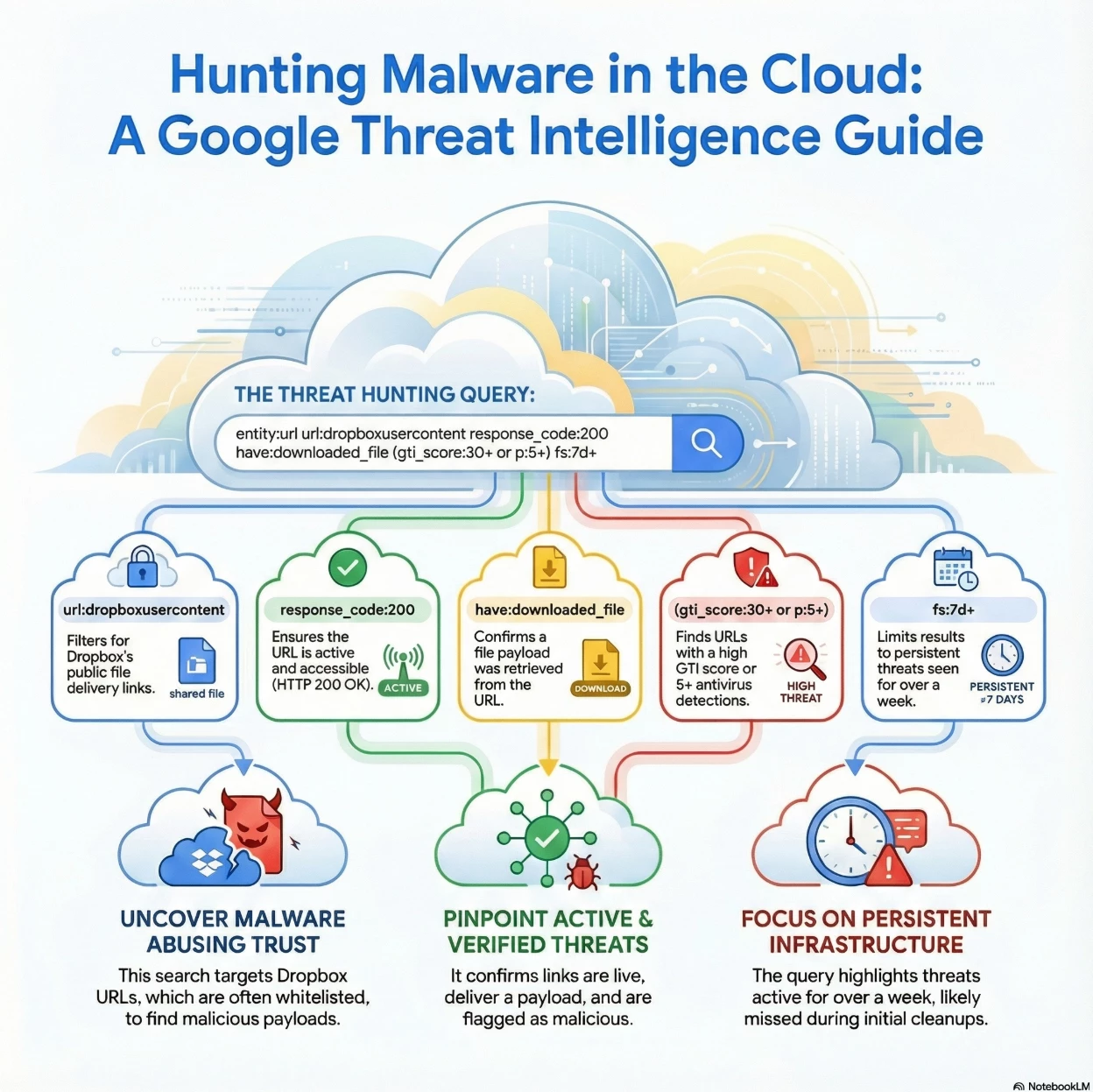
This Google Threat Intelligence search query is designed to identify currently active Dropbox URLs that directly download files and are already confirmed to be suspicious by multiple antivirus engines.
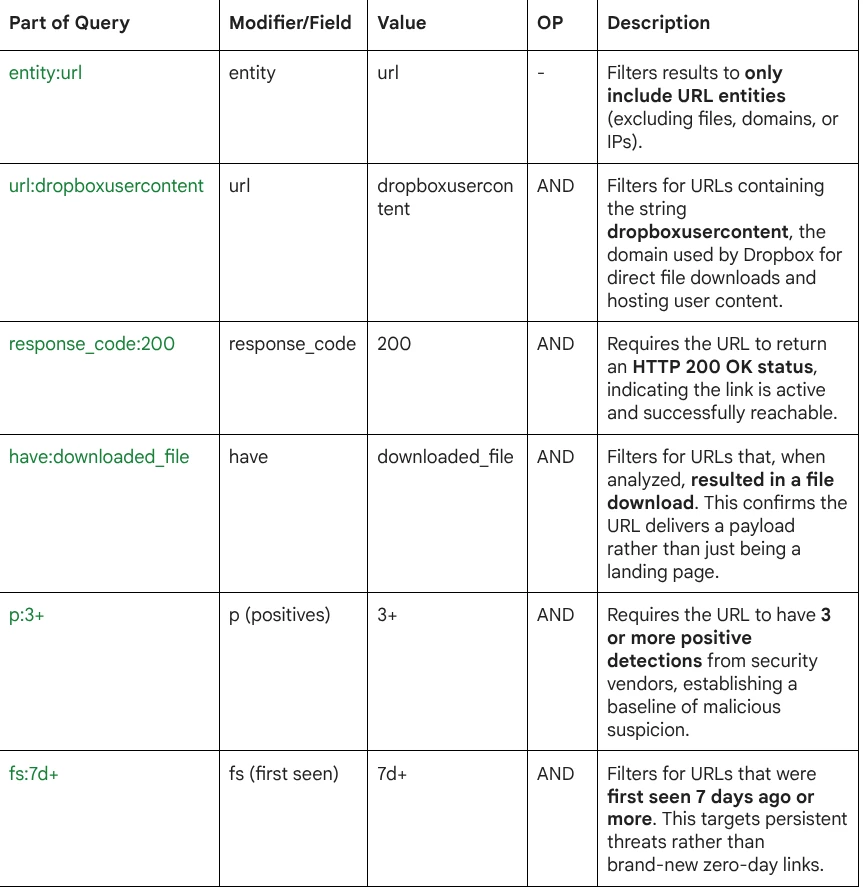
entity:url url:dropboxusercontent response_code:200 have:downloaded_file p:3+ fs:7d+
Query Breakdown: The query combines entity, URL pattern, and metadata modifiers to filter for high-confidence, persistent threats hosted on legitimate infrastructure.
Summary of Intent: The overall goal of this search is to detect malware abusing legitimate cloud storage (Dropbox) to evade network filters.
The search looks for:
- Abuse of Trust: It targets Dropbox URLs (url:dropboxusercontent), which are often whitelisted in corporate environments.
- Active Threats: It ensures the link is live (response_code:200) and delivers a payload (have:downloaded_file).
- Verified Maliciousness: It filters out benign files by requiring a consensus of at least 3 detections (p:3+).
- Persistence: By looking for items seen over a week ago (fs:7d+), it highlights infrastructure that has likely been missed during initial cleanup or is successfully evading takedowns.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the legendary and amazing


