Table of Contents
Ingestion
Configure Data Ingest
Data Ingest is the core of Google SecOps ingests raw log data, alerts, and other information. Ingested information is normalized and indexed for rapid search, then context enriched with data available from other ingested sources including threat intelligence feeds.
Configuring data ingest is the first step in preparing Google SecOps to correlate security events for your SecOps team. Google’s industry leading SecOps indexing, context enrichment, and search will enable your SecOps analysts to respond rapidly with a comprehensive view of threats and events.

Install & Configure Forwarders
Google SecOps SIEM forwarder is a software component that runs on a machine or device on your network, such as a server. Google SecOps SIEM forwarder can collect log data and network interface packets and forward that data to your Google SecOps SIEM instance.
Steps
- To add a new forwarder, users will select Settings in the left-side Navigation Bar and then select SIEM Settings, that will display the Settings page.
- In the Settings page, users will select Forwarders, that will display the page.
- Users can conduct search for Forwarders in the Search bar.
- Users also have the ability to Filter the list of Forwarders by selecting the Filter icon to the left of Create Forwarder.
- Users can add a new Forwarder by selecting Add New Forwarder.

- In the Forwarder Name field, can create a new Forwarder name.
- To further configure, users will expand the Configuration Values section and specify any of the following:
- Upload compression
- Asset namespace
- Label key
- Label value
- Filter description
- Regular expression
- Filter behavior
- Optional: Toggle Server Settings to configure the forwarder's built-in HTTP server, which can be used to configure load balancing and high availability options for syslog collection on Linux.
- Click Submit.
Relevant Documentation Links

Parsers
Google SecOps SIEM forwarder is a software component that runs on a machine or device on your network, such as a server. Google SecOps SIEM forwarder can collect log data and network interface packets and forward that data to your Google SecOps SIEM instance.
Steps
- To add a new Parser, users will select Settings in the left-side Navigation Bar and then select SIEM Settings, that will display the Settings page.
- In the Settings page, users will select Parsers, that will display the Parsers page.
- Users can conduct search for Log Types in the Search bar or from the Log Source list.
- Users also have the ability to Filter the list of Parsers by selecting the Filter icon to the left of Create Parser.
- Users can add a new Parser by selecting Create Parser.

- Users will see a Create New Custom Parser popup.
- On the Create New Custom Parser popup, users will enter a new Log Source in the Select the Log Source field.
- To further configure a new Custom Parser, users will write a new Code in the Parser Code Terminal for the Parser, and then select Validate by selecting the Validate button.
- Users can see the UDM Output in the UDM Output Preview box, to the right of the UDM Output text box, by selecting the Preview button.
- If the UDM Output is correct and final, users will select Validate to create the Parser.
- The validation process may take a few minutes, so we recommend that you preview the Custom Parser first, make changes if required, and then validate the Custom Parser.
- Click Submit.
- The Parser is picked for normalization after 20 minutes.
Relevant Documentation Links

Create and Manage Feeds
Google SecOps allows to users to create, manage, and troubleshoot feeds using the feed management UI. Managing the feeds includes modifying, enabling, and deleting the feeds. Each data feed has its own set of prerequisites that must be completed prior to setting up the feed in Google SecOps.
Steps
- To add a feed to your Google SecOps account, complete the following steps. Users can add up to five feeds for each log type.
- From the Google SecOps menu, select Settings, SIEM Settings, and then click Feeds. The data feeds listed on this page include all the feeds that Google has configured for your account in addition to the feeds that you have configured.
- Click Add New. The Add Feed window is displayed.

- Add a feed name, by searching the Source type list, select the source type through which users intend to bring data into Google SecOps. Users can select from the following feed source types:
- Amazon Data Firehose
- Amazon S3
- Amazon SQS
- Google Cloud Pub/Sub
- Google Cloud Storage
- HTTP(S) Files (non-API)
- Microsoft Azure Blob Storage
- Third party API
- Webhook
- In the Log Type list, select the log type corresponding to the logs that the user wants to ingest. The logs available vary depending on which source type you selected previously.
- Click Next.
- Review the user’s new feed configuration from the Finalize tab. Click Submit when you are ready. Google SecOps completes a validation check of the new feed. If the feed passes the check, a name is generated for the feed, it is submitted to Google SecOps, and Google SecOps begins to attempt to fetch data.
Relevant Documentation Links

Connectors
Google SecOps SOAR uses connectors to ingest alerts from a variety of data sources into the platform. A connector is one of the items in an integration package which can be downloaded through the Google SecOps Marketplace.
Prerequisites
- Users will need to download an Integration that has a Connector in Marketplace.
Steps
- To add a new Connector, users will select Settings in the left-side Navigation Bar and then select SOAR Settings, which will display the Settings page.
- In the Settings page, users will select Ingestion dropdown menu and select Connectors in the dropdown menu.
- A Connectors popup page will appear, which will display a Search field to select from options for Connectors.
- Users can also select the Create New Connector button
 at the top-right of the Connectors popup page.
at the top-right of the Connectors popup page. - An Add Connector popup page will appear, where users can select a from a Connector list in a dropdown menu.
- The option to select a Remote Connector can be selected by clicking the Remote Connector checkbox.
- If no Agents are configured, users can select Install Agent in the Add Connector popup.
- Users will then select Create.
- A New Connector Configuration page will appear.
- In this page, users will be able to configure a New Connector with three tabs, consisting of the following input pages:
- A New Connector Configuration page will appear.
- In this page, users will be able to configure a New Connector with three tabs, consisting of the following input pages:
- When complete, users will select Save.
- If users need to add a Domain, they will navigate to the Settings > SOAR Settings > Environments > Domains.
- Users will click the Add button on the top right of the Domains page.
- Enter the Domain and Environment into the Add Domain popup .
- When complete users will select Add.
- When complete, users will select Save.
- If users need to add a Domain, they will navigate to the Settings > SOAR Settings > Environments > Domains.
- Users will click the Add button on the top right of the Domains page.
- Enter the Domain and Environment into the Add Domain popup .
- When complete users will select Add.
- Name
- CIDR Format
- Priority level
- Environment
- When complete users will select Add.
Relevant Documentation Links
- [All Steps] https://cloud.google.com/chronicle/docs/soar/marketplace-integrations/google-chronicle#chronicle-alerts-connector
- [Additional Steps]
https://cloud.google.com/chronicle/docs/soar/admin-tasks/configuration/define-domains-for-mssps
https://cloud.google.com/chronicle/docs/soar/admin-tasks/configuration/manage-networks
Utilize SecOps Marketplace
The Google SecOps Marketplace offers a central hub where you can access a wealth of pre-built integrations, community-developed playbooks, and powerful analytics – all designed to streamline your Security Operations Center (SOC) workflows and supercharge your incident response.
The Marketplace empowers you to seamlessly connect Google SecOps with leading security tools, automate repetitive tasks with pre-built playbooks, and gain invaluable insights from comprehensive dashboards. This collaborative environment fosters innovation, saves valuable time, and allows your SOC team to focus on what matters most – effectively combating cyber threats.
Prerequisites
- Entitlement for Google SecOps on the account and project.
- Administrative access to Google SecOps.
- Administrative access for any 3rd party applications that are intended to be connected to Google SecOps

Marketplace Use-Cases
The Google SecOps Marketplace acts as the customer's toolbox, holding a wide range of utilities and options to choose from. The Marketplace also contains a repository for predefined Use Cases, Power Ups that enhance Playbook capabilities, and Analytics that provide valuable insights.
Steps
- To begin, users will go to the left-side Navigation Bar and then select Marketplace, which will display the Google SecOps Marketplace page.
- Users will also see three tabs to select from, consisting of:
- Use Cases
- Integrations
- Power Ups
- Users will select the Use Cases tab, which will display many pre-defined Use Cases at the bottom of the page.
- In the Marketplace page, users will see a Search bar at the top-right of the page, to Search for Use Cases.
- Users will have the option to Filter the category types of Use Cases they want to display at the center of the page.
- These categories consist of:
- Malware
- Endpoint
- Threat Hunting
- Investigation
- Threat Intelligence
- Insider Threat
- …and more
- To the right of Filters is a Use Case Option menu, which will give the user a choice to:
- Create New Use Case
- Export Use Case
- Refresh
- For SCCE version of SecOps, Create New Use Case may not be available.
- A popup window will appear, which will display the Use Case with five steps:
- Use Case Information
- Use Case Items
- Install Use Case Items
- Configure Integrations
- Run Use Case
- Typically the Use Case Information section will display a video from Google SecOps that will give users a basic overview with and step-by-step instructions on how to install and run the Use Case.
- On the same page, users will see a description and three to four dropdowns that will display:
- Playbooks
- Integrations
- Test Cases
- Connectors
- Users will select Next.
- Users will see the Use Case Items page, that will show Install Use Case Items at the top of the page. Here users will be able to:
- Install Integrations
- Install Playbooks
- Install Simulation Cases
- Users will have a Search function in section and an option to Override existing Ontology.
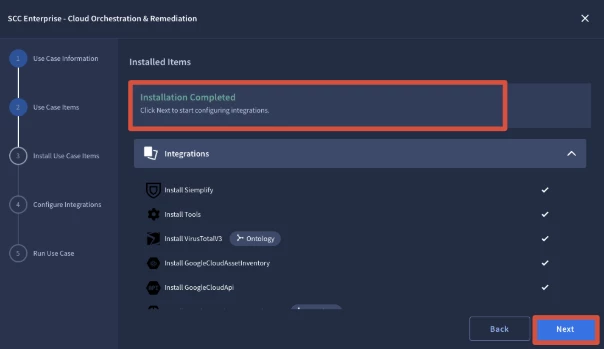
- Users will select Install to Install the Use Case items. Once the Installation is completed, it will display Installation Completed, with all of the Integrations, Playbooks, and Simulation Cases installed. Then select Next.
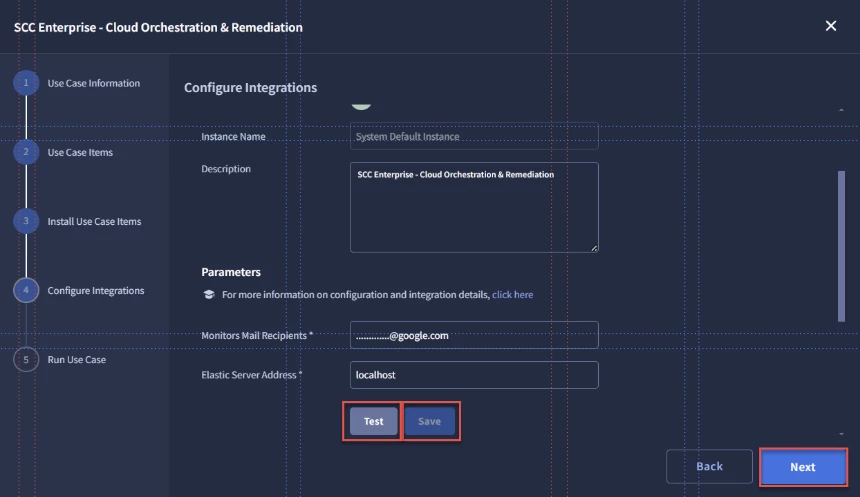
- Users will see the Configure Integrations page, listing all of the Integrations. Each Integration will have the following fields to Configure:
- Instance
- Environment
- Instance Name
- Description
- Parameters
- API Key
- Verify SSL
- Users will then have the option to Test and Save each Integration.
- When complete, users will select Next.
- In the Run Use Case page, users will see an option to Select Alert for Simulation by selecting the checkbox next to the Use Case and select Next.
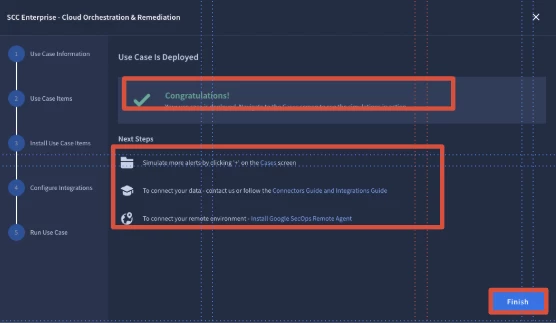
- Once selected users will see a Congratulations message and the Next Steps to:
- Simulate More Alerts
- To Connect Your Data
- Connect your Remote Environment
- Users will select Finish.
Relevant Documentation Links
Use Case Example
- Here is an example of how to install and configure the Use Case“SCC Enterprise - Cloud Orchestration & Remediation”:
- Users will select the Marketplace on the left Navigation Bar.
- Select Use Case tab on the Google Marketplace page.
- In the pre-defined Use Cases below, select from the Community-version “SCC Enterprise - Cloud Orchestration & Remediation” and click Install.
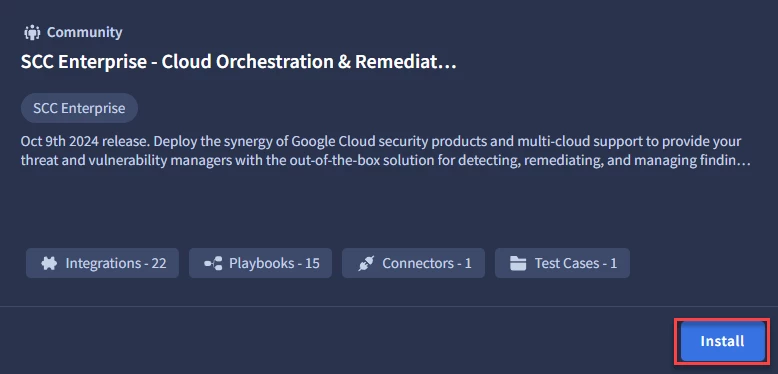
- Watch the Guide Video (If available) in the Use Case Information section, users will see the Playbooks, Integrations, Test Cases, and Connectors associated with the Use Case, and select Next.
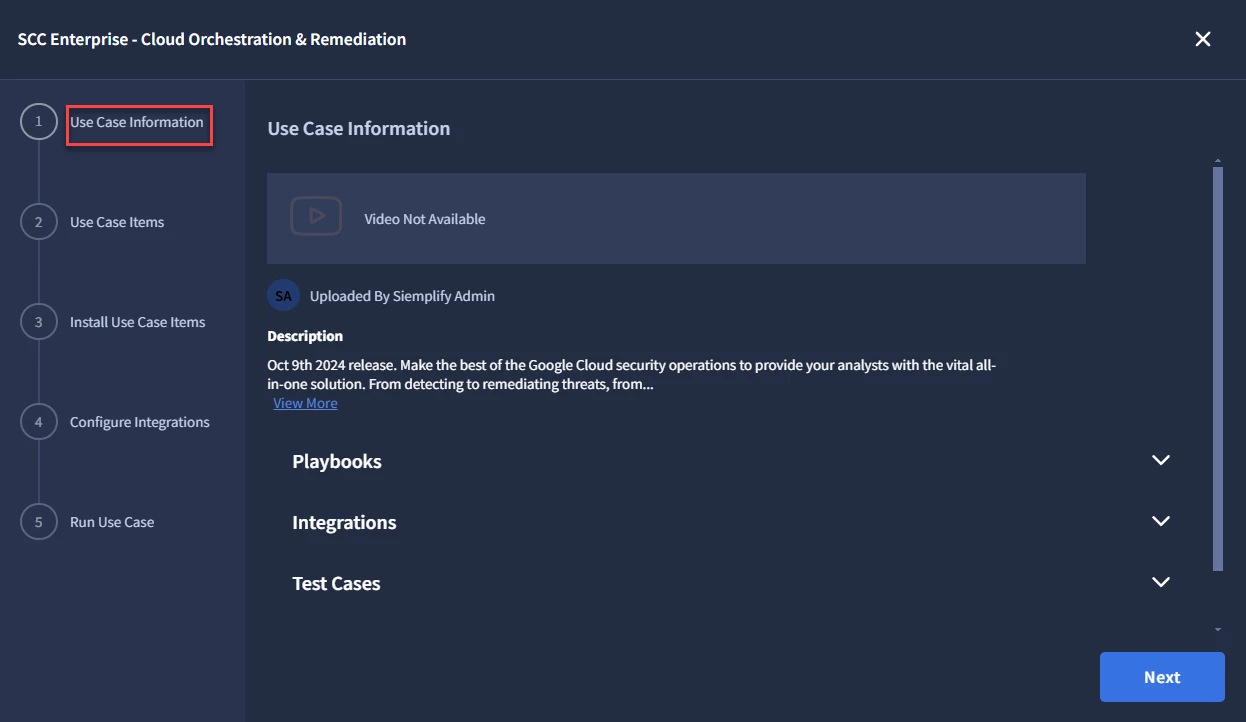
- In the Use Case Items section, users will see the Integrations, Playbooks, and Simulations Cases that will be Installed. If there is a conflict with an existing Ontology, and the user chooses to Override, they will select the box next to Override Existing Ontology. Once complete, users will then select Install.
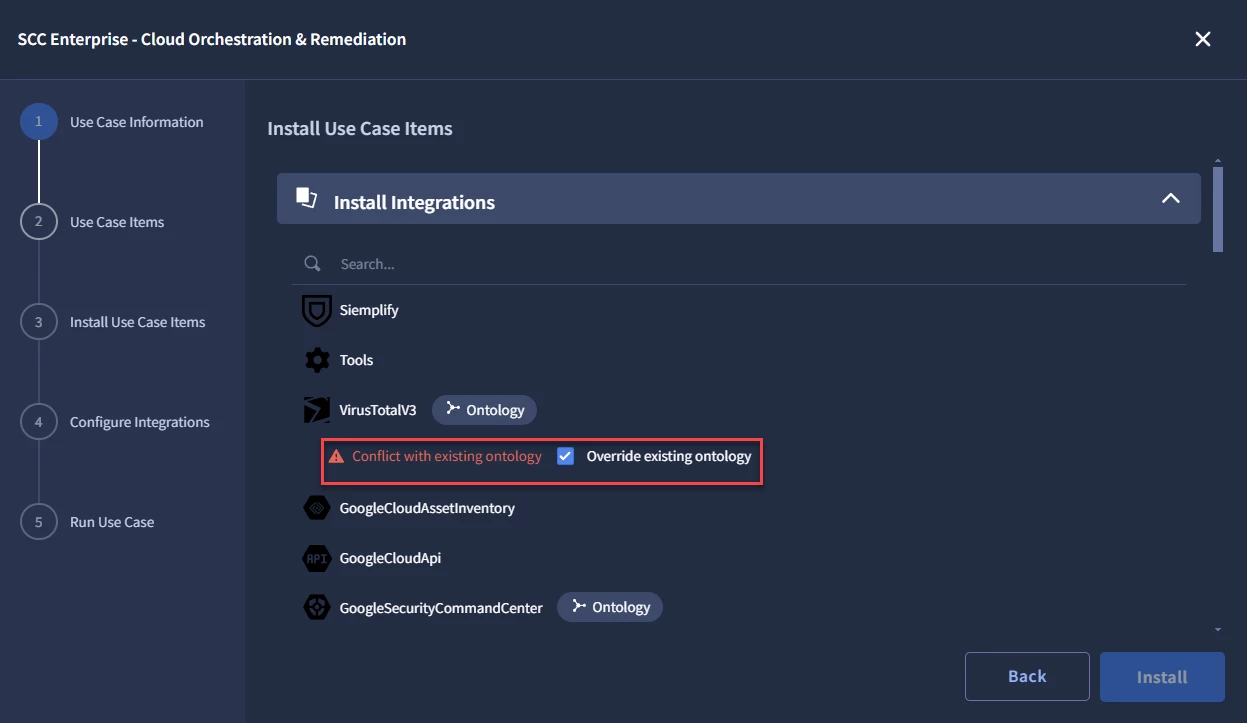
- Once Installed, users will see that their Installation is complete, and will select Next.
- Once users Configure their Integration, they can Test and Save the Configuration, then select Next.
- In the Run Use Case section, users will select the Alert for Simulation, by selecting the checkbox next to the Use Case, then select Next.

- In the final step, once the Use Case is deployed, users will see instructions on Next Steps and how to navigate to the Cases screen to see the simulations in action. Once done, select Finish.

Marketplace Integrations
The Google SecOps Marketplace acts as the customer's toolbox, holding a wide range of utilities and options to choose from. The Marketplace also contains a repository for predefined Use Cases, Power Ups that enhance Playbook capabilities, and Analytics that provide valuable insights.
Steps
- To begin users will go to the left-side Navigation Bar and then select Marketplace, that will display the Google SecOps Marketplace page.
- Users will also see three tabs to select from, consisting of:
- Use Cases
- Integrations
- Power Ups
- In the Marketplace page, users will see a Search bar at the top-right of the page, to Search for Integrations.
- Users will select Integrations, which will display many pre-defined Integrations at the bottom of the page.
- Users will have the option to Filter the category types of Integrations they want to display at the center of the page.

- These categories consist of:
- Security
- Threat Intelligence
- IT & Infrastructure
- Access Management
- IAM
- …and more
- At the top of the page are two dropdown menus:
- Type
- Status
- In the Type menu, users can select from the following Integrations:
- All Integrations
- Google SecOps Integrations
- Published by Community
- Custom Integrations
- In the Status menu, users can select Integrations that are:
- Installed
- Not Installed
- Available Upgrade
- Users can read the Details of each Integration by selecting the Details button.
Relevant Documentation Links
- [All Steps] https://cloud.google.com/chronicle/docs/soar/respond/integrations-setup/configure-integrations

Marketplace Power-Ups
The Google SecOps Marketplace acts as the customer's toolbox, holding a wide range of utilities and options to choose from. The Marketplace also contains a repository for predefined Use Cases, Power Ups that enhance Playbook capabilities, and Analytics that provide valuable insights.
Steps
- To begin users will go to the left-side Navigation Bar and then select Marketplace, that will display the Google SecOps Marketplace page.
- Users will also see three tabs to select from, consisting of:
- Use Cases
- Integrations
- Power Ups
- In the Marketplace page, users will see a Search bar at the top-right of the page, to Search for Power Ups.
- Users will select Power Ups, which will display many pre-defined Power Ups at the bottom of the page.
- Users will have the option to filter the list of Power Ups by selecting by Status, using the following options:
- Installed
- Not Installed
- Available Upgrade
- Users can read the Details of each Power Up by selecting the Details button.
Relevant Documentation Links
Next Step: Security Command Center Enterprise: Step 4.1.3 - Remediation | Google SecOps | Detection
Previous Step: Security Command Center Enterprise: Step 4.1.1 - Remediation | Google SecOps | Administration