
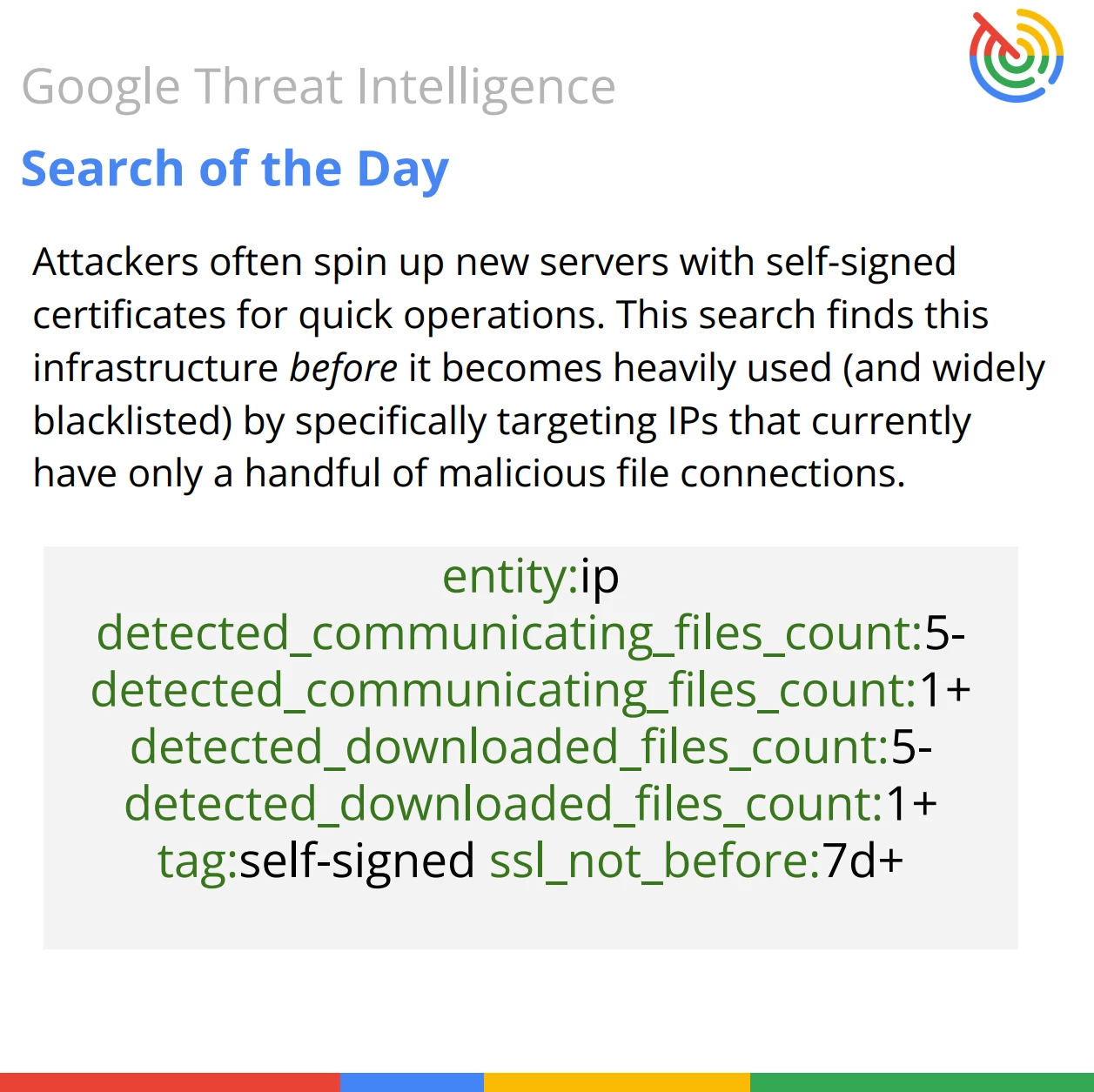
This VirusTotal Intelligence search query is designed to identify IP addresses acting as potential Command and Control (C2) servers. It specifically targets infrastructure that is serving or being contacted by a small number of malicious files and uses newly issued self-signed SSL certificates—a strong signal of newly deployed or low-profile C2 infrastructure.
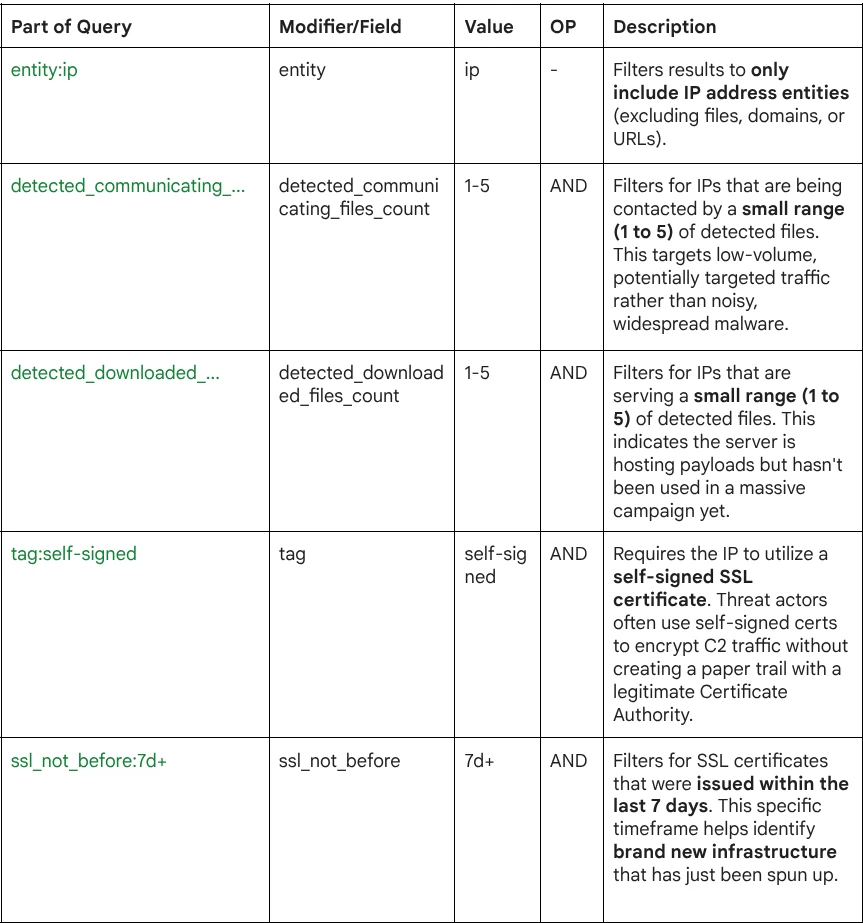
entity:ip detected_communicating_files_count:5- detected_communicating_files_count:1+ detected_downloaded_files_count:5- detected_downloaded_files_count:1+ tag:self-signed ssl_not_before:7d+
Query Breakdown: The query combines entity filters, file count statistics, and SSL certificate metadata to isolate fresh, low-volume threats.
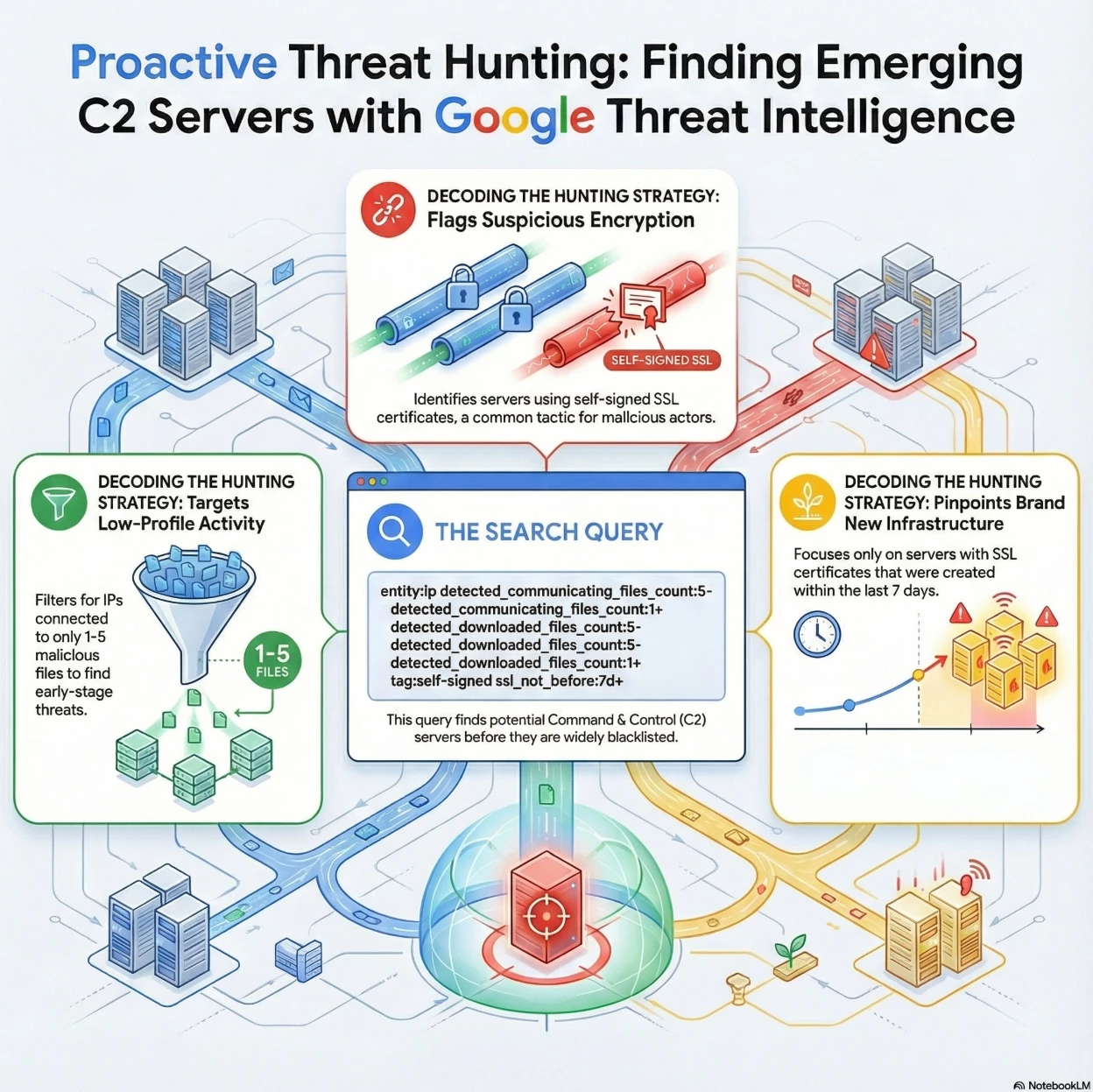
Summary of Intent: The overall goal of this search is to detect freshly minted C2 infrastructure before it becomes widely known.
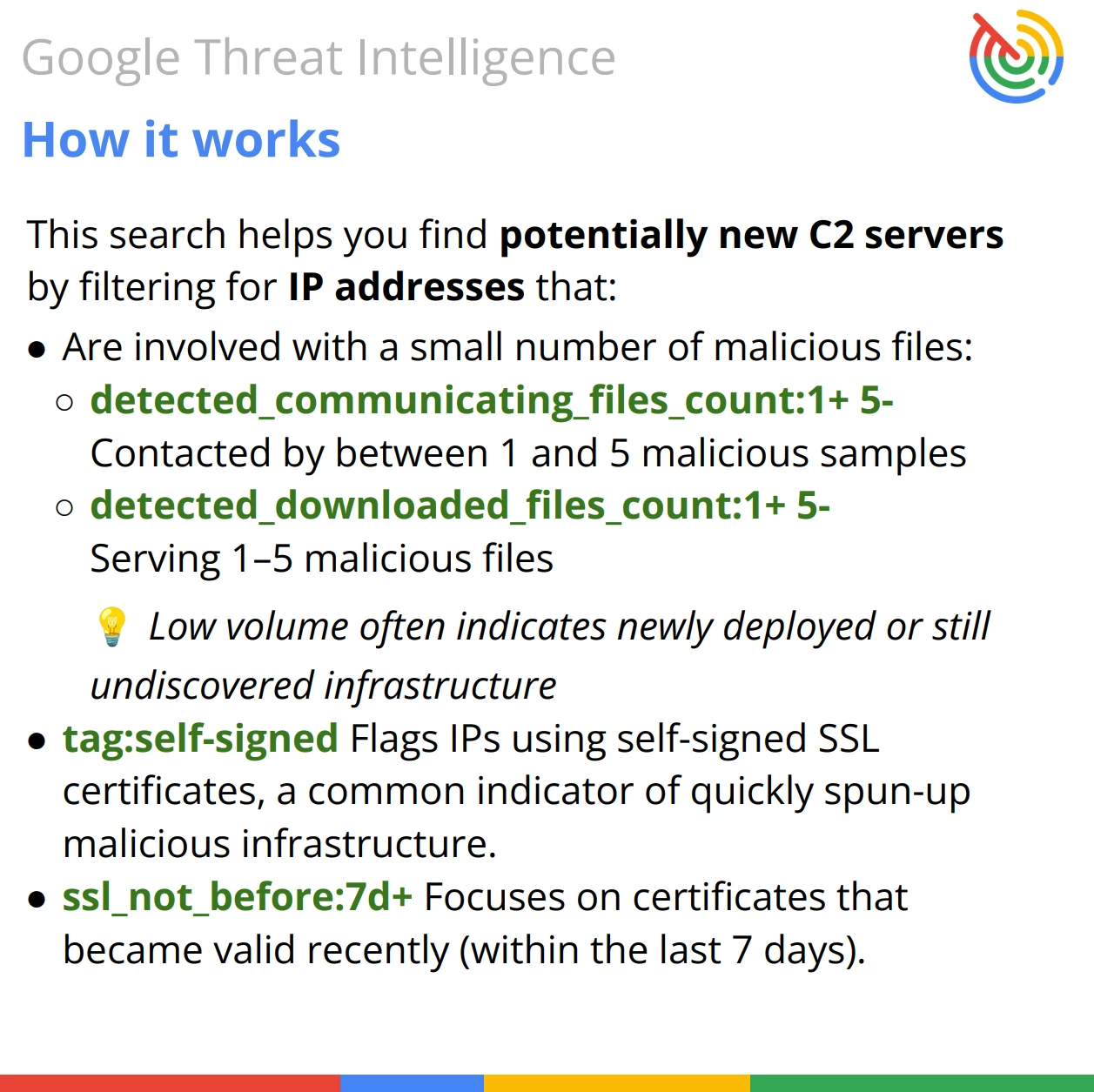
The search looks for:
- Entity Type: The target must be an IP address (entity:ip).
- Low Profile: It filters for a low number of associated files (between 1 and 5), avoiding "noisy" IPs that are likely already blocked and focusing on targeted or early-stage activity.
- Suspicious Encryption: It targets the use of self-signed certificates (tag:self-signed), a common tradecraft in C2 setups to avoid cost and attribution.
- Recency: It ensures the infrastructure is new by checking the certificate issuance date (ssl_not_before:7d+), catching the threat shortly after deployment.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


