Want to know which API we are using to fetch keys present for the below Query
for the below table under findings
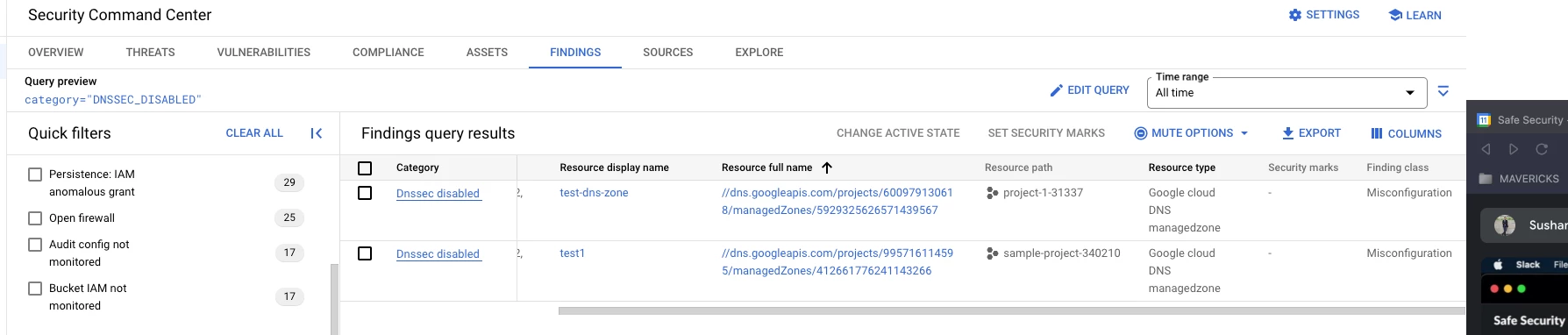
If i click on finding name i can see json response and in the json response there is one key "
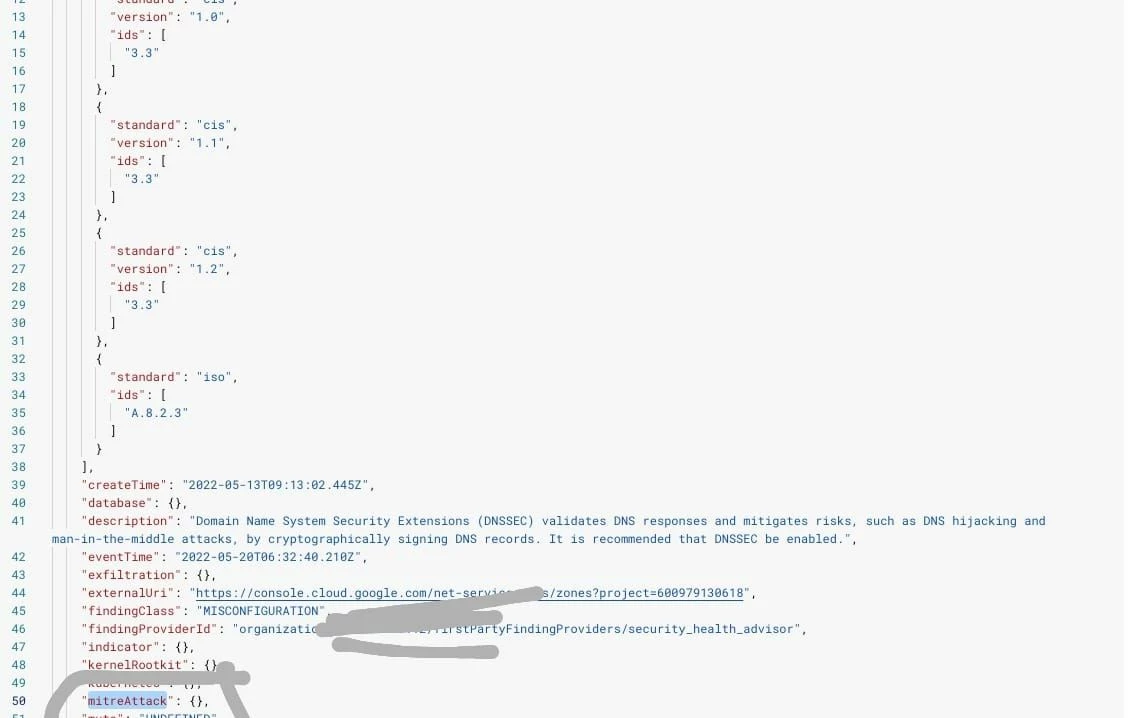
Query : In which API response i can get this key and how is response gets populated for this key



